With the launch of Microsoft Entra External ID for Customers, we explore the potential transition from Azure AD B2C. And how you can develop a customer identity and access management (CIAM) strategy for the long-term.
On May 15 2024, Microsoft released Entra External ID into general availability. This is Microsoft’s next generation customer identity and access management (CIAM) solution. A new platform that aims to extend the capabilities of Entra ID to external identities.
And we’re already starting to see its potential with frequent feature updates helping the platform quickly evolve.
Now you might be asking what this means for Azure AD B2C. After all, this has been the ‘go to’ CIAM solution for many organisations.
In this blog, we’ll explore the pathway from Azure AD B2C to Entra External ID. The steps and considerations you need to take to ensure you keep pace with changing customer identity trends. And to ensure that your CIAM solution is equipped for future challenges.
So, what’s happening with Azure AD B2C?
Well, Azure AD B2C remains a mature, robust solution for login and registration journeys, supporting multiple authentication methods and extensive user experience customisations. And, for the foreseeable future, Microsoft have committed to supporting this popular platform.
However, mastering Azure AD B2C’s proprietary XML format to build custom policies can be challenging.
And, with Microsoft now shifting its focus to Entra External ID, the older platform hasn’t seen any significant updates of late.
The reality is the future of Microsoft’s customer identity management is with Entra External ID.
Comparing Azure AD B2C and Entra External ID
At Kocho we’ve got a long track record of building CIAM solutions with Azure AD B2C. We know its intricacies, capabilities, and features. And, as a leading Microsoft identity partner we’ve also been fortunate enough to have had advance insight into Microsoft Entra External ID for Customers.
Placing us in the ideal position to offer a comparison of the two platforms.
For instance, Azure AD B2C offers:
- Custom JavaScript and CSS: Azure AD B2C supports extensive user interface customisation, making it possible to address specific client needs with advanced UI tweaks and design consistency. At present, Entra External ID doesn’t fully support these capabilities in its browser-delegated journeys.
- Flow Control Logic: The platform allows you to tailor user journeys based on various attributes, creating a bespoke experience for users. This nuanced control is currently not available in Entra External ID’s browser-delegated flows.
- Custom User Journey Steps: With Azure AD B2C, you can build sophisticated multi-step processes using custom policies. Entra External ID offers only default step options at this point.
- Support for Various UI Controls: Different input types and form controls can be utilised extensively and further customised through JavaScript in Azure AD B2C. Entra External ID currently supports basic inputs like text, radio buttons, and checkboxes.
- Custom OIDC Identity Providers: Integrating external identity providers via OIDC is straightforward with Azure AD B2C, while Entra External ID is still catching up in this regard, currently supporting only SAML/WS-Fed.
As you can see, Azure AD B2C still has a range of features not yet released into the new Entra product. However, changes and new releases are happening fast, so watch this space.
And, as we’ll highlight below, Entra External ID for Customers also offers fresh capabilities that promise to redefine customer-facing identity and access management.


latest edition
Everything you need to know about Microsoft Entra
A clear, practical view of how Microsoft Entra works as a unified platform.
Expert guidance on modern identity design, security, governance, and Entra licensing.
Discover how you can:
- Run Entra as one coherent identity platform
- Apply end-to-end security and governance
- Modernise IAM safely, from MIM to AI-driven identity
Native authentication in Entra External ID
CIAM experiences built on Azure AD B2C are bound to a browser which is used to render the user journey and redirect the user back to the application in the end. While Entra External ID also offers browser-delegated CIAM journeys, it is now introducing a new approach which changes the way in which applications interact with the identity provider.
This authentication strategy, currently in preview in Entra External ID, gives full control over the design of the user journeys.
CIAM experiences are built within the application, and interaction with the Entra External ID tenant is performed via an SDK (MSAL) or via the native authentication APIs.
The CIAM journey no longer needs to be loaded on a browser. Instead, it’s integrated within the application.
This is the most flexible way to build CIAM journeys in Entra External ID.
It’s currently limited to email/OTP and email/password authentication with support for self-service password reset, but more authentication methods are likely to be added soon.
