Legitimate file-sharing platforms like Dropbox are being weaponised by cybercriminals. Learn how attackers are exploiting these services to develop convincing attacks. And gain practical tips to identify and defend against these threats.
Kocho’s SOC team has observed a surge in phishing campaigns exploiting legitimate external file-sharing platforms.
While SharePoint and OneDrive abuse remains a concern, Dropbox-based attacks are now dominant.
With thousands of organisations worldwide relying on Dropbox, this twist on traditional email phishing has become a popular vehicle for threat actors.
Without user training and education, these campaigns have a high success rate, frequently deceiving users into disclosing identity-based information.
A common example: ‘Legitimate’ Microsoft file sharing
Phishing campaigns can vary widely in style, even when using the same platform. As with traditional phishing campaigns, some are more elaborate than others.
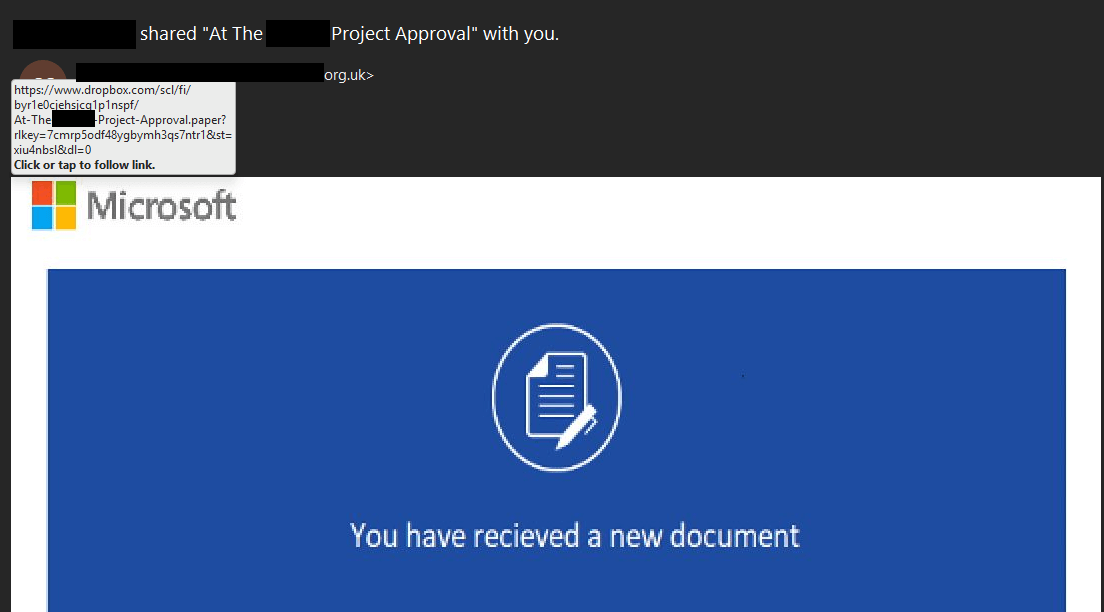
A common and less sophisticated example follows a familiar pattern. For example, a malicious email with the subject: “Jack Fisher shared ‘Kocho SecOps Project’ with you.”
To convince users that it’s a legitimately shared Microsoft file, the email will typically include a Microsoft logo in the header.
Hovering over the image reveals the full URL (see below), which redirects to Dropbox. Further analysis would confirm that the file is actually hosted on Dropbox.
