What We Do
Cloud Security solutions

























Moving your business into the cloud unlocks unlimited potential for growth. But this can all be undone by a poor cloud security posture.
Without the right protection, your network provides an open door for ransomware, phishing attacks, compromised users, rogue applications, and high-risk usage.
Leaving your business vulnerable to devastating financial losses, fewer customers, a ruined reputation, and crippling legal repercussions.
With our cloud security solutions, we provide the peace of mind to help your business flourish. Helping you:
-
Keep your data secure and protected across your cloud environment.
-
Stay protected from cyber threats, unusual behaviour, and compromised users.
-
Meet your regulatory and compliance obligations with ease.
Organisations who suffered data breaches from cloud misconfigurations.
Companies who've experienced at least one cloud security incident in the past year.
Companies who report better cloud security led to faster application and feature deployments.
Feeling lost in the clouds?
We know managing your cloud environment, and cloud-based apps, can be a challenge.
Poor visibility
Do you lack insight and a clear view of your current cloud security posture? Unsure where you’re vulnerable?
Threat detection
Concerned that attacks are being missed, or misconfigurations are going unchecked?
Data breaches
What measures have you applied to stop data from falling into the wrong hands? How is data transferred, viewed, and shared?
Application risks
Are you at risk of compromise or attack from third-party applications? How are you protecting your network?
Compliance challenges
Can you easily locate and secure your cloud-based data? Or are you risking non-compliance penalties?
Shadow IT
Are you at risk from unauthorised app usage? How can you stay aware of all apps in use across your organisation?
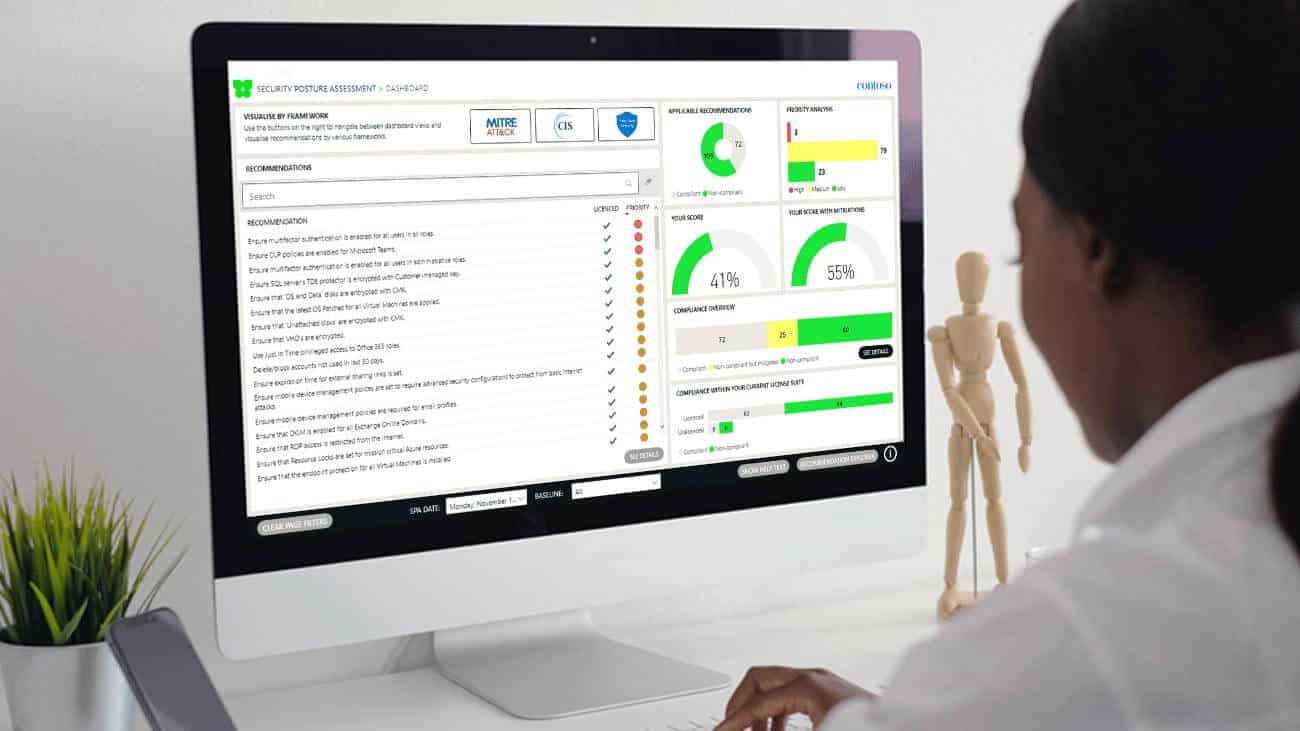
Watch 3-minute Security Posture Assessment Demo
See for yourself how a Security Posture Assessment helps you:
- Improve visibility of security threats
- Prioritise threats based on risk and effort
- Track improvements and measure ROI
- Stop wasting money with smarter investments
We apply industry-leading Microsoft technology to help your business meet its security and compliance requirements. Providing unrivalled protection, visibility and peace of mind.
Get more clarity and control over your cloud security
Our expert team can provide everything you need to protect your data, maximise security, and stay ahead of compliance challenges.
While allowing your team to work and collaborate to maximum effect.
We can help you:
Improve security posture
Identify and rectify vulnerabilities and misconfigurations.
Protect sensitive data
Classify and protect sensitive data across your cloud environment.
Detect sophisticated attacks
Detect and protect against cyber attacks and malicious activity.
Manage all apps
Apply automated processes for real-time control of your cloud apps.
Meet compliance obligations
Ensure you meet regulatory requirements and industry standards
Improve visibility
Simplify cloud security management by bringing all data into a single view.
As a trusted Microsoft partner, we help you take advantage of world-leading security solutions that keep your cloud activity protected, compliant, and running at optimum efficiency.

Mat Richards
Head of Security, Kocho
Comprehensive cloud security solutions to keep your business safe
Our solutions include:
The Security Posture Assessment has helped us immensely to visualise what is important and prioritise accordingly. The result has been a continuous delivery of enhancements to our security.
Paul Mathanaraja
Head of Infrastructure

Want to enhance your security?

Case studies
Who we've helped




















Free Guide
In-house vs. outsourced security operations: Which is right for you?
62% of organisations say their security teams are understaffed.
Download your 35-page comparison guide to discover:
- The real cost of building an in-house SOC
- Key questions you must ask before investing
- Hidden risks that could catch your business out
Got a question? Need more information?
Our expert team is here to help.