In our view, this is a level of flexibility that’s superior to that offered by Azure AD B2C because it’s completely under the control of the application.
Planning a migration strategy from Azure AD B2C to Entra External ID for Customers
Microsoft have committed to supporting Azure AD B2C for years to come, so there’s no rush for existing users to make the migration just yet.
However, Entra External ID is on a fast upward trajectory. And given the rate at which new features are being added, it’s advisable to consider your strategy for a future transition.
Let’s examine some of the options.
Tenant migration
Ideally, migrating an entire Azure AD B2C tenant to a new Entra External ID tenant, including users, applications, and custom policies, would be automated.
While it’s a capability being considered by Microsoft, it unfortunately appears unlikely any time soon.
So, we must consider other approaches.
Phased migration
A phased migration is more realistic. This approach involves running both Azure AD B2C and Entra External ID tenants in parallel until Azure AD B2C can be phased out:
- User Data: Store user data in either or both tenants using a combination of methods.
- User Journeys: Use Azure AD B2C for highly customised CIAM journeys, authenticating users in Entra External ID at the end.
- Gradual Transition: Gradually move CIAM journey steps to Entra External ID as more features become available, transitioning part of the journey from Azure AD B2C to Entra External ID seamlessly.
- User Migration: Migrate users from Azure AD B2C to Entra External ID via Graph API, either through batch processes or just-in-time.
Via ROPC from Azure AD B2C to Entra External ID
Resource Owner Password Credentials (ROPC) is an OAuth 2.0 flow which allows an application to verify the username and password of a user account directly on the destination directory.
This approach is risky because it requires a high level of trust in the calling application and is limited to just username/password authentication.
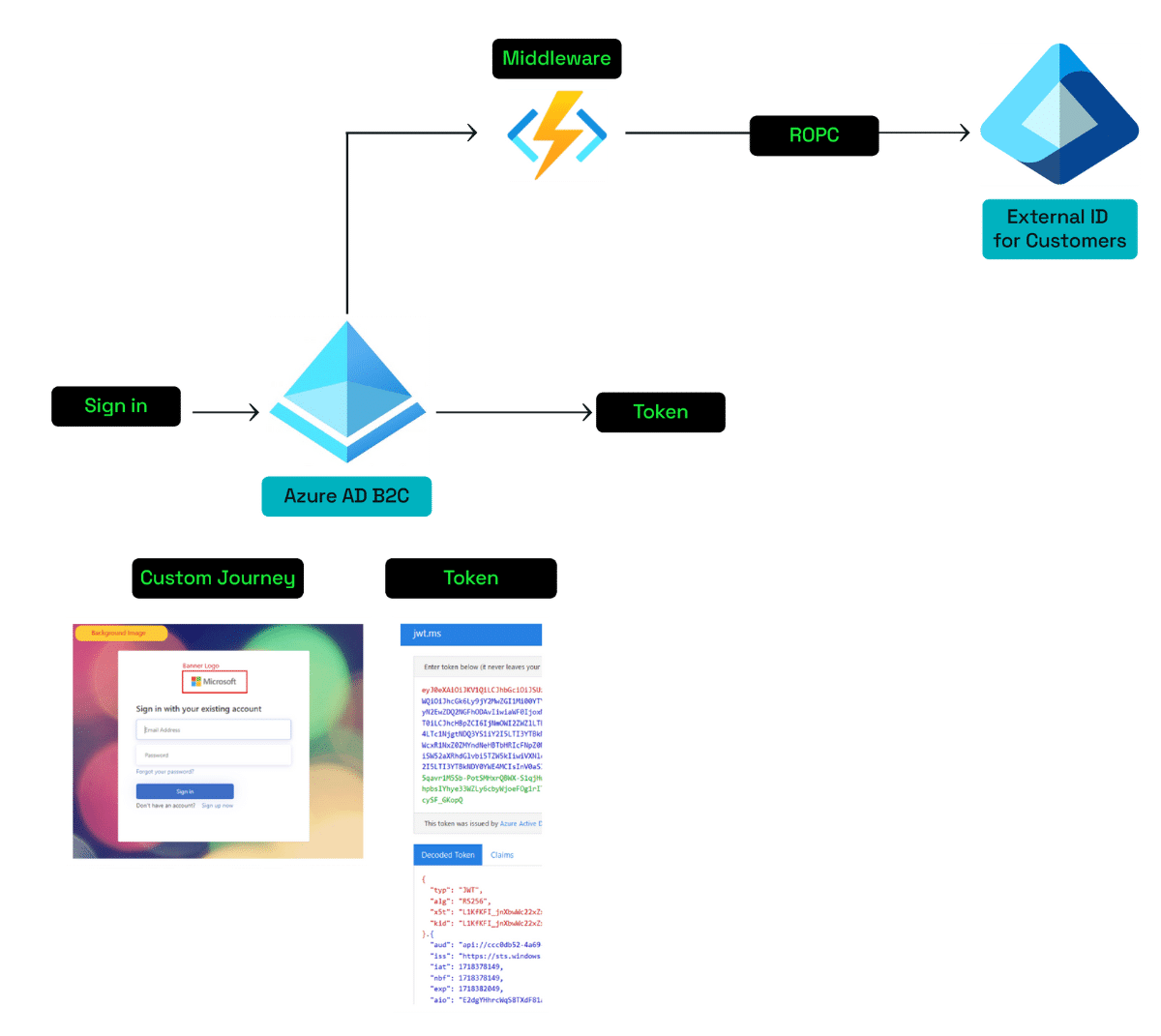
This type of integration can be used to build any kind of browser-delegated CIAM journeys which require the user to sign-in via a customised process that can’t be built in the new CIAM platform.
The token will be issued by Azure AD B2C. The user account on Entra External ID can be updated via Graph API through a middleware called from Azure AD B2C if needed.
Currently the ROPC endpoint is not officially supported in Entra External ID, however something similar could be achieved by using the native authentication APIs.
