Discover how to smoothly transition from Azure AD Graph to Microsoft Graph before it’s too late. This guide covers key timelines, benefits, and actionable steps to ensure your organisation is ready for the change.
The end is near for Azure AD Graph.
Microsoft has announced its full retirement, and by June 2025, any applications not migrated will stop functioning. It’s essential to act now to avoid business disruptions.
In this guide, we’ll walk you through the timelines, why this migration is happening, and how to move to Microsoft Graph seamlessly, ensuring your identity management processes continue without a hitch.
Why Azure AD Graph is being retired
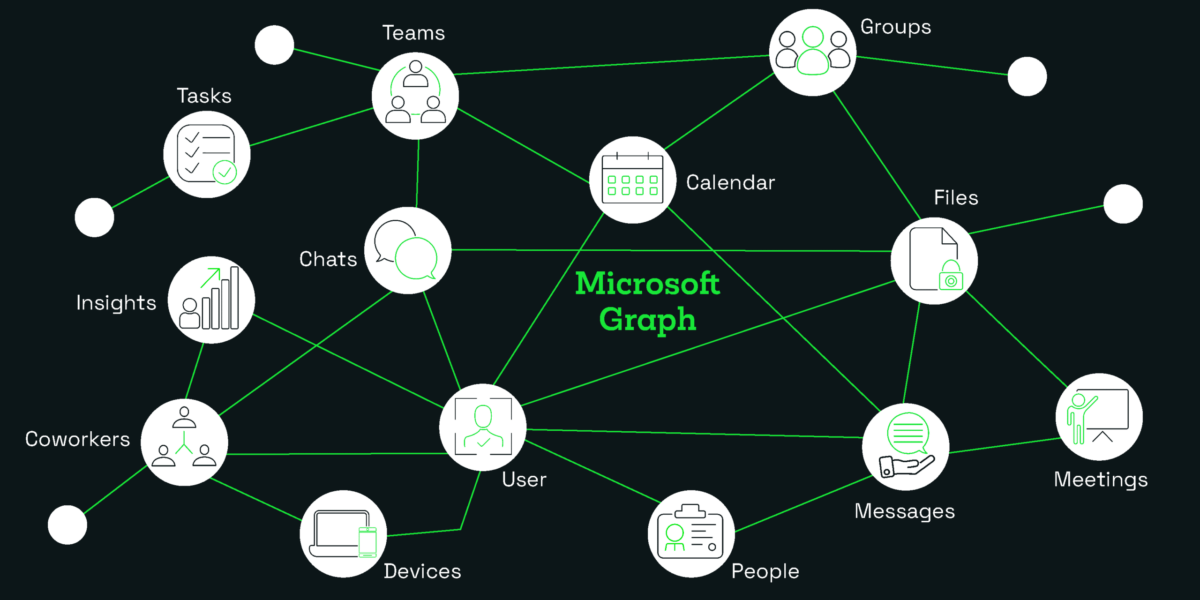
Azure AD Graph has served as a key API for identity management, allowing organisations to integrate their applications with Microsoft Entra ID. However, Microsoft Graph has emerged as a powerful and versatile successor, providing a unified endpoint for accessing a broader range of Microsoft services.
You see, unlike Azure AD Graph, which focuses solely on Entra ID, Microsoft Graph exposes REST APIs and client libraries to access data across Microsoft’s cloud services.
Such as:
- Microsoft 365 applications (e.g. OneDrive, OneNote, SharePoint)
- Enterprise Mobility + Security (e.g. Microsoft Entra ID, Intune, Advanced Threat Protection)
- Dynamics 365 Business Central Services
- Windows services (e.g. Activities, devices, notifications, Universal Print)
With added features, better security, and more resilience, Microsoft Graph is Microsoft’s “Best-in-Breed” API. It includes capabilities like identity protection, multitenant permissions management, privileged identity management, and broader integrations with Microsoft services.
Key dates for Azure AD Graph retirement
Here’s a timeline to help you understand the phased retirement of Azure AD Graph:
- June 30, 2023: Azure AD Graph enters its retirement cycle after a three-year notice period.
- August 31, 2024: New applications created after this date must explicitly opt-in for extended Azure AD Graph access. Existing applications will continue to function, but new ones won’t be able to use Azure AD Graph without this opt-in.
- February 1, 2025: Both new and existing apps must explicitly opt in for extended access to Azure AD Graph. Without opting in, these apps will break.
- June 30, 2025: The final retirement date. All Azure AD Graph access will end, and applications still relying on it will cease to function.


latest edition
Everything you need to know about Microsoft Entra
A clear, practical view of how Microsoft Entra works as a unified platform.
Expert guidance on modern identity design, security, governance, and Entra licensing.
Discover how you can:
- Run Entra as one coherent identity platform
- Apply end-to-end security and governance
- Modernise IAM safely, from MIM to AI-driven identity
Why migrate now?
Beginning the migration process now gives enough time to properly validate and roll out updates in a phased approach, minimising impact to the business.
Leaving it to the last minute puts unnecessary pressure on already busy IT teams. Pressure and time-sensitivities that could increase the likelihood of hurried and under-tested changes. Which in turn can lead to greater problems, increased risk, and potential issues for critical processes like the Joiner, Mover, Leaver lifecycles.
For instance:
- Joiners might not get accounts set up in time for their first day.
- Movers could end up with incorrect permissions, affecting their productivity.
- Leavers might remain active in systems, posing security and licensing risks.
