We review why Microsoft Sentinel soars above other SIEMs and delivers unparalleled security through AI, analytics and automation.
It’s essential that modern security operations centres (SOCs) have visibility across their entire cloud and on-premises infrastructure.
But this can be a challenge.
Analysts are confronted by unprecedented cyber threats. Yet their defences depend on wading through vast amounts of data and alerts from diverse and often siloed sources across increasingly wide and complex digital estates.
It’s a process that can be labour intensive and prone to error or missed incidents. Not only impacting analyst’s ability to effectively investigate, but seriously slowing down detection, response, and remediation.
When rapid action is called for.
These are the issues and common challenges directly addressed by Microsoft Sentinel.
In this article, we explore how Sentinel manages the overwhelming flow of alerts—sifting through the noise to highlight genuine threats and reducing the risk of oversight or errors.
We also examine how Sentinel sits at the heart of Microsoft’s vision for a unified extended detection and response (XDR) solution. Underscored by AI and automation to facilitate unsurpassed investigation and machine-speed responses to every incident.
Anywhere across the estate.
Microsoft Sentinel – What is it and what does it do?
Microsoft Sentinel is Microsoft’s cloud-native security information and event management (SIEM) AND security orchestration automated response (SOAR) solution all in one!
It brings together the latest in security innovation and advanced AI to provide near real-time intelligent security analytics for a bird’s-eye view over your entire enterprise’s IT estate.
With Sentinel you can consume security related data from almost any source – not just sources inside your Microsoft tenant! This removes the need to manage multiple pieces of complex and costly infrastructure components – whilst providing a cloud platform solution that can easily scale to your needs.
Sentinel uses machine learning and AI models to surface important insights based on data consumed through a wide catalogue of data connectors. This includes native connections to all key Microsoft sources, together with a range of native 3rd party connectors which includes technologies from AWS, Symantec, Barracuda, Cisco, and many others.
The solution analyses in excess of 6.5 trillion signals daily to provide unparalleled threat intelligence. This, coupled with the ability to filter millions of signals into meaningful dashboard alerts, provides comprehensive hunting and investigative capabilities – enabling you to expedite your response to potential attacks.
Sentinel also integrates with a wide range of systems – providing the option to automate your incident response activities, thereby allowing you to orchestrate your activities in an efficient and effective manner.
4 key security pillars
Put simply, Microsoft Sentinel enables you to:


Free Video
Microsoft Sentinel and Defender XDR Demos
Detect, investigate, and remediate threats across your entire network, with the power of AI.
See how you can:
- Make security and protection more efficient
- Utilise AI to power detection and remediation
- Protect endpoints, identities, and apps
How to enable Sentinel in your environment
Enabling Sentinel in your environment is simple, all you need is the following:
- An active Azure subscription.
- A Log Analytics workspace.
Once you have that, you can browse to Sentinel within the Azure portal to deploy – then you are ready to begin adding your data connectors.
You can enable Sentinel on new Azure Monitor Log Analytics workspaces and both data ingestion and Sentinel charges are waived for the first 31 days (up to 10GB of log data per day). It’s worth noting you are limited to a 20-workspace limit per Azure tenant, but it should be more than sufficient to get a feel for the platform.
For existing workspaces, only the Sentinel charges are waived during this 31-day trial. Also, any charges related to additional automation or bring-your-own machine learning still apply.
Currently, there are several Microsoft data connectors that are available out-of-the-box and these provide near real-time integration, including, Office 365, Azure AD, Microsoft 365 Defender and Defender for Cloud Apps.
Sentinel also provides over 100 out-of-the-box data connectors for non-Microsoft solutions, including AWS, Barracuda, Cisco, and Symantec. Sentinel additionally provides support for generic connectors allowing you to send data via Windows Firewall, Syslog, REST API, or common event format (CEF), enabling you to send information from any data source. So, it’s very flexible to your infrastructure.
Once your data connectors are enabled, Sentinel will begin analysing and reporting on potential threats within your environment using the built-in alert rules.
However, the real power of Microsoft Sentinel is the ability to write custom alert rules and automated playbooks to help detect and remediate threats in real-time. These custom alert rules and playbooks allow you to tailor Sentinel to protect your organisation against any specific threats it faces.