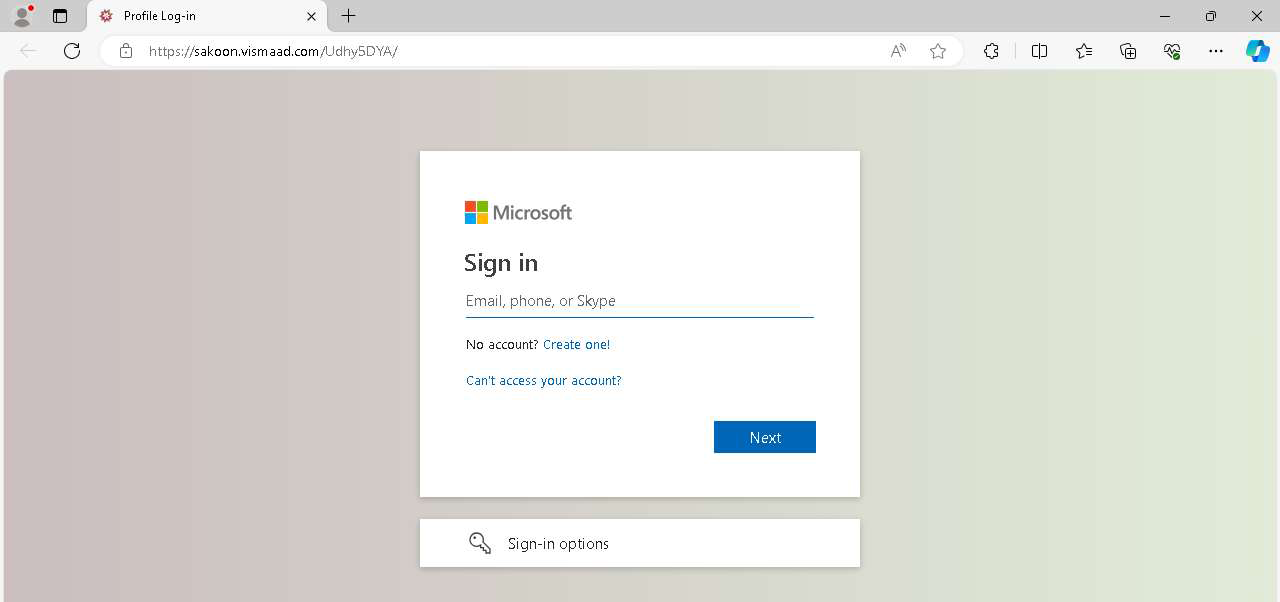
All links lead to a Microsoft credential harvesting page:

This is a simple approach. However, we are seeing more elaborate and creative methods, with attackers adding an extra step to social engineer end users (scroll down to see an example).


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Getting creative: Legitimate Dropbox accounts
Threat actors are creating legitimate Dropbox accounts to share documents (see email below).
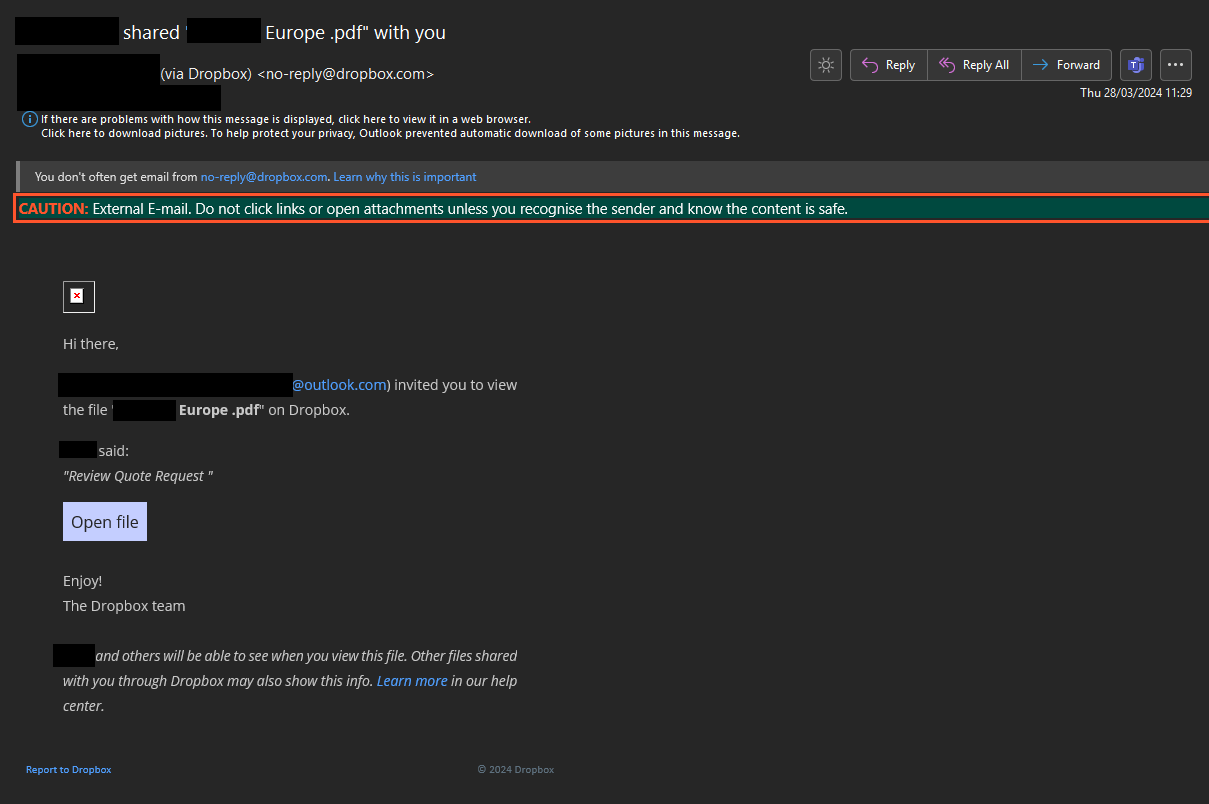
This is clearly far more convincing, as it’s coming from the actual platform.