Via OIDC federation from Azure AD B2C to Entra External ID for Customers
Custom OIDC federation is currently not available in Entra External ID, but it will be very soon. When that happens, Azure AD B2C can be added as a custom OIDC identity provider in Entra External ID. The following diagram illustrates what this integration would look like:
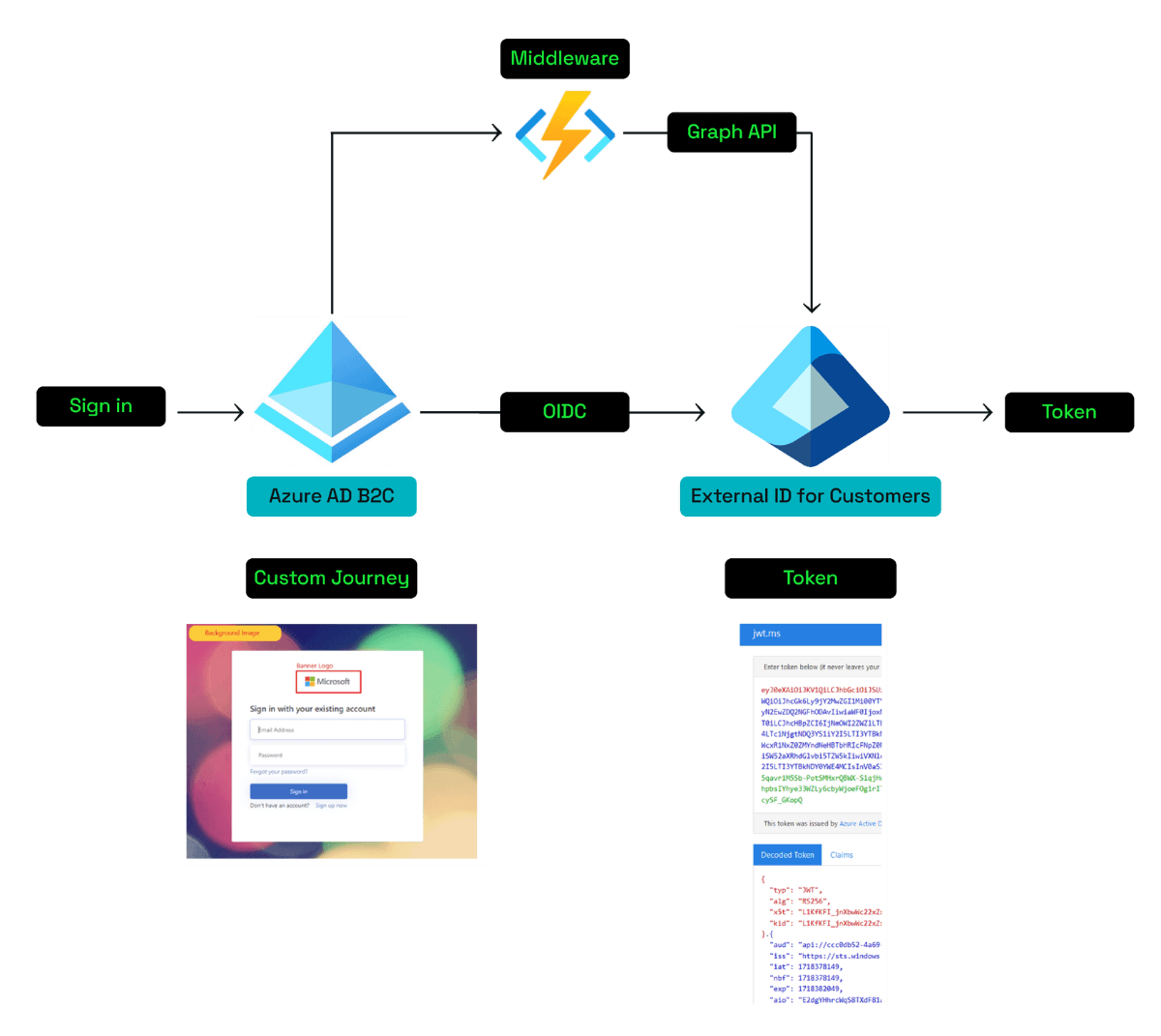
The customised experience of the journey will be created in Azure AD B2C, but the final token will be issued by Entra External ID.
Using this approach part of the user journey can be handled by Azure AD B2C and part of it can potentially be handled by Entra External ID. Individual steps can be migrated to Entra External ID when possible.
The two tenants can use a middleware which calls Graph API to interact with either of the directories if needed.
Via OIDC federation from Entra External ID for Customers to Azure AD B2C
This is the only OIDC federation currently possible between the two Microsoft CIAM platforms. Entra External ID can be configured as an external OIDC identity provider in Azure AD B2C and then used to sign in users to the B2C tenant.
The user data will be stored in Entra External ID, whereas shadow accounts would automatically be created in Azure AD B2C once a user signs in.