Microsoft Sentinel in action – A typical scenario…
In this example, an organisation’s Entra ID Connect instance has been compromised and their credentials have been exfiltrated. We will investigate this attack and highlight how Microsoft Sentinel could have been used to alert and mitigate this attack at different points of the cyber kill chain.
The cyber kill chain is a series of 8 steps that trace an attack from reconnaissance to data exploitation – enhancing our understanding of the timeline of a cyber-attack.
We will be focusing on the alerting and remediation response against reconnaissance, intrusion and exfiltration.
Why target Entra ID Connect?
For those unaware of Entra ID Connect, it’s a tool that allows organisations to connect their on-premises Active Directory with their Entra ID environment. The most common authentication configurations are via Password Hash Sync (PHS) or Pass Through Authentication (PTA).
Password Hash Sync operates by synchronising the hashed passwords that sits on Active Directory with Entra ID, allowing users to sign into cloud services using their on-premises credentials. Whereas Pass Through Authentication allows users to sign into cloud services using their on-premises credentials by forwarding authentication requests to an on-premises Active Directory server.
Both these configurations deal with the management of an organisation’s credentials, as such it is often a valuable target for attackers. Hence it is vital that the Entra ID Connect service, and the server it sits on is protected to prevent the compromise of credentials.
Reconnaissance
The first step of the cyber kill chain is reconnaissance. Research shows that up to 60% of an attacker’s time is spent investigating an organisation and their infrastructure before they begin their attack. So, while reconnaissance is not a threat nor is it an exploit. It is important to remember that reconnaissance is the first step on the path to a cyber attack. As such it is vital to respond to such threats when they occur.
The most common form of reconnaissance is the use of port scanning to fingerprint servers and identify what OS is in use and potentially what services are running. With this information, attackers will exploit known vulnerabilities or use a password spray attack to attempt to gain a foothold in the system.
Using Microsoft Sentinel, we can create a custom alert rule that will react when it detects potential port scanning and trigger a playbook to remediate the threat.
To respond to this alert, we can create an automated playbook which is built using the Logic Apps framework available in Azure. Logic Apps uses a simple drag and drop interface to build a series of tasks to execute.
The advantage of Logic Apps is they can be used to build complex workflows that would normally take up valuable time of an organisation’s IT personnel – thus reducing the amount of time spent on trivial, repetitive tasks.
Intrusion
An ever-growing form of intrusion that many organisations face, is the password spray attack. This is a type of attack where an attacker will attempt to gain access into a system using default or commonly used credentials.
Attackers are also increasingly using lists of the most common passwords to gain access to systems. According to the NCSC, over 75% of organisations had passwords that feature in the top 1,000 most commonly used passwords. So, it’s no surprise that password spray attacks are so commonplace.
Attackers are unlikely to attempt to sign into an account manually from their own IP address, instead they’ll attempt to automate the task using botnets. Hence when an alert is raised for an unusual sign-in, we can look up the IP address of the sign-in alert and check whether it came from a known botnet, block the user from signing in and raise a ticket in Service Now to notify IT personnel of a potential account breach.
While most workflows can be created using the basic building blocks providing in Logic Apps, a more complex workflow is sometimes required. In this case we can’t easily create a Logic App to compare the IP address of the alert against a list of known botnets. However, Logic Apps allows us to integrate with Functions Apps, which are small blocks of custom code that can be run. As a result, we can create Logic App that can perform more complex tasks.
Exfiltration
Once an attacker has gained initial access in a network, they will be looking for ways to extract data from a system. In our fictitious example, the attacker has gained access to a local administrator account and is now looking to export all the user credentials stored in the Active Directory.
As the attacker has breached the server which hosts the Entra ID Connect service, they can compromise the built-in service account which Entra ID Connect uses to perform its synchronisation, an attack method commonly referred to as DCSync. It impersonates a Domain Controller and can request password data from the target Domain Controller.
Now, Microsoft Defender for Identity has out-of-the-box detection for DCSync attacks. And thanks to Defender XDR and Sentinel providing a singular view across the estate, SOC teams have the capability to detect and respond at rapid speed.
