What we do
eXtended Detection and Response (XDR) solutions

























When it comes to security, the race is on to spot and stop threats, fast.
Cyber threats are constantly evolving, and a delayed response can be catastrophic.
Our XDR solutions empower you to swiftly pinpoint and prevent attacks across your entire IT infrastructure.
By integrating your security solutions and providing real-time information, we ensure that nothing goes unnoticed, reducing risks and safeguarding your organisation.
Our solutions can help you:
-
Lower risk with continuous threat monitoring and hunting.
-
Respond rapidly with automated incident alerts and meaningful insights.
-
Save money by consolidating security into a single suite.
-
Stay compliant with industry regulations.
Be prepared – it’s not ‘if’, it’s ‘when’…
A core tenet of zero trust security is to assume you’ve already been breached. You need to be able to spot suspicious behaviour quickly. The longer it goes undetected, the more damage can be done.
Costing you money, harming your reputation, and putting you at risk of compliance penalties.
Your challenges:
Too many alerts
You get so many alerts of potential threats, it’s hard to know how to prioritise amidst the deluge.
Keeping up to date
With criminals devising new ways to penetrate your business, it’s hard to keep on top of emerging threats.
Lacking expertise
You don’t have the time or resource to develop specialist cyber security skills in-house.
Protection
Security breaches are expensive, cause operational disruption, and put your assets at risk.
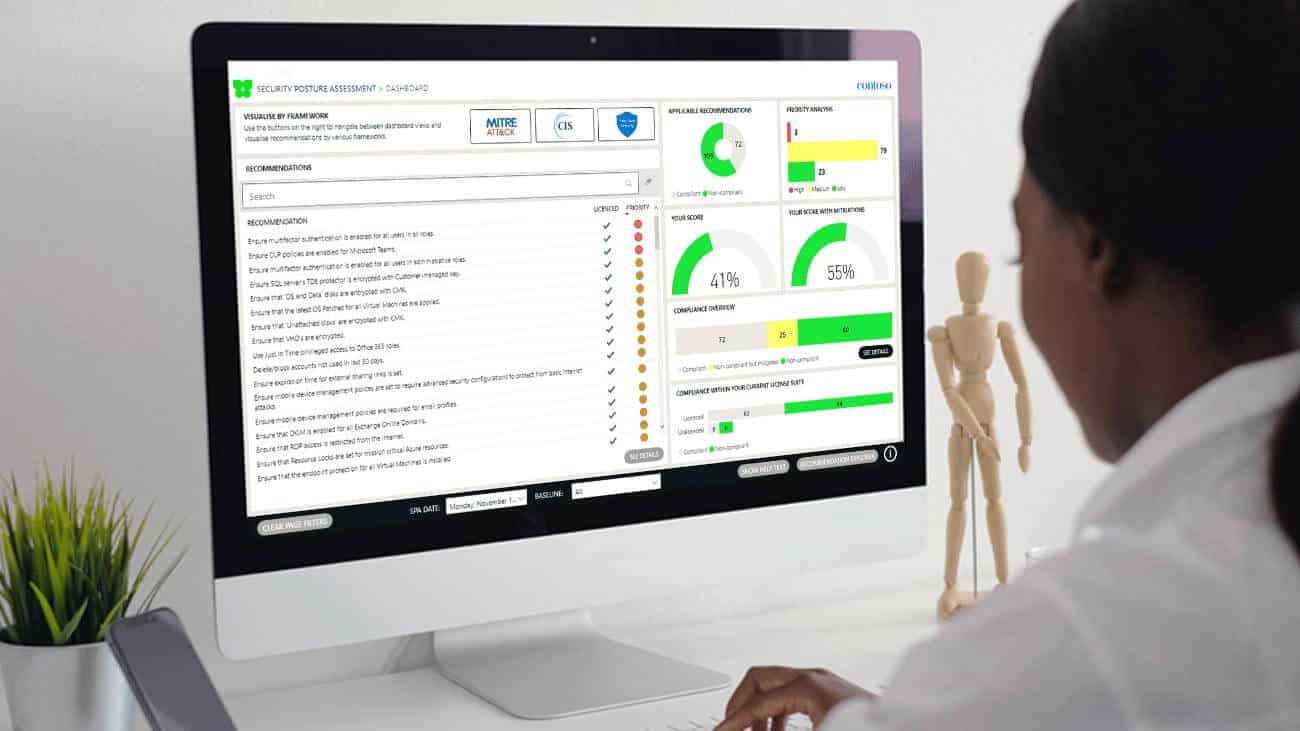
Watch 3-minute Security Posture Assessment Demo
Identify hidden threats and prioritise security risks.
The average attacker spends 56 days inside a victim’s network before they are detected.
FireEye M-Trends 2020
Safeguard the security of your organisation with XDR
Get the visibility and context you need to defend your organisation – and take your security operations to the next level.
You’ll benefit from:
Lower risk
Lower risk with continuous threat monitoring and hunting, generating a clear view of security data.
Rapid response
Respond rapidly with automated incident alerts and meaningful insights. Focus on the threats that matter.
Cost savings
Save money by removing expensive point solutions and consolidating your security into a single suite.
Compliance
Stay compliant and avoid hefty fines and reputational damage. Maintain compliance with industry regulations.
A comprehensive XDR solution to give your security some stopping power
Our solutions take care of:

Featured technology
Microsoft Sentinel + Microsoft Defender = A perfect security combo
Our service is built using Microsoft Sentinel and the Microsoft Defender suite.
Combining the market-leading cloud-hosted incident management and orchestration powers of Microsoft Sentinel and the extensive security coverage of the Defender suite makes for a potent XDR solution.
Combining cutting-edge AI with the power of the Cloud, Microsoft Sentinel and Defender provide the crucial visibility you need to identify the real threats – then respond and shut them down at speed.
The Security Posture Assessment has helped us immensely to visualise what is important and prioritise accordingly. The result has been a continuous delivery of enhancements to our security.
Paul Mathanarajah
Head of Infrastructure

Want to enhance your security?

Case studies
Who we've helped

Microsoft security suite pays dividends for a UK asset management company’s security posture

Validating a leading healthcare provider’s security posture





























In-house vs. outsourced security operations: Which is right for you?
Download your 35-page guide to discover:
- Costs and risks to build inhouse
- Potential security benefits and savings

Don't Miss
Great detection & response resources

Achieving XDR: How to make your SIEM SOAR
Learn how a modern SOC based on the latest Microsoft Defender and Sentinel technologies can help you see and stop threats across your entire cloud and hybrid estate before they can do damage.

Supercharge your security operations with SIEM and XDR

The ultimate guide to Microsoft Enterprise Security

Microsoft Sentinel vs. Splunk: Which is better?
Got a question? Need more information?
Our expert team is here to help.

