
Blog | 12-minute Read
What is Microsoft Azure AD B2B?
Marcus Idle
Published: 20 December 2022
Allowing external users access to your resources without compromising security can be a major headache. In this article we explore how Microsoft Azure AD B2B makes this process simple, seamless and safe.
Providing timely, hassle-free access to outside suppliers and other external people can be crucial for organisations. It’s a vital way to unlock benefits from the specialist expertise brought by your partners.
However, these users often don’t have the same onboarding, offboarding, and governance mechanisms as your permanent staff.
Many organisations still create username and password sign-in for their external users. Once they leave their own ‘native’ organisations, they may still retain their sign-in details for yours.
Which represents a significant security risk.
So, how can you securely share resources and applications with outside collaborators?
The solution lies within Azure AD External Identities.
And, in particular, Azure AD B2B.


Free Guide
The ultimate guide to external identity success
A 7-step plan to achieve seamless user access, the highest levels of security, and unrivalled user experiences.
Discover:
- How to reduce account compromise attacks by 99%
- Why the right IAM solution can increase ROI by 123%
- How to achieve compliance through good governance
What is B2B in Azure AD?
Azure AD B2B is a feature within External Identities that allows you to invite external users as guests to collaborate with your organisation.
External users can be invited to sign in to your Azure AD organisation with their own credentials.
They can then securely access the resources and applications you need to share. While you maintain full control over what external users can access, and your corporate data.
Azure AD B2B can be used regardless of the size of the external partner.
What’s more, it doesn’t matter if they don’t have Azure AD themselves – or even an IT department.
How does Azure AD B2B work?
Established identity providers outside of Azure AD (e.g., Google Workplace) can be ‘federated’ (or linked to your Azure AD tenant for collaboration) using the ‘External Identities’ panel in Azure.
- Inviting users to your tenant is as easy as sending the invitations to any email address. Azure takes care of the onboarding mechanism.
- Users without Azure AD or a federated identity system are given an email-based one-time passcode (OTP) as a means of sign-in
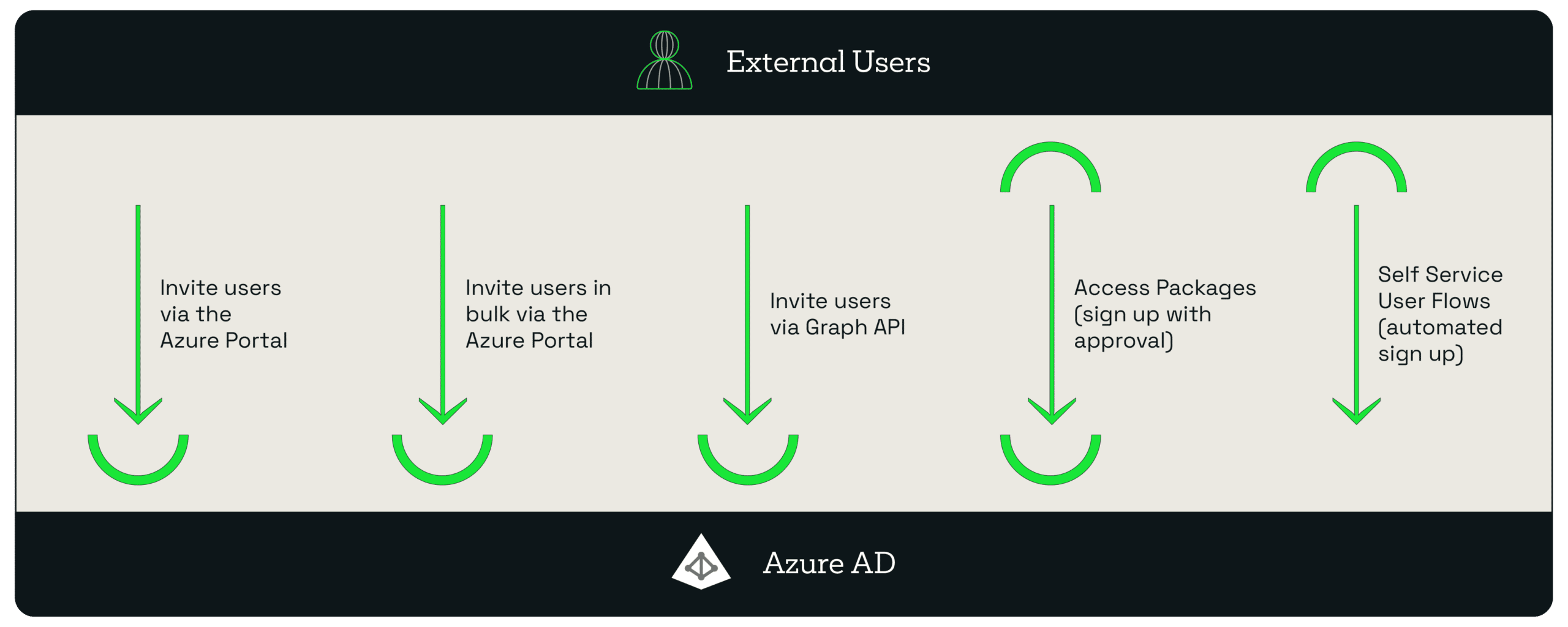
- Users can be invited one by one or in bulk by email address via the Azure portal. This is an invite-driven (‘pull’) process.