Furthermore, as Sentinel collates alerts from all sources (Microsoft and non-Microsoft alike) across the estate, teams are able to add contextual information that can help the investigation process.
Looking ahead: A single solution for end-to-end protection
The power of Sentinel’s platform is a central component of Microsoft’s vision for unified security across the entire attack surface.
At the Ignite event at the end of 2023, Microsoft announced that they were bringing together the aligned power of Sentinel, Defender XDR (formerly Microsoft 365 Defender), and Microsoft Security Copilot.
Bringing these tools together means creating a full, unified SOC suite. Powered by AI and offering SOCs a single place to attain full visibility, investigation, and response across the entire estate including:
- Hybrid identities
- Email and collaboration tools
- Cloud apps
- Endpoints
- Data
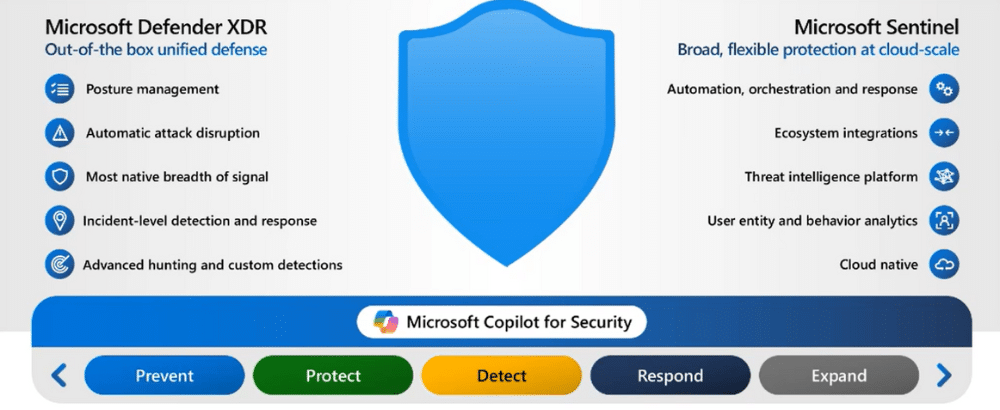
Furthermore, by adding Microsoft Security Copilot into the mix, add powerful generative AI that will speed up analysis and simplify processes (for example, translating natural language into KQL).
Like we said at the top, SOCs need visibility across the estate to deal with relentless threats across diverse digital ecosystems. But that also means having technology that can combat ever-evolving emerging cyber threats.
Unlocking the unified power of Sentinel, Defender XDR, and Microsoft Security Copilot, is Microsoft’s powerful solution to meet these demands.
Conclusion
Microsoft Sentinel is a powerful SIEM fit for the modern technological landscape. It provides a bird’s-eye view of your entire IT estate along with smart analytics supported by advanced artificial intelligence to help detect and respond to threats in near real-time.
As seen in the examples in this blog, Sentinel can integrate seamlessly with your pre-existing Microsoft and non-Microsoft infrastructure, while still providing you the control to customise Sentinel to match your security requirements.
This all contributes toward defending your organisation against the ever-growing cyber security threats of this modern world. Microsoft Sentinel’s use of automated playbooks can also increase the productivity of IT and support personnel by reducing the amount of trivial and time-consuming remediation tasks required, all while increasing response times to incidents.
Key takeaways
Microsoft Sentinel is Microsoft’s cloud-native SIEM and SOAR solution.
Gaining visibility across your entire IT estate is crucial to staying secure.
Sentinel pulls all your security event data into one place for effective threat detection and response.
Powerful AI and automation capabilities drastically reduce detection and response times.
Sentinel is highly compatible with both Microsoft and third-party solutions to give you a complete picture.
Sentinel, alongside Defender XDR and Microsoft Security Copilot is integral to Microsoft’s vision of an AI-powered unified SOC platform


Free Video
Microsoft Sentinel and Defender XDR Demos
Detect, investigate, and remediate threats across your entire network, with the power of AI.
See how you can:
- Make security and protection more efficient
- Utilise AI to power detection and remediation
- Protect endpoints, identities, and apps
Next steps

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great Microsoft Sentinel resources
























Got a question? Need more information?
Our expert team is here to help.