Ransomware attacks pose one of the most disruptive, destructive, and costly cyber security risks to an organisation. And it’s continually evolving.
Ransomware isn’t a new thing. In fact, the first recorded incident dates back to 19891. And it remains a major threat to this day.
As technology has advanced, so ransomware has evolved.
Better tech, broader attack surfaces, smarter (sneakier?) tactics, and commercialisation has led to a ransomware renaissance.
And that’s bad news for affected organisations.
Let’s look at what makes this such a prevalent threat today.
And a significant reason you need to have robust security processes, and effective threat detection and response measures in place.

The global cost of ransomware attacks equates to $30,051 per minute.2
The malware that makes you pay
For those of you who don’t know, ransomware is a particularly nasty kind of malicious software (malware).
If it gets into your network it will encrypt all the files stored within. Effectively holding your data hostage until you pay a ransom for its release.
And, whether the ransom is paid or not, the attack comes at a cost.
Cyber Magazine3 reported that almost half of attacked organisations paid the ransom to recover their data, with large enterprises much more likely to pay.
However, it goes on to say that recovery costs substantially added to the overall pain.
But that’s only part of the cost. If you’re hit by a ransomware attack, the residual damage can be particularly harmful. And potentially long-lasting.
The costs across your business
You’re also likely to be hit in the pocket due to:
- Loss of earnings during downtime
- Cost of recovering the data
- Regulatory penalties for compliance breach
- Diminished productivity
- Loss of customers and reputational damage
Plus, there’s no guarantee that your attacker will release the data upon payment, keeping you in a longer level of paralysis.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
The rise of Ransomware as a Service
Taking its lead from the business-models of modern-day Software as a Service (SaaS) operations, cyber criminals are increasingly setting up ransomware packages available for sale on the dark web.
So, why should you be concerned by this?
The ransomware ‘industry’ is a lucrative hunting ground. As such, it’s able to attract those with skills in software development, finance, and other technical and operational skillsets, seeking to make a quick and healthy profit for their efforts.
Which leads to:
- Better innovation and sophistication of the software
- Ability to rapidly scale up the volume of attacks
- Lower barriers to entry for potential bad actors
- Increased chances of successful attacks
- Higher ransom demands
Like the best SaaS models, RaaS offers opportunities for attacks to grow in volume, improve in effectiveness, and increase revenue streams.
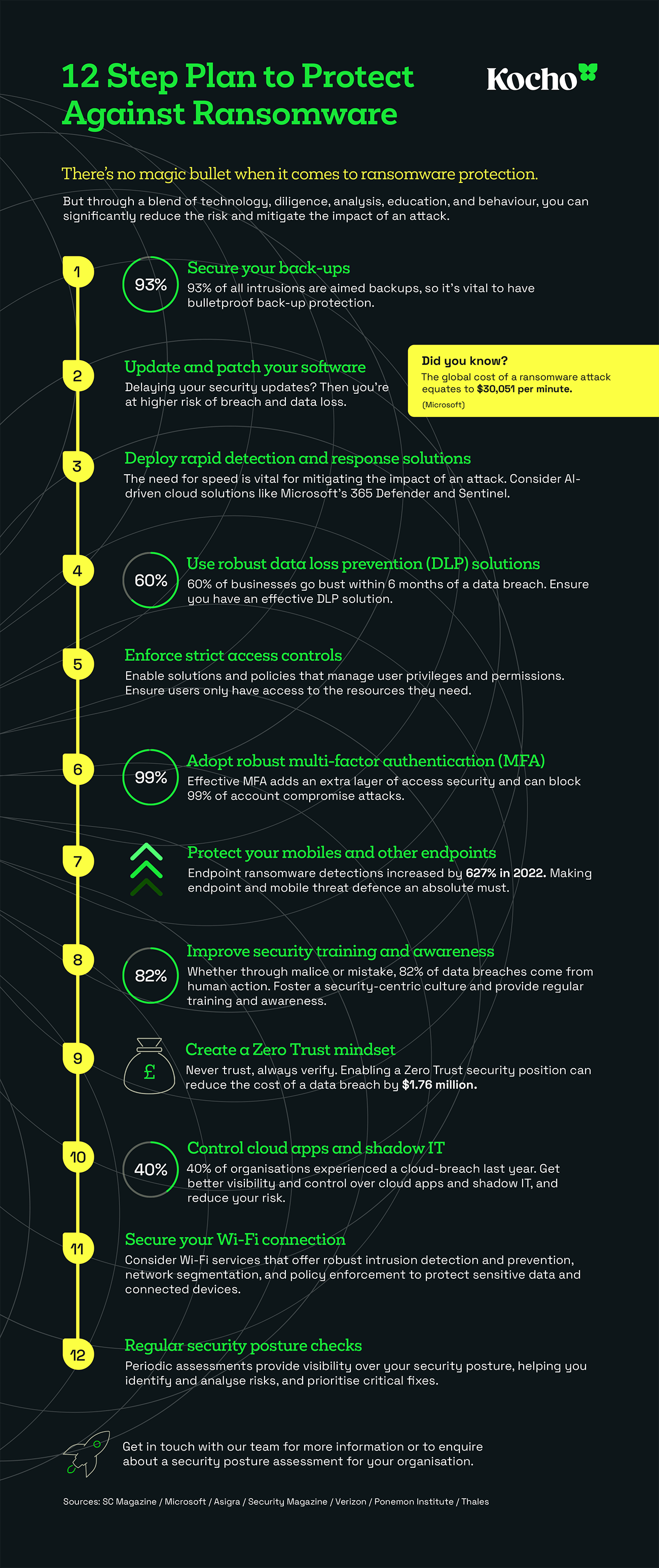
93% of all intrusions were aimed at back-ups, with 75% of these attacks ‘successful’.4
Attacking your back-ups
Backed-up data is now the primary target of ransomware attacks.
Of course, backing up your data regularly is a traditional tactic for mitigating the risk of losing access.
After all, if you’re subject to an attack, you can retrieve the backed-up data and you’re back in business, right?
But what if your back-up is breached?
Now you have a problem.
Typically these attacks are meticulously planned, with trojan horse style malware implanted into a system months ahead of the attack.
Meaning when they strike, your backed-up data is already compromised.
Leaving you with nowhere to run.
Completely at the mercy of the hacker and increasing the likelihood that you’ll pay.
This is why it’s essential that you have robust security measures for your back-up systems.
Consider a software solution that not only scans and quarantines malicious files during the back-up process, but can also scan and detect malware lying dormant within your back-ups. Isolating it before it has a chance to infiltrate your system.
Speak to an expert for more information on how to protect your back-ups.
Connected devices can be a cause for ransomware concern
From mobile devices, to laptops, printers, and the increased number of internet of things (IoT), connected devices have created diverse digital ecosystems.
And increased the attack surface immeasurably.