- Microsoft Graph API can be used to replicate this function from a machine perspective.
-
Users can apply for an approval-based access package using the Microsoft Access portal.
- Self Service (External Identity) user flows give you the ability to onboard users with automatic approval.
Benefits of Azure B2B
B2B addresses the problem of sharing your resources and applications with external users. These users may be suppliers, customers, partners, or any kind of external users.
With Azure, all of the technical configuration is handled behind the scenes. All you need to worry about is what organisations and users are collaborating with you.
Once invited, you can:
- Place guests into the same groups as your employees to manage access to resources
- Control and review access with Azure AD’s Conditional Access and access reviews.
- Easily create terms-of-use for your guests to accept before they gain access.
Other B2B benefits
Azure AD B2B can also benefit your organisation in other ways.
It’s easy to invite guests and internal users quickly
As an administrator, you can easily add guest users to your organisation in the Azure portal.
- Create a new guest user in Azure AD, similar to how you’d add a new user.
- Assign that guest user to apps or groups.
- Send an invitation email containing a redemption link or send a direct link to an app you want to share.
Guest users/collaborators can self-serve
Azure AD B2B allows you to create a self-service sign-up experience for external users who want to access your apps.
Plus, you can integrate your self-service sign-up user flows with external cloud systems using application programming interface (API) connectors.
It allows you to:
- Connect with custom approval workflows
- Perform identity verification
- Validate user-provided information.
Use policies to securely share your apps and services
Using custom authentication and authorisation policies, you’re able to easily protect corporate content.
You can enforce Conditional Access policies, (e.g., multi-factor authentication) at the tenant and application level, as well as for specific guest users.
Application and group owners can manage their own guest users
You can use Azure AD B2B to delegate guest user management to application owners.
This means you’re able to add guest users directly to any application you want to share. It doesn’t matter if it’s a Microsoft application or not.
Integrate with SharePoint and OneDrive
It’s easy to securely share resources with people outside your organisation. Simply enable integration with SharePoint and OneDrive.
Typically, users you share resources with are added to your directory as guests. Meaning you can control permissions and groups the same as you would for internal users.
Credentials stay in the guest directory
With Azure AD B2B, you don’t need to administrate any of your external partners’ credentials.,
They’ll use their own identity management solution, signing in to your apps and services with their own identities.
Access control is managed in the host directory (your directory)
You don’t have to do any administration over your external partners’ credentials. But that doesn’t leave you powerless.
You’ll still have complete control over the access those external partners have to your resources and applications.
New bespoke branding features within B2B
Microsoft have recently redesigned the company branding functionality. This allows a more flexible, user-centric customisation of the built-in identity flows for Azure AD and includes B2B.
With enhanced company branding functionality, you can create a custom look and feel for your sign-in pages.
This means that you’ll be able to:
- Customise the self-service password reset (SSPR) hyperlinks.
- Customise the footer hyperlinks.
- Customise the Browser icon.
- Use cascading style sheets (CSS) to create sign-in experiences.
- Enable header and footer using pre-defined templates.
Brand consistency is a hugely important factor for any organisation. So, being able to develop pixel perfect branded sign-ins for both customers and external partners further empowers the brand and improves the user experience.
How to enable Azure AD B2B
Firstly, you’ll need to enable and configure your external identities function of Azure AD.
Sign-In
- Sign in to the Azure portal (you’ll find that here) with a Global administrator account. Open the Azure Active Directory service.
- Select ‘External Identities’, and then ‘External collaboration settings’.
Guest user access
Select your guest user’s access level:
- Guest users have the same access as members: This is the most inclusive option and gives guests the same access to Azure AD resources and directory data as your existing users.
- Guest users have limited access to properties and memberships of directory objects: This is the default setting, and it blocks guests from certain directory tasks.
- Guest user access is restricted to properties and memberships of their own directory objects: This is the most restrictive setting. Guests are only allowed access to their own profiles.
Guest invite settings
Choose the settings appropriate for you.
- Anyone in the organisation can invite guest users including guests and non-admins: This lets guests invite other guests, including those who aren’t members of an organisation.
- Member users and users assigned to specific admin roles can invite guest users including guests with member permissions: This allows member users and users with specific administrator roles to invite guests.
- Only users assigned to specific admin roles can invite guest users: This lets users with administrator roles to invite guests. Administrator roles include Global Administrator, User Administrator, and Guest Inviter.
- No one in the organisation can invite guest users including admins: This is the most restrictive setting and denies everyone the ability to invite guests.
User flows
- Enable guest self-service sign up: Select YES, if you want to create user flows that let users sign-up for apps
External user leave
Use these settings to control whether external users can remove themselves from your organisation.
- Selecting ‘yes’ lets users leave the organisation without approval from your admins.
- Selecting ‘no’ means that users won’t be able to leave your organisation themselves. They’ll see a message guiding them to contact your admin or privacy contact to request removal from your organisation.