This tactic also often bypasses security monitoring, as the emails pass authenticity checks.
The key telltale sign is the email used for Dropbox file share. For example, instead of using the email [email protected] the attacker may create an account with [email protected].
There are likely two reasons attackers use this approach:
- They don’t have access to the user’s email account.
- If the account is compromised, the user remains unaware that their account was used to sign up for Dropbox.
At a quick glance, a user will see a legitimate Dropbox sender and recognise a partner, colleague, or supplier’s name in the body of the email.
By relying on social engineering to deceive the user, the email appears more authentic – and is therefore more likely to be successful.
The final step is always the same: a Microsoft credential harvester that steals passwords and live session tokens, which are then used to gain access to the targeted accounts.
Options to protect your business
To protect your organisation from this type of attack, you should consider one or more of the following options:
- Add KQL query into Microsoft Sentinel
- Microsoft Entra Identity Protection
- Block access to external file sharing platforms
- User education and training
We cover each of these in a little more detail below.
Add KQL query into Microsoft Sentinel
The following KQL query can be used to hunt for similar emails in Microsoft Sentinel:
| where TimeGenerated > ago(1d)
| where SenderFromDomain has “dropbox.com”
| where EmailDirection =~ “Inbound”
// Detect keywords
| where Subject has_any (“shared”, “proposal”, “project” , “agreement”, “important”, “urgent”)
| project TimeGenerated, SenderFromAddress, RecipientEmailAddress, Subject, DeliveryAction, NetworkMessageId
// Join on UrlClickEvents to find any user clicks
| join kind=inner UrlClickEvents on NetworkMessageId
Microsoft Entra Identity Protection
The P2 license of Microsoft Entra ID Protection is essential if you want to protect your organisation from modern phishing attacks like these.
Risk-based conditional access uses machine learning to detect risky sign ins, and automatically block unauthorised access or add additional security features (e.g. MFA) to confirm actions are legitimate.
Download ‘The Complete Guide to Microsoft Entra’ to learn more about Entra’s key security tools.
Block access to external file sharing platforms
The most extreme option.
While this approach does give you a high level of control – restricting users to trusted and approved platforms – it does introduce barriers for users.
You’ll need to balance user productivity with security needs, and ensure appropriate alternative platforms are in place.
User education
Use articles like these to keep staff informed about evolving threats and security best practices.
Regular training and education is key to helping employees recognise the latest phishing attacks – and minimising the risk of a data breach in your organisation.
Kocho can support you with individualised phishing and security awareness training programmes. Get in touch for more information.

Let's talk!
Real partnership. Microsoft expertise. Complete transparency.
Book a free Discovery Call and learn more about our AI-powered security operations service, XDR Rapid Protect.
Get more information on:
- AI-powered rapid protection, from day one
- Dedicated Microsoft experts, by your side
- Powerful, intuitive reporting tools
- Collaboration and transparency as standard
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great protection starts here
Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
You’ll get:
- Notifications of critical vulnerabilities
- Recommendations to reduce your risk level
- Expert advice to defend against new threats
























Got a question? Need more information?
Our expert team is here to help.








