Microsoft Global Secure Access (GSA) became generally available in summer 2024. In this Q&A, we answer the questions UK organisations are asking. From how it works in practice to the commercial and operational impact we’re seeing on the ground.
The old network perimeter is gone. Today, users connect from anywhere, and security has to follow them. That shift has pushed organisations toward cloud-based, identity-driven security models, known as Security Service Edge (SSE).
Microsoft entered the SSE market in 2024 with GSA becoming generally available. It promised to raise the bar for network access security and user experience. With the technology now live, we examine how that promise is playing out.
So, what is Global Secure Access?
Global Secure Access (GSA) is the unifying term for Microsoft Entra Internet Access and Microsoft Entra Private Access.
These components make up Microsoft’s cutting-edge SSE solution designed to deliver a smooth and secure user experience , a core component of Microsoft’s security platform that controls and protects how people connect to the internet and to private business apps.
GSA is part of Microsoft’s security platform that controls and protects how people connect to the internet and to private business apps.
Think of it as a checkpoint between the user and whatever they’re trying to reach. Before it lets anyone through, it checks:
-
Who they are (identity)
-
What they’re using (device)
-
Whether there’s any risk in the connection
It uses the same security rules engine that already protects Microsoft 365, so you can manage access policies in one place for your cloud apps, the public internet, and your internal systems.
Under the hood there are two services.
Microsoft Entra Internet Access
Entra Internet Access works as a Secure Web Gateway (SWG) in the cloud. Before allowing any outbound connection, it applies Conditional Access checks to confirm the user, device, and risk level.
It filters traffic using category and policy rules, and enforces Microsoft 365 tenant restrictions where required. Every action is logged with identity details, so you can investigate events in Microsoft Defender or Sentinel.
Traffic to Microsoft services is routed through Microsoft’s own backbone network. This often means faster, more reliable connections to Teams, SharePoint, and Exchange Online, with fewer delays or drop-outs.
And what benefits does Entra Internet Access offer?
Microsoft Entra Private Access
Entra Private Access is a Zero Trust Network Access (ZTNA) solution that provides a modern alternative to traditional VPNs. Instead of giving users access to an entire network, you define exactly which applications they can reach by domain name, port, or IP range.
A lightweight connector in your environment creates an outbound connection to the service, so there’s no need to open inbound firewall ports. It can also protect older protocols while still enforcing MFA and device compliance.
This removes the common VPN flaw where, once connected, users (or attackers) can see and access far more of the network than they actually need. By restricting access to only what’s required, you cut down the risk of lateral movement inside your environment.
Entra Private Access benefits?
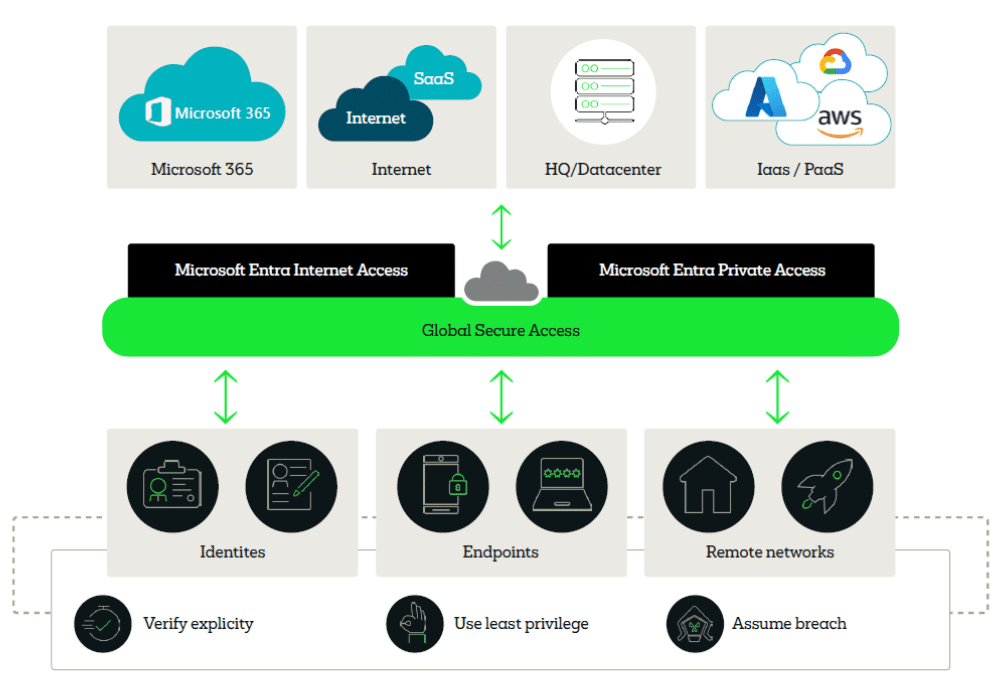
How do Internet Access and Private Access work together?
