
Blog | 7-minute Read
Identify, analyse and remediate: What is Microsoft 365 Defender?

Mathew Richards
Head of Secure Digital Transformation
Published: 26 August 2020
A ‘one-stop-shop’ for security incident management and remediation, here are the ins and outs of Microsoft 365 Defender’s top threat protection technologies.
Microsoft 365 Defender is much more than just “another security solution”.
It’s an entire suite of technologies working together to provide market-leading protection that can be accessed through a single portal.
These technologies include powerful identity and endpoint protection tools that defend your email and office collaboration apps and services.
Microsoft has been establishing itself as a major player in security and has announced it will be spending $20 billion over the next five years on cyber security.
There’s nowhere that this investment can be seen more clearly than in Microsoft 365 Defender.
Microsoft 365 Defender explained
Microsoft 365 Defender is mainly focused on user devices, e-mail, identity, and user data. It consolidates your view of security incidents across several technologies and adds a host of deep correlation and automation capabilities.
This makes the life of a security analyst more efficient and effective. Microsoft has been building the foundations for Microsoft 365 Defender for some time now. It’s done this by bringing all its security telemetry together in one place.
This foundation enables you to query a data set spanning multiple technologies.
I like to think of Microsoft 365 Defender as a collection of depth or specialist security tools – technologies that have a clearly defined focus within your environment.
Microsoft 365 Defender will help you run queries that can identify the following:
- Machines infected with a specific payload.
- Modified mailboxes.
- Malicious activity and the identities involved.
- Vulnerabilities caused by an exposed CVE.

