With end users persistently targeted by increasingly sophisticated phishing attacks, business email compromise (BEC) continues to be a prevalent menace. Discover the recent trends and prevention tactics that our managed security operations team have identified.
BEC incidents serve as a precursor for various cyber attacks, ranging from payment hijacking to ransomware.
Consider that 80 – 95% of all cyber attacks originate from phishing and that Microsoft reported an average of 156,000 BEC incidents per day in 2023 and you can see why this is a big deal.
In fact, every significant recent ransomware attack would have started with a phishing email.
The evolving face of BEC
While the days of simple email address spoofing have given way to more complex techniques due to improved defences, it’s become increasingly challenging to detect and protect against phishing emails.
Attackers are now sending phishing emails from legitimate domains and sometimes these can be from people who users regularly interact with.
This makes their fraudulent requests for information or actions seem much more believable. Which in turn increases the chances of a successful attack.

There were an average of 156,000 BEC incidents per day in 2023
Detecting phishing is getting harder. So, what can be done?
At Kocho, our strategy is to detect malicious actors throughout the entire attack timeline. This means that even if an initial access vector, such as stolen credentials, bypasses our initial detections, we have additional analytics in place to identify unusual or suspicious behaviour.
One technique commonly used by adversaries is the creation of ‘Email Hiding Rules’.
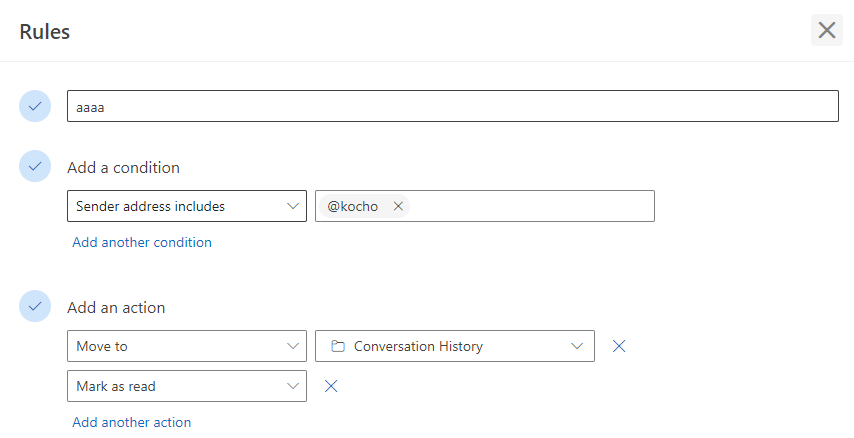
These are mailbox rules set up on a compromised mailbox to divert certain emails to hide the attacker’s activities.
By doing this, the attacker can maintain access to the account and continue their operations unnoticed.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Observing recurring tactics
After observing several different BEC incidents, attackers seem to follow the same suit when creating these mailbox rules.
The created rules will often divert emails to default Outlook folders. Typically, these will be folders never used by the end user.
The folders most commonly abused are:
- RSS Feeds
- RSS Subscriptions
However, it’s worth bearing in mind that other default folders are now being used too. We’ve recently noticed that folders such as Conversation History and Junk Email have also been leveraged by attackers.
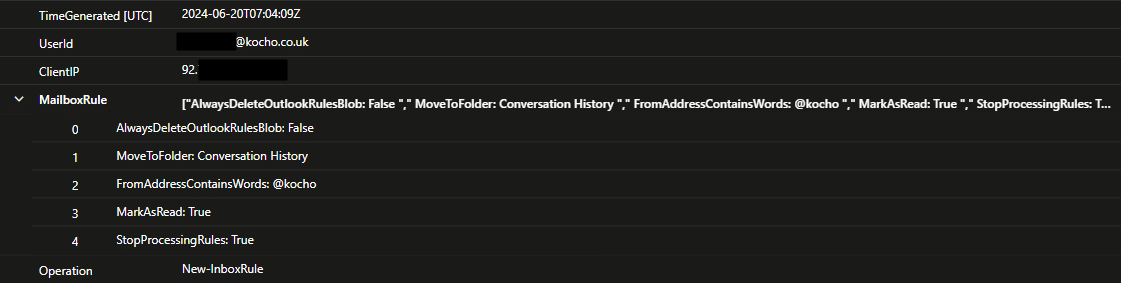
Detecting malicious email rules
Email hiding rules continue to be a prominent behavioural technique employed by adversaries. Detecting this activity is helping to prevent attacks from escalating, while minimising false positives.
And while it can be a painstaking task, filtering out normal user behaviour and minimising false positives is crucial for any Security Operations team.
Here are some rule properties to be on the lookout for.
Operations
- New – InboxRule
- Set – InboxRule
Specifying the following folder names can help pinpoint malicious activity:
- RSS Feeds
- RSS Subscriptions
- Deleted
- Conversation History
- Junk Email
Key takeaways
BEC is a major threat to organisations with email-targeted phishing a primary tactic for cyber attacks.
Modern phishing techniques make it increasingly harder for security teams to detect attacks.
‘Email hiding rules’ are a common tactic used by attackers to divert emails to default Outlook folders, concealing their activities.
Effective detection of malicious mailbox rules involves monitoring for specific rule properties and unusual folder usage while minimising false positives.
A comprehensive defence strategy, including behavioural analytics and automated alerts, is essential for protecting against BEC and related cyber threats.
Want to know more?
If you’d like to understand more about how Kocho SecOps detects and responds to this behaviour, reach out to our team for a detailed consultation. Our expertise in managing and mitigating BEC attacks can help safeguard your organisation against ever-evolving, always improving cyber threats.
And please join our mailing list for the latest cyber security news, technology updates, and regular tips to keep protected against advanced threats.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great protection starts here
Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
You’ll get:
- Notifications of critical vulnerabilities
- Recommendations to reduce your risk level
- Expert advice to defend against new threats
























Got a question? Need more information?
Our expert team is here to help.








