What We Do
Mobile Threat Defence solutions

























Comprehensive mobile security for your organisation.
Mobile devices are increasingly becoming a critical component of every organisation’s business operations.
However, as the usage of mobile devices continues to rise, so do mobile security risks.
Kocho's solutions use cutting-edge technology and allow you to:
-
Provide comprehensive protection for all mobile devices.
-
Utilise Microsoft Intune and Microsoft Defender for Endpoint
-
Mitigate security risks for your organisation
Overcoming the challenges of mobile security
We understand the challenges you face when it comes to securing your mobile devices.
Evolving threat landscape
Staying ahead of the constantly evolving threat landscape requires vigilance and deployment of the latest technologies.
Productivity vs. security
Your organisation needs to strike the right balance between keeping your users safe, while giving them the right tools for productivity.
Regulatory compliance
Mobile endpoints don’t just represent a logistical and security risk, they also represent a potential compliance nightmare.
Diverse endpoints
It can be a security headache when using a variety of devices on a range of different operating systems.
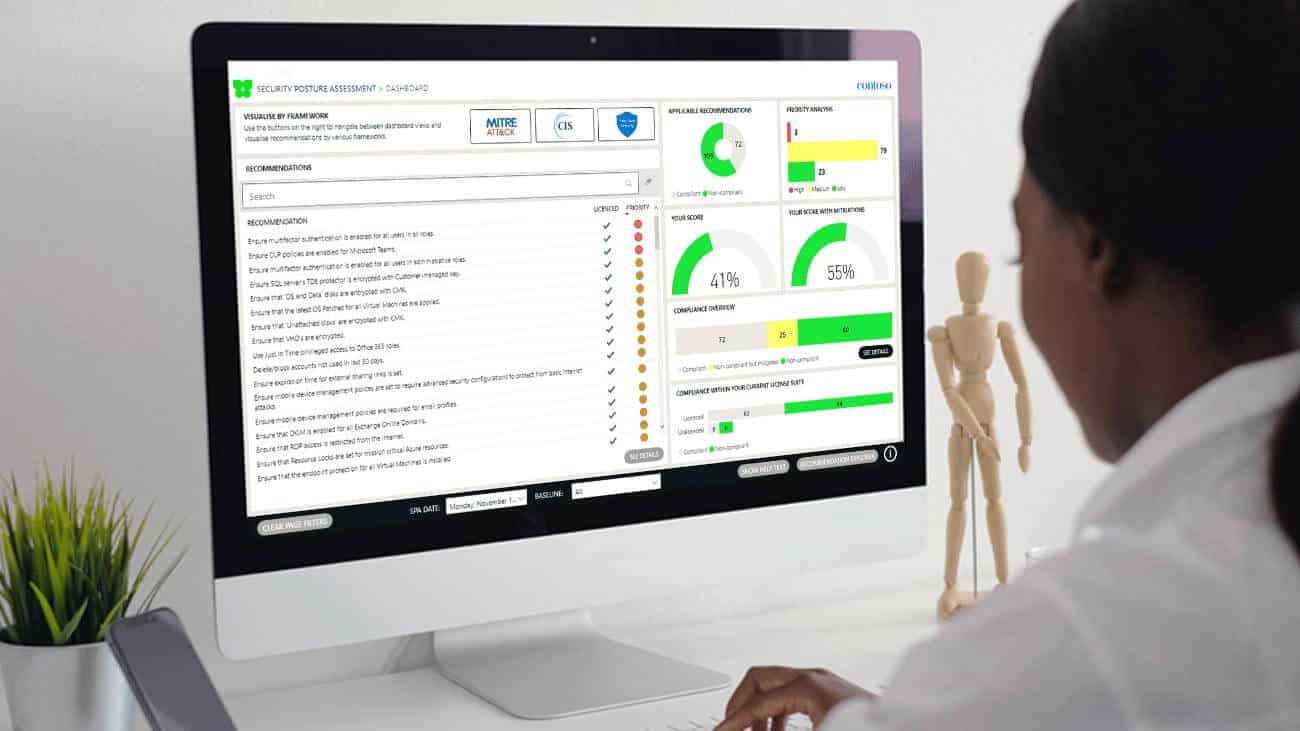
Watch 3-minute Security Posture Assessment Demo
Identify hidden threats and prioritise security risks.
60% of companies allow their employees to use personal mobile devices for work-related activities, but only 30% have implemented any kind of mobile threat defence solution
MobileIron Mobile Threat Defence Report
Protect your mobile devices with confidence
Our mobile threat Defence solution with Microsoft Intune and Microsoft Defender for Endpoint is tailored to meet your specific mobile security needs.
We can help you:
Rapidly respond to threats
Our mobile threat defence solution detects and responds to cyber threats in real-time to continually protect your devices
Protect your entire mobile estate
We offer complete protection for all types of mobile devices, including those running iOS, Android, Mac, and PC operating systems.
Integrate into existing security infrastructure
Our solution seamlessly integrates with your current security infrastructure to enhance your mobile security capabilities.
Meet compliance obligations
Our mobile threat defence ensures compliance with industry regulations, protecting your data and reputation.
More than 70% of mobile devices are not protected by basic security measures, making them vulnerable to cyber threats.
Verizon Mobile Security Index
Ready to boost your security?
Comprehensive mobile threat defence for your organisation
Our solutions include:

Featured technology
Microsoft Intune
Microsoft Intune is a cloud-based service that combines mobile device management (MDM) and mobile application management (MAM) capabilities.
With Intune, organisations can manage and secure their employees’ devices from a single console. Plus, it integrates with other Microsoft tools, including Defender for Endpoint and Azure AD, and supports various device types, from Android and iOS to Mac and PC.
The Security Posture Assessment has helped us immensely to visualise what is important and prioritise accordingly. The result has been a continuous delivery of enhancements to our security.
Paul Mathanarajah
Head of Infrastructure

Want to enhance your security?

Case studies
Who we've helped

Managing mobile devices with Intune at Sir George Monoux College

Large UK insurer improves endpoint security and compliance





























The Ultimate Guide to Microsoft Enterprise Security
Microsoft security simplified. Download your 40-page guide.

Don't Miss
Great threat defence resources

Supercharge your security operations with SIEM and XDR

In-house vs. outsourced security operations

Microsoft Defender for Cloud Apps Demo
Learn how Microsoft Defender for Cloud Apps can give you full visibility of your SaaS app landscape and safeguard the data in all your apps.

Better together: Why Unified Endpoint Management needs Mobile Threat Defence
Got a question? Need more information?
Our expert team is here to help.