The Ultimate Guide to Microsoft Security [New for 2024]
Cut through the complexity. Master Microsoft security.
What’s included in Microsoft 365 Defender?
Microsoft 365 Defender isn’t a single technology – it’s a collection of different technologies that work as one platform to deliver a high standard of protection.
Let’s look at the different parts of Microsoft 365 Defender to gain a better understanding of what it does.
Microsoft Defender for Endpoint
Defender for Endpoint is a specific technology solution for your endpoints. These include things like your mobile devices and tablets.
It manages your vulnerabilities, protects your endpoints, helps detect what your endpoints are, and puts it all under a single, unified platform.
Microsoft Defender for Office 365
Defender for Office 365 is a cloud-based email filtering service that protects your organisation against advanced threats to email and collaboration tools. This includes things like phishing attacks, compromised business emails, and malware.
Microsoft Defender for Identity
Formerly Azure Advanced Threat Protection, this is a cloud-based security solution that looks at your on-premises Active Directory signals to:
- Detect advanced threats
- Investigate advanced threats
- Identify compromised identities
- Identify malicious insider actions
Microsoft Defender for Cloud Apps
Defender for Cloud Apps is what’s known as a Cloud Access Security Broker (CASB). It has various deployment modes including log collection, API connectors, and reverse proxy.
It can provide your organisation visibility, control over data travel, and comprehensive analytics. These will let you identify and combat cyber threats across your Microsoft services and any third-party cloud services you use.
How does Microsoft 365 Defender work?
Microsoft 365 Defender combines the telemetry and insights drawn from the following products:
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Endpoint
- Microsoft Defender for Cloud Apps
- Azure AD Identity Protection
Microsoft 365 Defender brings these technologies together in one security operations console.
Within the console, you can see how Microsoft 365 Defender correlates insights from these technologies and applies relevant automated activities to address them.
Being able to mark an identity as compromised or perform actions against your endpoints allows you to apply a kind of ‘self-healing’ capability to affected entities.
These activities can then drive different behaviours when the user authenticates. This could mean blocking the user, enforcing multi-factor authentication (MFA), or directing the connection through a reverse proxy, for example.
Microsoft 365 Defender continuously monitors activity across a wide range of entities, using signals to surface incidents and highlight suspicious activities.
Aligned closely to the MITRE ATT&CK framework, Microsoft 365 Defender shows you where in the attack chain the activities contributing to the incident have occurred. These activities could highlight attack persistence, defence evasion, or lateral movement.
As you can see below, a security incident raised by Microsoft 365 Defender shows these tactics across the complete kill chain and provides supporting evidence.
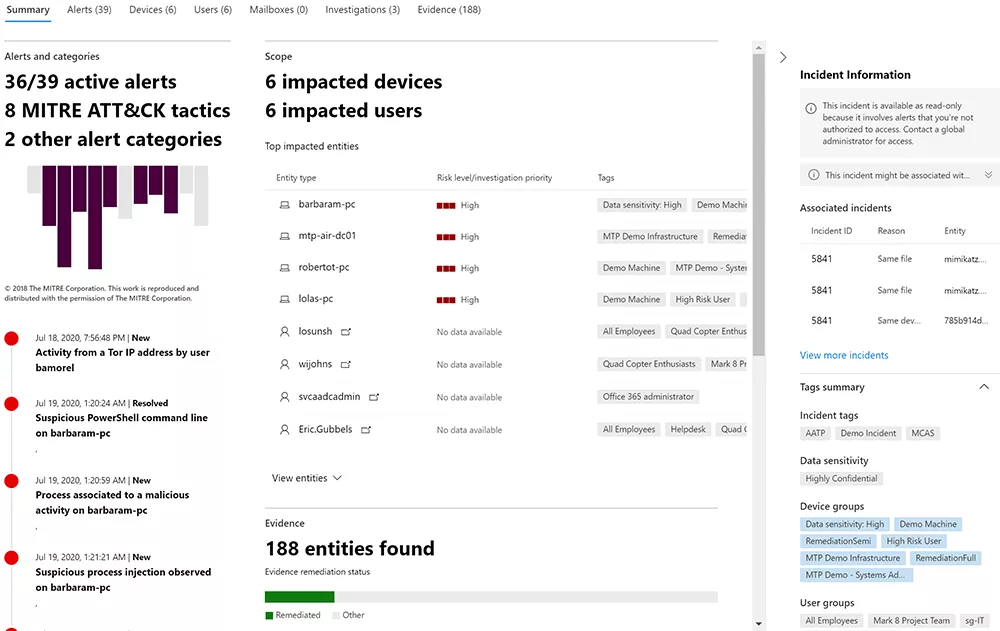
With this visibility, you can quickly establish the extent of the issue and get a handle on it. You can see all the affected entities such as mailboxes, identities, and devices, alongside their investigation priority.
You can also see any investigations that have been triggered automatically through the automated incident response (AIR) engine. AIR can execute automated investigations to further understand the details and potentially mitigate the risk.
These can be fully automated or based on an approval workflow.
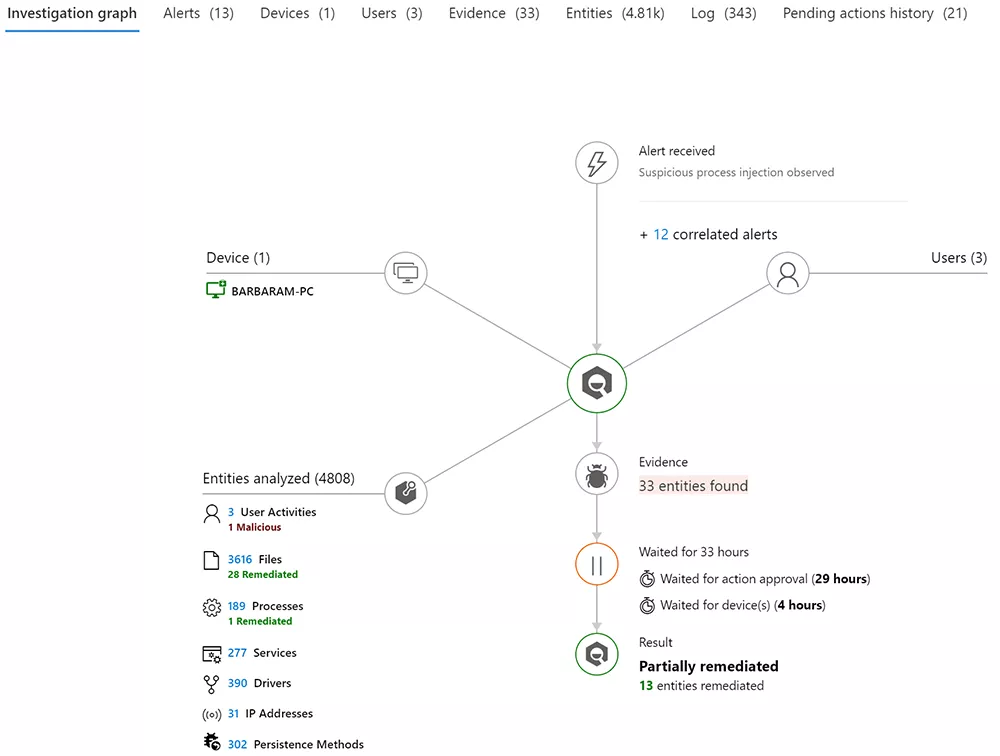
The insights provided by Microsoft 365 Defender will then flow into your overarching security incident and event management (SIEM) solution. Your SIEM can then perform further analysis and correlation across all the data consumed.
What’s new in Microsoft 365 Defender?
Microsoft has been regularly updating and improving 365 Defender. It’s worth taking a brief look at what new technology has been included since its initial release.
- Microsoft Defender Vulnerability management: This provides continuous vulnerability assessment, risk-based prioritisation, and threat remediation.
- Microsoft Defender Threat Intelligence: This maps the entire Internet to expose threat actors and their infrastructure. This gives you the intelligence you need to block attacks and keep your organisation safe from complex threats (e.g., ransomware).
- Microsoft Defender External Attack Surface Management: This gives your organisation an overview of your attack surface, so it’s simpler to discover vulnerabilities and block potential attack vectors.
