
Case Study
Large UK insurer improves endpoint security and compliance
As one of the UK’s largest insurers representing many UK household insurance brands, our client came to Kocho with a vision to bolster security for endpoints and devices, whilst improving compliance controls around sensitive document sharing and collaboration.
The organisation had been a Broadcom client for over 15 years, but upon completion of a discovery and capability mapping exercise, was excited to be modernising with a hybrid-cloud infrastructure using Microsoft 365’s full suite of security and compliance products.
With plenty of experience in endpoint security, information protection, and helping organisations stay compliant, Kocho were more than qualified to help our client improve their overall security and compliance posture.
Replacing an ad-hoc system with a simplified cloud platform for improved security and data protection
How we helped our client ‘Become greater’:
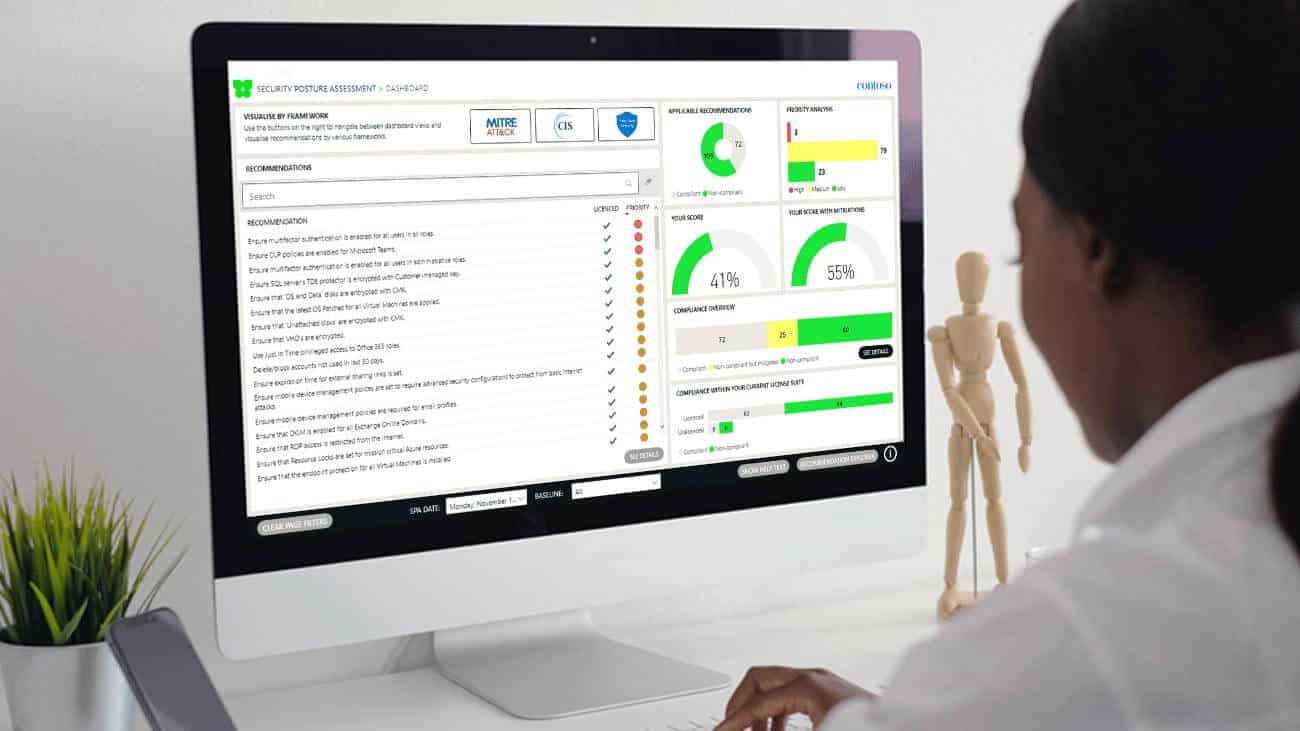
Watch 3-minute Security Posture Assessment Demo
See for yourself how a Security Posture Assessment helps you:
- Improve visibility of security threats
- Prioritise threats based on risk and effort
- Track improvements and measure ROI
- Stop wasting money with smarter investments
Addressing growing concerns with endpoint security and documentation
For an organisation with over 14 million customers, 10,500 employees, and dozens of office sites around the UK, changing the way it secures devices, endpoints, and documentation can quickly become an overbearing task (especially given the scale of challenges surrounding endpoint security).
Finding the right organisation or partner that can provide the best technology is a painstaking process, and it can be difficult to know where to start. Kocho was able to take the pain away from this process with a series of discovery workshops and capability mapping sessions.
These sessions helped our clients’ board, IT teams, and compliance decision makers understand the value of the Microsoft 365 E5 Security and Compliance suite, clearly showcasing how all the components work together.
Workshopping a complete Microsoft solution
Kocho assessed the current infrastructure to better understand how Microsoft could potentially replace the existing Broadcom solution. The capability mapping exercise was led and conducted in a workshop scenario by experienced Kocho Architect David Guest.
We led three separate workshops examining the business requirements, the current solution in place, followed by a modelling and documentation exercise.
Kocho spent time understanding the clients current requirements, how the existing Broadcom technology supported them, and if other complementing solutions were required to fulfil the client’s needs.
A walk-through and demonstration via the client’s architecture team was conducted to obtain a complete understanding of how the existing technology was working.
We discovered that the current solution was integrated with a lot of other technologies to provide sufficient security, and that whilst Broadcom and Microsoft’s functionality was similar, both solutions worked in different ways.
Highlighting the gaps in the existing solution architecture
It became clear that Broadcom has a lot of individual components that are “best of breed” as standalone solutions. However, this solution needed a lot of work to create a comprehensive platform across the whole technology stack.