Endpoint ransomware detections increased by 627% in 20225
Attackers are innovative in their tactics
Any mobile or other endpoint where security is not up to scratch is a sitting target for attack. And the threats are ever-present and ever-evolving.
Such as:
- Exploiting vulnerabilities in the operating system: Whether Android or iOS, operating systems are frequently updating to address vulnerabilities. But too many users ignore or delay the updates on their devices. Exposing them and their system to risk of exploitation.
- Compromised apps: Downloading apps from illegitimate sources, or failing to keep apps updated on your device represent another major weak spot that can allow the malware into your system.
- Clicking unsafe links and websites: While your office desktop may have measures in place to stop you visiting a high-risk site, it’s not always the case when it comes to mobile devices. Especially if it’s the users personal device being used for work.
- Credential or password dumping: Hackers will exploit devices with poor security measures to steal credentials stored within it. Once they have the credentials, they can potentially gain illicit access to your organisation’s data.
- Juice jacking: This involves installing malware onto a victim’s device via public USB ports and charging stations. A particular hazard for remote workers and those who spend their working days ‘on the road’.
With the increase of employees using their own devices at work (BYOD), mobile breaches can lead to a direct threat to the organisation.
Mobile usage is here to stay, and offers real operational and cost benefits to organisations. But you need to be aware of the risks, and ensure you have the policies, procedures, and tools in place to keep protected.
Find out more about how you can keep your mobile fleet safe.
Siegeware and the ransomware risk to your office
Siegeware is a particular type of ransomware that has the capacity to completely disable your office or place of work.
It’s a direct attack on so-called ‘smart devices’, led by the increased adoption of IoT within our digital environments.