- Microsoft Defender Experts for Hunting: This is a managed threat hunting service that can assist your Security Operations Centre (SOC) with continuous monitoring, analysis, and support. This allows you to identify and respond to critical threats unique to your environment.
Enabling extended detection and response (XDR) with Microsoft 365 Defender, Sentinel, and Defender for Cloud
As you would expect, Microsoft 365 Defender has native integration with Microsoft Sentinel (Microsoft’s SIEM and SOAR offering) – easily enabled by a simple tick box!
Using the insights of these specialist tools within Sentinel provides valuable insights to identify the end-to-end attack chain.
This helps you see what’s affected and where to focus your attention to mitigate the risk. It’s all about visibility.
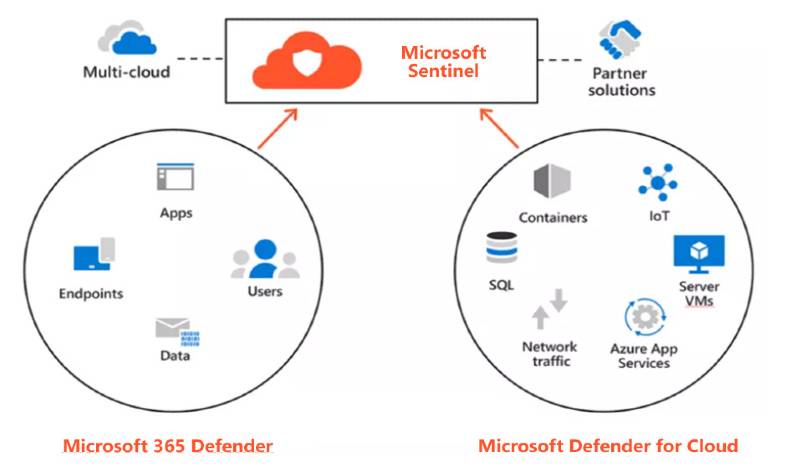
Without accurate, near-real-time visibility of activities across your entire environment, you’re at risk of harbouring bad actors who will be waiting for the perfect moment to strike.
An additional benefit of bringing these two powerful technologies together is the ability to enable a powerful extended detection and response (XDR) platform.
Combining Microsoft Sentinel’s world-beating, cloud-hosted incident management and the comprehensive security coverage of the Defender suite (particularly Defender for Cloud) creates an extremely powerful XDR platform.
Using cutting-edge AI and combining it with the power of the Cloud, Microsoft Sentinel and 365 Defender can give you the all-important visibility you need to identify threats to your organisation – and then respond to them rapidly.
Future-proof security management
Microsoft 365 Defender delivers a far more efficient and effective way of managing threat incidents within your organisation. It enables your analysts to quickly identify and remediate discovered threats.
Driven by the native integration of multiple technologies and backed with sophisticated machine learning models, Microsoft 365 Defender should form an essential part of your overall security strategy.
Microsoft’s goal with Microsoft 365 Defender is to make it the ‘one-stop-shop’ for managing threat protection. Whilst there has been a significant amount of work already completed to make this a reality, there is still more for Microsoft to do.
Today, you can see and interact with the incidents that have been raised and get visibility into the areas already discussed. On occasion, you will still need to enter the respective technology’s portal to gain a deeper understanding.
This is made easy for you from within Microsoft 365 Defender, but the eventual goal is to deliver everything you need in the Microsoft 365 Defender portal.
Microsoft has an ambitious roadmap planned, so expect to see many new capabilities being delivered across all of its threat protection technologies over the coming months.
Microsoft 365 Defender licensing
The Microsoft 365 Defender portal is available automatically if you have one or more of the technologies that comprise Microsoft 365 Defender.
You can access it if you have any of the following licences or products:
- Microsoft 365 E5 or A5
- Microsoft 365 E5 Security or A5 Security
- Windows 10 Enterprise E5 or A5
- Enterprise Mobility + Security E5 or A5
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365
If you have any of the above, then you’re good to get started. There will likely be some configuration required to ensure everything is working correctly, so do reach out to us if you need any help or support.
The Microsoft 365 Defender portal can be accessed here.
Conclusion
Now that you hopefully have a better understanding of Microsoft 365 Defender and its constituent parts, you can appreciate how Microsoft 365 Defender might benefit your security team. Attacks are becoming far more sophisticated and there is a real need to stay one step ahead.
The investment and commitment that Microsoft has made to security is impressive and, if anything, they’re gathering pace and continuing to innovate on the technologies they offer.
So, Microsoft 365 Defender is a worthwhile investment for managing your security as the threat landscape continues to evolve.
Key takeaways
Microsoft 365 Defender is your ‘one-stop-shop’ for managing threat protection.
It draws on all of Microsoft’s security technologies and telemetry.
Security incidents are clearly surfaced and highlight affected areas.
Microsoft 365 Defender allows for quick and effective threat response and mitigation.
It’s designed to integrate seamlessly with Microsoft Sentinel for additional detail and control.

The Ultimate Guide to Microsoft Security [New for 2024]
Grab your Microsoft security ‘cheat sheets’. Discover how to:
- Simplify security across your multi-cloud estate
- Easily protect identities, devices, and data

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great security & compliance resources






















Got a question? Need more information?
Our expert team is here to help.