While each service has its own focus, they’re complementary:
- Internet Access secures outbound traffic to Microsoft 365, SaaS, and public internet resources.
- Private Access secures inbound connections to internal and private apps.
Together, they create a unified Zero Trust fabric for all network access.
Why did Microsoft develop Global Secure Access?
Work has shifted. Users connect from anywhere, most apps are SaaS, and the classic routed perimeter is more administrative overhead than risk control.
VPN concentrators and appliance‑style web gateways were built for a world of fixed sites and fat pipes. They introduce latency, create single points of failure, and hand out broad network access that attackers can move through if they get a foothold.
Microsoft built GSA to put access control where most customers already make trust decisions: Identity, device posture, and session risk in Microsoft Entra and Defender.
The aim is straightforward: policy at the point of access, delivered from the cloud, without having to own a network you no longer use as a perimeter.
Where does GSA sit within the broader Microsoft identity and security ecosystem?
GSA is an extension of Microsoft Entra.
Entra ID manages identity and access for users, devices, and workloads. Entra ID Governance adds lifecycle and compliance controls, while Micorosft Defender for Endpoint protects devices, and Defender for Cloud Apps acts as a Cloud Access Security Broker (CASB).
GSA knits these together at the network layer: Internet Access uses the same Conditional Access engine used by cloud apps, while Private Access extends the Entra application proxy.
Policies, logs and signals are surfaced in the Entra admin centre and can be ingested into Microsoft Sentinel for Security Information and Event Management (SIEM). For organisations already using Microsoft Intune for device management and Defender for Endpoint for threat protection, adding GSA consolidates the stack under one vendor.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
What licencing do I need for Global Secure Access?
Before you decide if GSA is the right move, it helps to know exactly what licences you’ll need and what they cost in the UK. Here’s a quick reference table:
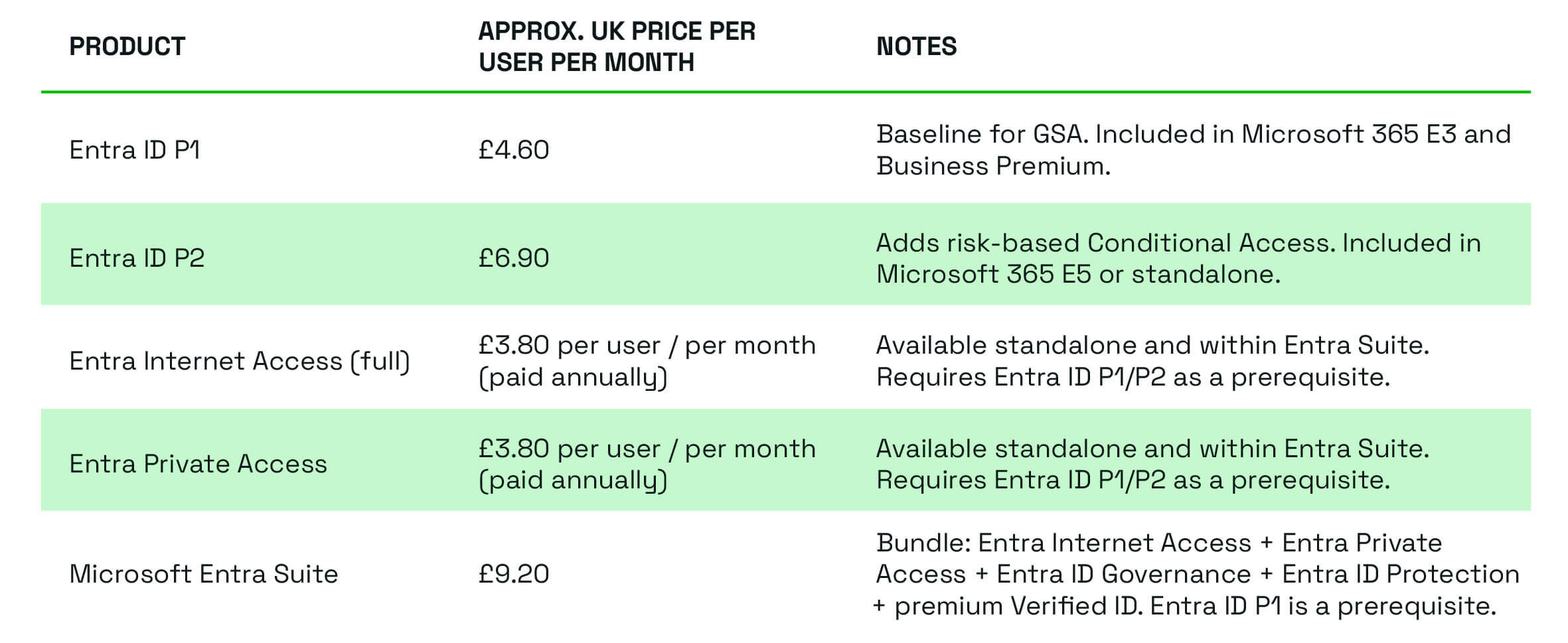
Note: Prices exclude VAT and vary under CSP or Enterprise Agreement. Licensing enforcement for Entra Internet Access and Entra Private Access applies; ensure users are licensed for the services they use.
