Diving into Microsoft’s Zero Trust approach to identity management and cyber security. We explore its principles, how it’s changed, practical applications, and why it’s the bedrock of a secure digital estate.
Microsoft made Zero Trust a foundational strategy for security more than five years ago. Today it underpins their philosophy for protecting people, devices, apps, and data.
It’s not a new concept. But it’s one that’s certainly come of age.
In this article we explore what Microsoft’s Zero Trust approach looks like in 2024.
And why, if it isn’t already, it should be high on your security radar.
Why are we having a Zero Trust conversation?
Over the last few years there’s been a migration of mindset among IT leaders towards the adoption of Zero Trust. Something which prompted Gartner to proclaim 2023 as the ‘Year of Zero Trust.’
This shouldn’t come as a surprise.
Organisations are growing wiser to the fact that older perimeter-style security measures are no longer equipped to protect the modern work environment.
That they’re vulnerable to those who target identities through phishing and credential theft.
That passwords aren’t enough to keep identities safe.
Or, that cloud, mobile, and IoT assets exist beyond the reach of firewalls.
But while there’s growing recognition of these facts, we still see a lot of organisations not doing enough about it.
After all, it can be a daunting prospect to completely overhaul your entire security strategy.
But this needn’t be the case. Especially as a Microsoft licence holder. With Zero Trust principles embedded across the full suite of identity and security products, the framework is there for organisations to embrace.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
Microsoft’s principles for Zero Trust
Zero Trust is based upon the mantra of: ‘Never trust, always verify.’
It’s a step change away from the traditional idea that anything ‘inside the perimeter’ is safe.
With a Zero Trust mindset, you’re treating all access requests with suspicion.
This is the basic premise used by Microsoft’s approach to Zero Trust. It’s a strategy designed to protect digital environments by assuming that breaches can occur at any point.
All of which is built upon three guiding principles that are laced into the fabric of the full Microsoft stack.
Verify explicitly
Don’t assume that just because something is on your network and seems legitimate that it is.
Access decisions should be based on several factors, including user identity, location, device compliance, classification of data and any relevant issues based on this access request. This should then be continuously verified throughout the session.
Least privileged access
Least privileged access means restricting user access rights to just the resources that are required to carry out the task at hand.
This is achieved by implementing just-in-time and just-enough-access policies. These, coupled with information protection policies, will help protect data wherever it travels and ensures the relevant level of access to your files is provided.
Assume breach
This one is important as it frames the whole mindset with which you should approach your security.
By doing so, you reduce the attack surface and prevent lateral movement by segmenting your network, users and devices when threats are detected.
You should ensure that all sessions are encrypted and utilise analytics to get visibility of threats and improve threat detection.
The Zero Trust model explained
Let’s start by looking at the depth to which a Zero Trust model goes into verification, compared to legacy approaches.
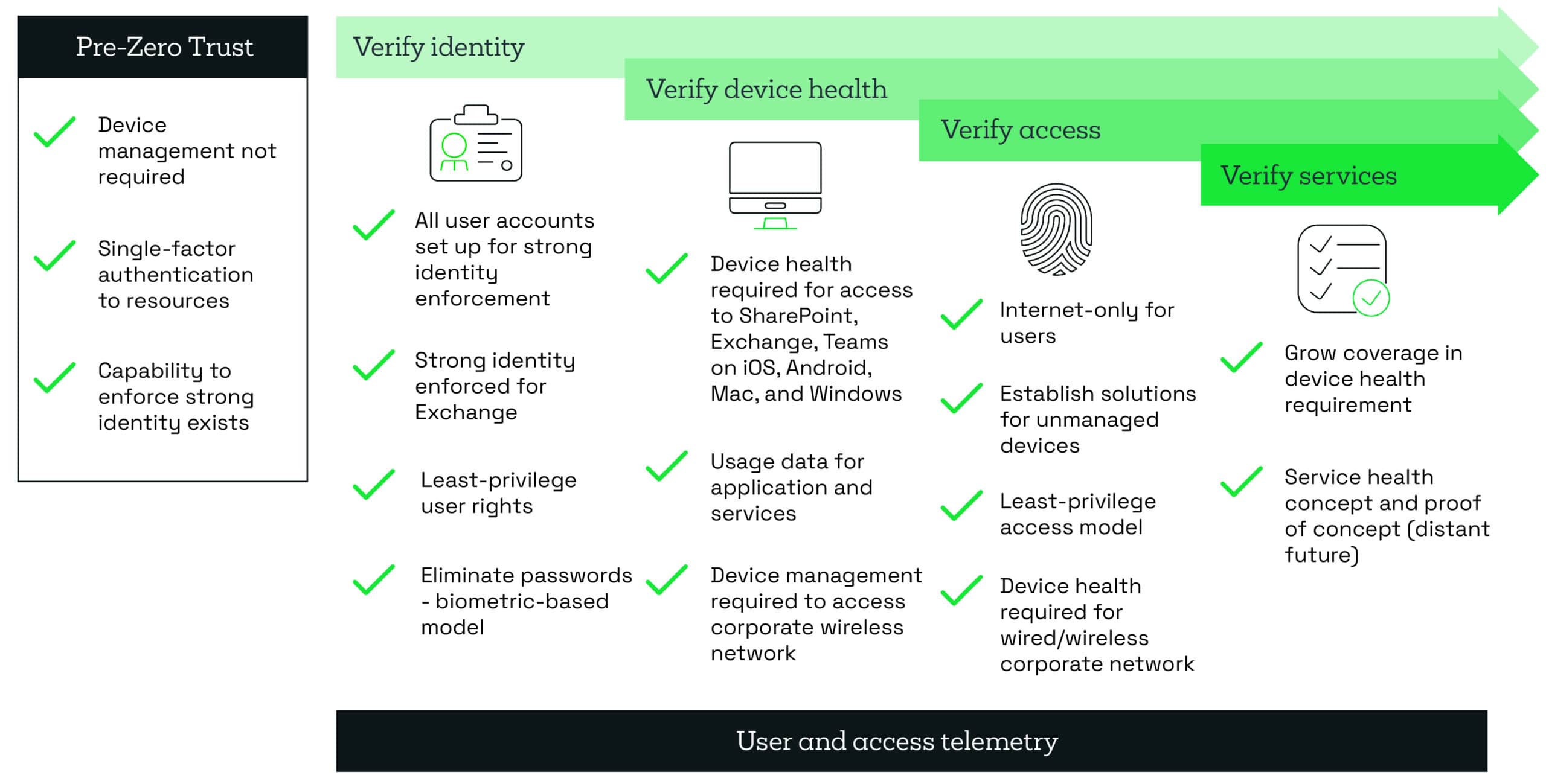
A Zero Trust approach is driven by attaining robust security across every aspect of your digital estate. Which is achieved by addressing six core components.