Why Microsoft Graph is worth the switch
Microsoft Graph also offers improved capabilities, such as the ability to restore users and groups after deletion, enhanced security features, webhook notifications, and advanced licence management tools, making the transition beneficial beyond mere compliance.
By switching to Microsoft Graph organisations can benefit from:
- Broader integration: It interacts with not just Microsoft Entra ID but also a wide range of services across Microsoft 365, Dynamics 365, and Windows.
- Advanced security features: Identity protection, privileged identity management, risky users monitoring, and identity governance features like access reviews and terms-of-use management.
- Operational features: Microsoft Graph has richer capabilities for managing Microsoft 365 groups, external user invitations, and the ability to restore users and applications.
- Improved developer tools: More supported SDKs, broader OData queries, and smoother integration workflows mean developers can more easily leverage the power of Microsoft Graph.
Navigating third-party migration challenges
Migrating to Microsoft Graph can be more complex if your organisation relies on applications provided by external service providers or suppliers. These third-party applications might have different timelines for migration, and some may already have this process on their own roadmaps. Therefore, it’s prudent to check early in the process to validate their plans and, if necessary, request changes accordingly.
Have you checked with your software provider if they are using the Azure AD Graph API? If so, what are their plans for migrating to Microsoft Graph API?
Identity management can be complex and often incorporates various software tools to manage user lifecycles, from pre-hire to leaver and everything in between. It’s important to assess if you’re using any software or applications that interact with Entra ID via Azure AD Graph.
While some software might look at Entra ID for provisioning downstream systems, not all software that uses the Azure AD Graph API is necessarily part of identity management lifecycles. Some organisations may use Azure AD Graph for reporting purposes or even for training platforms.
Your step-by-step guide to a successful migration
Migrating from Azure AD Graph to Microsoft Graph might sound challenging, but with a clear plan, it can be managed effectively. Here’s a step-by-step guide to help:
- Plan ahead: Start planning early to avoid last-minute issues.
- Assess your current usage: Identify all applications, scripts, and services using Azure AD Graph in your organisation.
- Use the Microsoft Graph migration tool: This tool will help you locate dependencies on Azure AD Graph and suggest suitable Microsoft Graph alternatives.
- Update authentication: Switch to OAuth 2.0 if you’re still using the Azure AD Authentication Library (ADAL). Move to Microsoft Authentication Library (MSAL) for token acquisition.
- Review permissions: Ensure all your applications request the right permissions for Microsoft Graph.
- Update API endpoints: Replace Azure AD Graph endpoints with Microsoft Graph API equivalents.
- Handle API differences: Adjust your code to account for any structural differences in responses, including property names and data types. Leverage official Microsoft Graph SDKs for your preferred programming language to streamline integration.
- Test thoroughly: Conduct comprehensive testing to validate functionality post-migration. Testing should cover all use cases, especially those that are critical to business operations.
- Monitor and log: Implement robust logging and monitoring during and after migration to catch any issues quickly.
- Roll out gradually: Where possible, migrate in phases, starting with non-critical systems. This allows you to identify potential issues on a smaller scale before full rollout.
- Stay updated: Keep an eye on Microsoft Graph API updates and best practices to make sure your systems stay compatible and take advantage of new features.
Leveraging Microsoft Entra ID for migration insights
Microsoft Entra ID offers valuable tools to streamline your migration. By signing into the Microsoft Entra Admin Centre, you can access the Recommendations feature to quickly identify applications and service principals still using Azure AD Graph. This is a great starting point, helping ensure all your dependencies are accounted for before migration begins.
The Entra Admin Centre lists both applications and service principals that need to be addressed separately, ensuring nothing slips through the cracks. For most organisations, this approach will cover nearly all existing use cases, reducing surprises during the migration.
Avoiding service disruptions: best practices
A smooth migration is all about planning and thorough testing. Here are some best practices to ensure things go as planned:
- Identify and document changes: Make sure you know what needs to be changed, and have a step-by-step plan, including backout steps if something goes wrong.
- Validate in a development environment: Test your changes in a safe environment before rolling out.
- Use a user acceptance testing (UAT) environment: If available, test your changes in UAT before moving to production.
- Monitor closely: Keep an eye on performance and any anomalies after deploying changes, and communicate clearly with users if any downtime or disruption is expected.
Final thoughts: Why Microsoft Graph is the upgrade you need
With Azure AD Graph nearing end of life, the time for migrating to Microsoft Graph is here. But this isn’t just about avoiding service disruptions. It’s an opportunity to leverage a more powerful, secure, and feature-rich API for your identity management needs. By starting early and following the steps outlined above, you can ensure your migration is smooth and that your organisation is ready to take full advantage of Microsoft Graph’s capabilities.
If you need further guidance or expertise to help with the migration, then talk to us about how our team of Microsoft experts can ensure the process is as seamless as possible.
Key takeaways
Azure AD Graph is being fully retired by June 2025, and all apps must migrate to Microsoft Graph.
Microsoft Graph offers a broader range of features, better security, and enhanced resilience.
Start migration early to avoid service disruptions and minimise stress on IT teams.
Use Microsoft Entra ID tools to identify dependencies on Azure AD Graph for a smoother transition.
Comprehensive testing is crucial to ensure functionality remains intact during migration.
Migration should be done in phases, starting with non-critical systems where possible.
Keep updated on Microsoft Graph API changes to stay compatible and leverage new features.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
Next steps
Like this article?
Don’t forget to share it.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.