In the second session, Kocho architects highlighted where gaps existed in the current Broadcom products and where there may be potential gaps in Microsoft’s version of the product, including how any gaps would be filled by Microsoft’s full suite of tools.
Kocho then provided an overview of Microsoft’s offerings and highlighted the differences between the two solutions. This part of our engagement was crucial as when working closely with Microsoft, we often find that one individual product suite doesn’t always replicate existing capability.
But after reviewing the full complement of Microsoft technologies and then using different suites of products configured together, we found that these more than replicated our client’s requirements when compared to Broadcom.
A detailed report and a move to utilise the whole of Microsoft 365’s functionality
Once the high-level analysis had concluded, a report was compiled and the results were presented back in the final workshop session with Kocho. We confirmed that the adoption of Microsoft 365 could replace the majority of the existing email, documents, and Windows device solutions.
This would not only reduce the client’s attack surface, but it would also significantly reduce regulatory compliance risks – all by maximising the ROI from its existing Microsoft licence fees.
The report noted that there are some elements of the Broadcom stack where Microsoft don’t yet have a ready-made replacement (specifically, the cloud-based reverse proxy), but this functionality would be easily achieved by integrating the Microsoft stack with a partner from their ecosystem.
Furthermore, Kocho concluded that given the use of Office 365 within the client’s infrastructure, the adoption of the Microsoft stack was an obvious move.
With the integration between the different Microsoft components increasing day by day and the aim to move to a single set of portals for administration becoming more real, there were few arguments against displacing Broadcom with the Microsoft version.
Moving forward and solution implementation
As part of the findings report, Kocho provided a recommended implementation roadmap, suggesting that consideration must be given to the desktop and mobile device management solutions to support the delivery of change in a lot of cases.
Each element could then be considered on its own or could have been rolled into a programme of work dependent upon the client’s own priorities and timelines. Further analysis was also conducted on the changes in ways of working for the client’s employees.
Kocho’s Business Transformation team worked alongside the technical team to ascertain how user journeys would change with the Microsoft version in place and a user adoption strategy was created to drive successful adoption where appropriate.
Next Steps

Watch 3-minute Security Posture Assessment Demo
See for yourself how a Security Posture Assessment helps you:
- Improve visibility of security threats
- Prioritise threats based on risk and effort
- Track improvements and measure ROI
- Stop wasting money with smarter investments

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great mobile threat defence resources

Microsoft Security Roadshow
Demos and expert insight to help you get the most from Microsoft's identity, security and cloud solutions.

Is it time to leave your security operations to the experts?

Why it's time for identity-first unified device management

Microsoft Intune explained: A guide to endpoint management and security
























Got a question? Need more information?
Our expert team is here to help.