Identity and access is the cornerstone of Zero Trust security
A founding idea of Zero Trust (or any security for that matter) is the need to keep the ‘bad guys’ out and let the ‘good guys’ in.
But how easy is it to always know who’s who?
Attackers are going after user credentials in a big way.
Speaking at our 2024 Security Roadshow, Microsoft Chief Security Advisor Sarah Armstrong-Smith revealed that there were 240,000 email attacks per minute in 2023.
And passwords just don’t stand up to the scrutiny of attack.
Our suggestions:
Applying multifactor authentication (MFA) or biometric tools like Windows Hello can protect against more than 99% of identity and access attacks.
Enable Single Sign-On (SSO) across the estate to reduce authentication friction, enhancing user compliance, improve visibility and monitoring, and improve control logs of who is accessing what.
Adding Conditional Access policies within Microsoft Entra ID enables verification and access based on user, device, and application risk levels.
Enforce least privilege policies like Just-In-Time and Just-Enough Access (JIT/JEA), risk-based adaptive polices, and data protection.
Establish device safety
With identity processes in place, you need to understand the risk presented by the many devices accessing your resources.
Having the ability to understand if a device is known and managed is one thing. Understanding if that device has all the necessary security controls in place is another.
Achieving this across different platforms can be challenging but it’s important to do so.
Whilst a device could be compliant in its configuration, you need to be able to understand if that device is behaving suspiciously.
Our suggestions:
Leverage Microsoft Intune to enforce device compliance policies, ensuring that only secure, up-to-date devices can access corporate resources. Intune has the capability to manage corporate owned and private owned, allowing for strategic use of BYOD policies as appropriate.
Enable the advanced mobile threat detection and response capabilities of Microsoft Defender for Endpoint to monitor devices for security risks or unusual activity. And ensure rapid response and remediation in the event of a breach.
Global admin is only for when things hit the fan
Providing users with more access than required is an age-old problem.
Nearly everyone knows it’s bad practice to hand out global admin rights for simple tasks, but it’s still happening. The reason being is that it makes life easier for the admin to just provide free reign to a user rather than configure specific limits that they may end up having to amend later.
For Zero Trust to work, this mindset needs to change. You need to reduce your security footprint as much as possible to close off unnecessary and easy access for uninvited guests. This can be achieved by ensuring that users only have the privileges required to do their job.
Our suggestions:
Adopting a just-in-time approach for your privileged accounts allows the user to only use their privileged role when they need it and removes the access when they don’t. This can be achieved by enabling Privileged Identity Management (PIM) and Entitlement Management, available in Microsoft Entra ID P2 licence.
This can be further enhanced by applying ‘just in time access’ in your Azure Network Security features.
Monitor, orchestrate, and respond
The success of adopting a Zero Trust approach depends largely on an organisation’s ability to apply these best practices and couple it with an assume breach mindset.
It really is a case of not if but when.
Nowadays, there are just too many ways a malicious actor can gain access to have 100% confidence that they’ll be stopped at the front door.