Collaboration restrictions
Choose whether to allow or deny invitations to domains you’ve specified and enter specific domain names in the text boxes. For multiple domains, enter each domain on a new line.
Now that you’ve tweaked all of your external collaboration settings to your preferences, configure your Azure AD B2B.
B2B collaboration is enabled by default, but comprehensive admin settings let you control your inbound and outbound B2B collaboration with external partners and organisations:
- For B2B collaboration with other Azure AD organisations, use ‘cross-tenant access settings’. This lets you manage inbound and outbound B2B collaboration, and manage access to specific users, groups, and applications.
- Using cross-tenant access settings, you can set a default configuration that applies to all external organisations. From there, you can create individual and organisation-specific settings.
You’ll be able to trust multi-factor (MFA) and device claims from other Azure AD organizations.
Is Azure B2B free?
Because Azure AD B2B is an External Identities function, it’s priced following the External Identities pricing model.
This is based on monthly active users (MAU). Helping you reduce costs and make forecasts with confidence.
There’s a free tier, a flexible tier, and a predictable pricing tier.
- Free Tier: Your first 50,000 MAUs per month are free for both Premium P1 and Premium P2 features.
- Flexible: This lets you connect with your customers or partners based on usage and features you need, rather than the licences you own.
- Predictable: This tier means you’ll only pay for what you use. You won’t be charged for a monthly active user’s subsequent authentications, or for storing inactive users in that calendar month.
Microsoft’s aim is to offer flexible, predictable, and cost-efficient billing that reflects the usage and features you need, rather than the licenses you have.
Allowing 50,000 free monthly active users at every tier means that the vast majority of customers are able to use Azure AD External Identities for free.
Azure AD B2B Costs
Azure AD External Identities is billed from the following starting rates:
Premium 1 |
Premium 2 |
|
|---|---|---|
First 50,000 MAUs |
£0/MAU’s |
£0/MAU’s |
More than 50,000 MAU |
£0.002700/MAU’s |
£0.013499/MAU’s |
Azure AD B2B licensing requirements
Azure AD B2B is a feature of the overall Azure AD technology solution. Meaning you don’t need a separate licence for it.
Azure AD comes in four editions:
Free
Included with a subscription of a commercial online service, such as Azure or Intune.
With Office 365 apps
Office 365 subscriptions include the Free edition, but Office 365 E1, E3, E5, F1 and F3 subscriptions also include features listed under Office 365 apps.
Key takeaways
Premium P1 / Premium P2
Available to purchase through your Microsoft representative, as well as the Open Volume Licence Programme, and the Cloud Solution Providers programme.
Azure and Office 365 subscribers can also buy Azure Active Directory Premium P1 and P2 online.
By employing incremental pricing for Premium P1 and Premium P2 features, organisations have the flexibility to offer world-beating security to any user.
Without the need to purchase more Azure AD licenses.
How Azure B2B stacks up to B2C
You may already know that Azure AD comes in two flavours: B2B and B2C.
As a customer identity access management (CIAM) solution, B2C supports millions of users and billions of authentications per day.
It enables your customers to sign-in with pre-existing identities, such as Facebook or Gmail. While allowing organisations to customise and control how their customers sign-up, sign-in, and manage their profiles.
While currently B2C is more customisable, things are changing. New custom features are being added into B2B all the time. This includes API connectors, additional attributes, and custom page layouts.
Both solutions are based on the same technology.
You can read our comprehensive B2B v B2C comparison guide here.
Conclusion
The need to collaborate with partners outside of the boundaries of your organisation is always going to exist.
However, giving outside collaborators access to your data, applications, and resources is always going to represent a security risk.
With Azure AD B2B, external users can sign into your organisation securely, using their own credentials. You stay in complete control of what’s shared, and what access those external partners have to data and applications.
As we’ve seen, rolling out B2B can be quite a tricky proposition. There’s a lot to consider with regards to enabling the technology, its pricing models, and its licencing requirements.
However, it needn’t be. By employing the help of the correct partner, your B2B rollout can be smooth and secure.
B2B has undergone a number of changes and improvements. Some of the functionalities of its sister technology B2C is now available for B2B customers.
With these changes, it’s looking increasingly like the two solutions are converging, and the labels B2B and B2C will be retired for one External Identities portal.
Key takeaways
B2B allows your organisation to collaborate with outside partners safely, while you retain control over access.
Outside partners are able to use their already existing identities to sign in to your organisation.
Credentials of your guests stay in their directory, while access control is managed by you in your host directory.
Using an experienced outside partner to configure Azure AD B2B can help to mitigate some of the difficulties of deployment.


Free Guide
The ultimate guide to external identity success
A 7-step plan to achieve seamless user access, the highest levels of security, and unrivalled user experiences.
Discover:
- How to reduce account compromise attacks by 99%
- Why the right IAM solution can increase ROI by 123%
- How to achieve compliance through good governance

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great enterprise identity resources
























Got a question? Need more information?
Our expert team is here to help.