Is Global Secure Access part of Microsoft Entra Suite?
Yes. Entra Suite combines both GSA services with Entra ID Governance and Identity Protection in one subscription.
It lets Microsoft-focused organisations manage access, lifecycle, and risk from a single platform. If you only need one access type, buying it separately might be cheaper. If you want both plus governance, then Entra Suite makes buying, budgeting, and running day to day far simpler, with all policies managed in one place.
Commercial and operational questions
If you’re considering the value of GSA in your estate, then you’ll likely have some or all of the following queries.
How does GSA compare to VPNs and traditional secure web gateways?
VPNs take an all-or-nothing approach. Once connected, a device can usually reach anything the network route allows. Security teams try to limit this with Access Control Lists (ACLs) and complex network segmentation projects, but these are hard to finish and harder to keep up to date.
GSA flips that model. Instead of opening the network, it only grants access to a specific application after the user, device, and session have passed policy checks.
For internet access, older secure web gateways depend on network location and Proxy Auto-Configuration (PAC) files to decide what’s allowed. GSA uses the same Conditional Access rules you already apply to SaaS apps, so decisions are consistent and easier to understand.
In practice, you avoid the slow “hairpin” routing through data centres and the downtime linked to appliance upgrades. You also get cleaner, user-attributed logs which makes investigations faster and compliance audits simpler.
Does GSA support Transport Layer Security inspection?
Microsoft added TLS inspection to Entra Internet Access in May 2025, and it’s currently in public preview. The feature securely decrypts HTTPS traffic in real time, applies identity-driven policies, and then re‑encrypts it before sending it on. This allows Conditional Access rules and web filtering to work not just at the domain level, but inside encrypted sessions.
How could it benefit you?
- Gain visibility into traffic that would otherwise be hidden, helping detect shadow IT and risky behaviour.
- Apply fine‑grained controls, such as blocking specific actions within approved SaaS apps.
- Make sure even encrypted traffic meets your organisation’s security and compliance requirements.
Can I deploy Internet Access and Private Access separately?
Yes, for many organisations, a phased rollout is often the most effective approach.
Commercially, it lets you:
- Focus budget on high-impact areas first, such as securing Microsoft 365 and SaaS traffic.
- Spread costs over multiple cycles.
- Prove value early, building the case for wider adoption.
Operationally, it helps you:
- Reduce change risk by addressing one access type at a time.
- Fine-tune Conditional Access policies before scaling.
- Deliver quick user experience wins while preparing more complex private access configurations.
This way, you see measurable improvements in security and productivity within weeks, without overloading teams or budgets.
So, can we run GSA alongside other vendors?
Yes – a coexistence strategy can support a gradual shift towards the longer‑term goal of consolidating and unifying tools, rather than forcing a big‑bang replacement.
Commercially, the eventual savings tend to come from three main areas:
- Retiring VPN capacity and its support contracts
- Removing appliances and associated change windows
- Cutting investigation times thanks to identity‑attributed logs.
By modelling these gains in a TCO exercise, you can build a clear business case for consolidation when the time is right.
Who’s a good fit for Global Secure Access?
GSA is a strong fit if you’re Microsoft‑first, already using Entra ID, Intune and Defender, and looking to phase out VPN in a controlled way.
It’s particularly effective for organisations that prefer to consolidate identity, endpoint and access with a single vendor, as you gain tighter signal sharing and smoother policy enforcement out of the box.
What’s next for network access, and how does GSA fit in?
As digital transformation accelerates, securing access to resources from anywhere is now an operational necessity. New threats and constant change mean organisations need solutions that can adapt just as quickly.
In practice, Global Secure Access reflects Microsoft’s push to unify network access controls under the same identity‑centric model already used in Microsoft 365 and Azure.
Its combination of cloud delivery, Zero Trust principles, and tight integration with existing Microsoft tools means it can slot into established environments with minimal disruption. For many organisations, this could streamline policy enforcement and monitoring, though its effectiveness will depend on how well it’s configured and aligned with existing security operations.
Ready to learn how to configure Global Secure Access for your organisation?
Did you know that Kocho are an official Microsoft launch partner for Global Secure Access?
So, if you’re looking to revolutionise your network security posture, talk to our team of experts and discover how it could transform your network security and your team’s productivity.


Free Guide
Everything you need to know about Microsoft Entra
The most comprehensive guide to Microsoft Entra. Over 40 pages. Plus, Microsoft licensing simplified.
Discover how you can:
- Cut costs by removing 50% management effort
- Elevate security – reduce breach chances by 45%
- Automate provisioning to ensure compliance
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.