IoT targeted attacks have increased by 41% in the past year.6
Think about the modern office environment, where everything from printers and routers, to the heating, A/C, alarms, and fire detection systems are connected to the network.
If a malicious actor gains access to the central system, they can effectively lock down all of these devices.
When considering the vulnerabilities in your system and security posture, you need to take account of every endpoint and access route that could be exploited.
Social engineering is the primary ransomware tactic
When it comes to cyber breaches, it’s easier to trick a person than a piece of software.
Social engineering focuses on potential lapses in judgement, ignorance, or naivety.
It exploits gaps in knowledge, behaviour patterns, and targets those who might be susceptible to ‘turning to the dark side of the force’.
And it works.

Social engineering is used in 98% of cyber attacks.7
Far and away the most common form of social engineering is phishing, or spear phishing. Phony emails designed to get the recipient to click on a ‘dodgy’ file or link.
While this has been a tactic in use for many years, it remains a successful weapon in the hackers arsenal.
And, with the emergence of new AI tools, phishing scams have improved, becoming harder for the human eye to detect.
But it’s not the only trick in the book.
Other social engineering tactics include:
- Bogus multi-factor authentication (MFA) prompts
- Mobile SIM-swapping to take over accounts
- Targeting unhappy employees with payments for credentials
- Targeting personal email accounts to gain access to credentials
- Fake help desk calls to reset login details
Ransomware is a real risk and you need to stay vigilant
There’s a successful ransomware attack every 40 seconds.8
Making it a major reason why you need to keep a tight rein on your security operations.
Of course, this represents an ongoing challenge. Tactics change and threats evolve. Malicious actors are always probing for weaknesses, seeking new ways to get into your system.
And once they’re in, and they have control of your data, you have a costly problem on your hands.
So, what can you do to stay ahead of the threat?
As well as ensuring you keep your system up-to-date and securely backed-up, you need to have the right:
- Policies and processes
- Training, awareness, and culture
- Visibility of weak spots across the estate
- Threat detection and response tools
- Access and user privilege controls
- Mobile and endpoint threat defences
The ransomware threat is always there. It never takes a day off.
Neither should your security.
Key takeaways
Ransomware remains a major threat that can bring devastating corporate costs.
RaaS has industrialised ransomware, increasing attack sophistication and velocity.
Back-ups are a key target and need to have quality security measures in place.
Social engineering is the main strategy of malicious actors.
Mobile, endpoint and IoT security is critical in mitigating ransomware risk.
It’s imperative you have the right tools, policies, and training in place.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Next steps
Sources: 1: Techtarget | 2: Microsoft | 3: Cyber Magazine | 4: SC Magazine | 5: Security Magazine | 6: Checkpoint | 7: Purplesec | 8: Dataprot
Like this? Don’t forget to share.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great security & compliance resources

Microsoft Security Roadshow
Demos and expert insight to help you get the most from Microsoft's identity, security and cloud solutions.

Purview Demo: Securing data in the age of AI

Cybersecurity a year in review: What happened in 2025, and what it means for your 2026 security strategy

How to achieve cost-effective threat visibility with Microsoft Sentinel data lake
























Got a question? Need more information?
Our expert team is here to help.