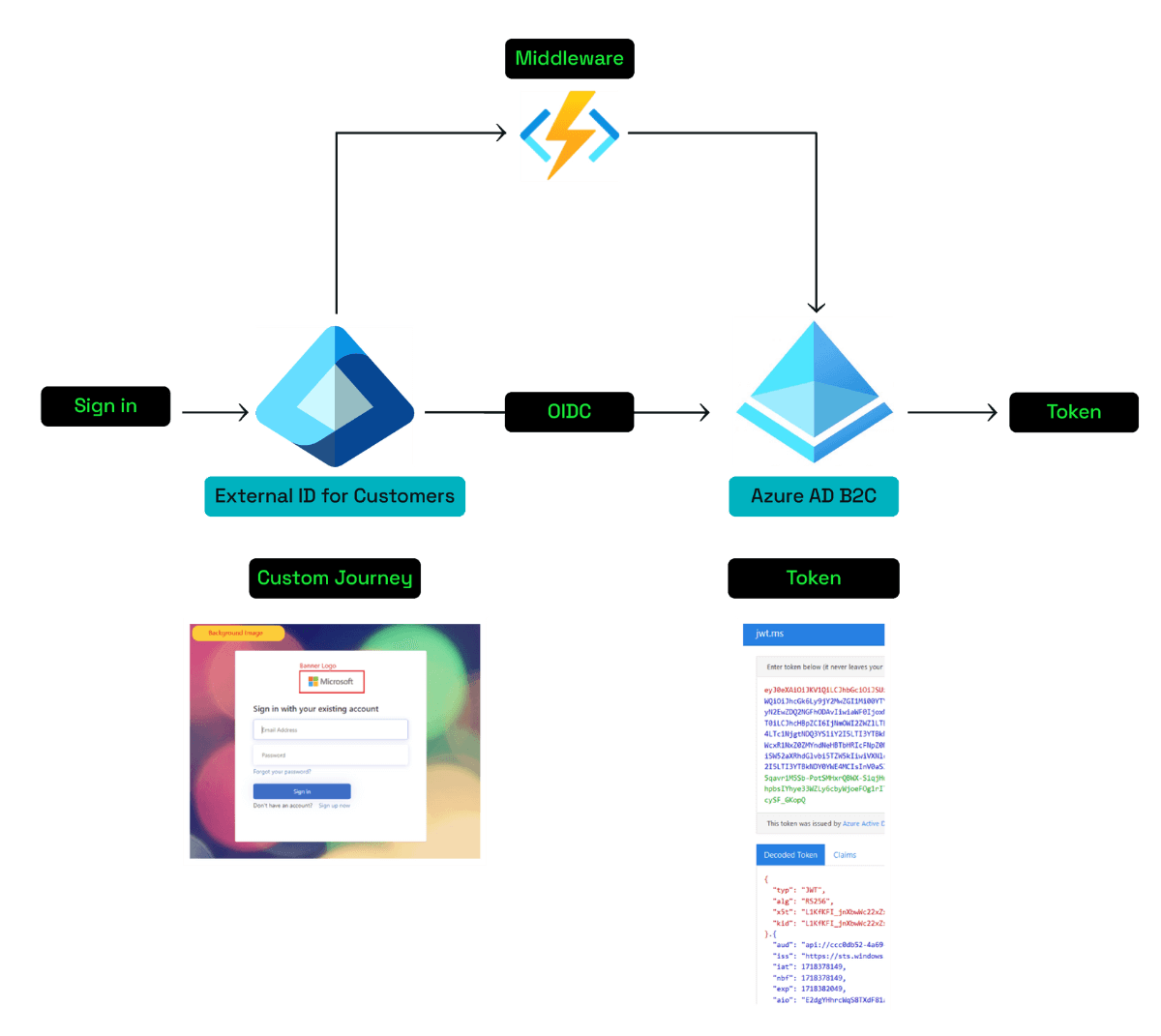
A middleware can be used to interact with either of the directories using Graph API.
Streamlining identity management with hybrid solutions
Hybrid solutions utilising Azure AD B2C and Microsoft Entra External ID for Customers are already feasible. And, for now, we certainly recommend a phased migration from Azure AD B2C as the most practical approach.
From an organisational perspective, we suggest evaluating current setups and strategically planning any migrations to minimise disruption and leverage new benefits.
Entra External ID is evolving, maturing, and increasing in functionality at pace. And that means ever more options when it comes to secure and flexible hybrid solutions.
So stay tuned, and watch this space.
Key takeaways
Microsoft Entra External ID is now in general availability and being developed as the next-gen CIAM solution.
Azure AD B2C offers more extensive UI customisation and detailed user journey controls, but Entra External ID is rapidly evolving its feature set.
Entra External ID supports more flexible, app-integrated authentication methods, reducing reliance on browsers.
A phased migration approach is recommended, utilising both Azure AD B2C and Entra External ID for seamless service transition.
Azure AD B2C will continue to be supported, allowing hybrid solutions that leverage both platforms.
Kocho’s external ID team can help enable the right migration strategy for your organisation.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier

Don't Miss
Great external identity resources
























Got a question? Need more information?
Our expert team is here to help.