Adopting an assume breach mindset whilst using the necessary tools to give you this visibility needs to be considered across all your devices, applications and services, infrastructure, identities, data and networks.
Our suggestions:
Enable Microsoft Defender XDR to get rapid incident visibility and response across the entire estate from users, devices, cloud apps, and your 365 tools. Disrupt advanced attacks automatically and at machine speed to block lateral movement.
Leverage the power of Microsoft Sentinel, a cloud-based SIEM and SOAR solution that draws on Microsoft’s vast threat intelligence for greater investigation, analysis, and insight that can be pivotal in detecting attacks before they’ve had a chance to hit.
How to get started with Zero Trust
Adopting a Zero Trust approach tends to be more of a journey than a wholesale change. A technological and cultural shift in the organisation that will develop over time.
If you’re at the foothills of this journey, then here’s a few steps that will point you in the right direction.
1. Assess your risk
Compile an inventory of your assets and IT infrastructure. What types of data do you have and where is it kept? What degree of protection is required?
With the traditional perimeter gone and data moving freely between devices in different locations, your security needs to follow the data trail.
2. Network segmentation
For Zero Trust to work, you have to be able to limit lateral movement within your network when a breach occurs. Think of it like shutting the fire doors to contain a blaze and prevent its spread.
Segment your network by separating different layers of your applications into different network VLANS managed by rules that dictate what can (and importantly can’t!) travel from one VLAN to the other.
Separating layers of the application, such as the database, application processing and application interface components, will make it much harder for malicious users to gain control. This should be considered for both your Azure-hosted infrastructure and on-premises infrastructure.
3. Configure access
Once you know your risk and have appropriately divided your network, you can begin to think about who you’re going to give access to based on defined identity rules.
This is where you can stipulate the use of MFA and Conditional Access based on role, device, application and more. Be sure to configure your network so that granting access to one environment does not mean automatic access to others.
In Zero Trust, every access request is scrutinised to ensure validity.
4. Don’t forget your people
Zero Trust can be a major change in the business. A new approach, often supported by new technology. You need your people to buy into this, and come along on the journey. After all, any strategy is only as good as its adoption. Educate your users on why the changes are being made, how to use the technology properly and invest in teaching them good cyber hygiene habits and Zero Trust tenets.
Human beings will always be fallible. Intentionally or not we can all pose a significant risk to IT security. So proper tech adoption planning is critical to reaping the benefits of a Zero Trust approach.
5. Enable least privileged access
Prioritise your most valuable assets and look to apply fine-tuned privileged access controls now that you’ve got your identity management working flawlessly.
This is where that just-in-time access comes into play and helps give your security a boost. Ideally, you would eventually have this degree of control over your entire estate, but first and foremost start with protecting your key resources and data.
6. Analyse, analyse, analyse
Zero Trust is driven by data. For a Zero Trust approach to be successful, you’ll need an effective way to monitor the activity of your environment that removes the alert fatigue and heavy lifting from your IT security team.
Software such as Microsoft Sentinel is ideal for this purpose. Constantly evaluating access requests and weighing them against factors such as location, time, device, frequency, etc. Giving you near real-time feedback of any suspicious activity, whilst facilitating verified requests to proceed with next to no interruption to the end-user.
The future of Microsoft’s Zero Trust approach to security
One thing that seems clear is that Zero Trust is likely to be the bedrock of Microsoft security for some time to come.
But it’s an approach that’s already evolving beyond it’s origins. This is largely due to the combination of emerging technology and the rapid advancement of cyber threats.
Add to that the ongoing change of working cultures, the continued path towards cloud ubiquity and ‘everything as a service’, or the perpetual increase in connected devices and IoT.
This all throws up challenges about how to secure access to your network and cloud-apps from anywhere, without friction or frustration for the user. That perennial dilemma of protection versus experience; moved into a remote, multi-cloud environment.
A challenge already being addressed by the emergence of Security Service Edge (SSE) solutions like Microsoft’s Global Secure Access suite. Offering new, identity-driven access to networks on the Zero Trust principles of least privilege, explicit verification, and assumed breach.
And of course, we’re already seeing the major impact of AI and machine learning, both from the perspective of attackers and defenders. As it relates to a Zero Trust approach, this means getting increasingly diligent in the face of improved AI-driven identity attacks, for instance. But also in utilising the AI-powered tools within Microsoft’s stack that’s designed to keep ahead of the threats.
Remember, the Zero Trust model is not a suite of tools or products.
It’s a mindset. A set of principles that help shape our thinking about how to keep our people, devices, data, assets, and network safe. However they evolve.
Key takeaways
Zero Trust is a security approach based on an assume breach mindset.
Every access request is verified and analysed before approval.
It brings together strong IAM and the latest security technologies.
Apply Zero Trust to every element of your environment.
Zero Trust enables flexible access and fast, data-driven security response.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great security & compliance resources
























Got a question? Need more information?
Our expert team is here to help.