Cyber criminals are waging a new kind of war, but too many Security Operations Centres (SOC) are still fighting yesterday’s battles. Discover why it’s time to cease the siloed approach and stop attackers exploiting the gaps.
In cybersecurity, there’s often a sense that attackers are ahead of the game. Pushing the boundaries with advanced tools, innovative tactics, and AI.
But it often comes down to a mismatch between the way attackers and defenders operate.

Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.
Attackers excel at exploiting the interconnected nature of systems and networks, leveraging graph-based strategies to outmanoeuvre defenders. In contrast, many SOCs remain reliant on siloed, linear approaches.
It’s an outdated model that creates structural weaknesses attackers are quick to exploit.
For SOCs to stay ahead, they must adopt the strategies of their adversaries. Making the shift from fragmented defences, to unified, proactive strategies.
But what’s holding them back?
The challenge of shifting from silos
We know that a lot of SOC teams are already aware of the need to move away from traditional silos but come up against significant barriers to making the change.
Such as:


Free Guide
The Ultimate Guide to Microsoft Security
The most comprehensive guide to Microsoft Security. Over 50 pages. Microsoft licensing and pricing simplified.
Discover technologies that:
- Detect and disrupt advanced attacks at machine-speed
- Tap into the world’s largest threat intelligence network
- Protect identities, devices, and data with ease
So, how can SOCs break the silos and strengthen their security posture?
Well, it’s really a case of grasping the nettle and identifying this as a necessary change.
Which means we first need to establish the value and benefits that will come from the investment required.
And what of the potentially devastating costs of continuing with tactics that attackers can bypass with increasing ease?
The costs beyond the breach
As any organisation who’s suffered a breach will attest, there’s not just an initial crisis to control.
There are also considerable knock-on effects that come with big costs.
- 66% of consumers lose trust in a company after a data breach.
- Publicly listed companies experience an average 7.5% drop in stock prices after an attack.
- UK businesses have endured £44 billion in cyberattack-related losses over the past five years.
This is without factoring in the cost of downtime, lost productivity, or the potentially devastating delays in new projects.
Or the emotional impact on IT teams dealing with all this fallout, in a sector where 68% of cybersecurity professionals are already reporting burnout.
How attackers exploit graph-based thinking
Today’s cyber attackers see organisations as a web of interconnected systems, users, and data. Their dynamic approach exploits these connections to achieve their goals.
Attackers exploit lateral movement across IT systems
After gaining an initial foothold, via phishing or weak passwords, attackers exploit relationships to move across systems, using credentials or permissive access to escalate privileges.
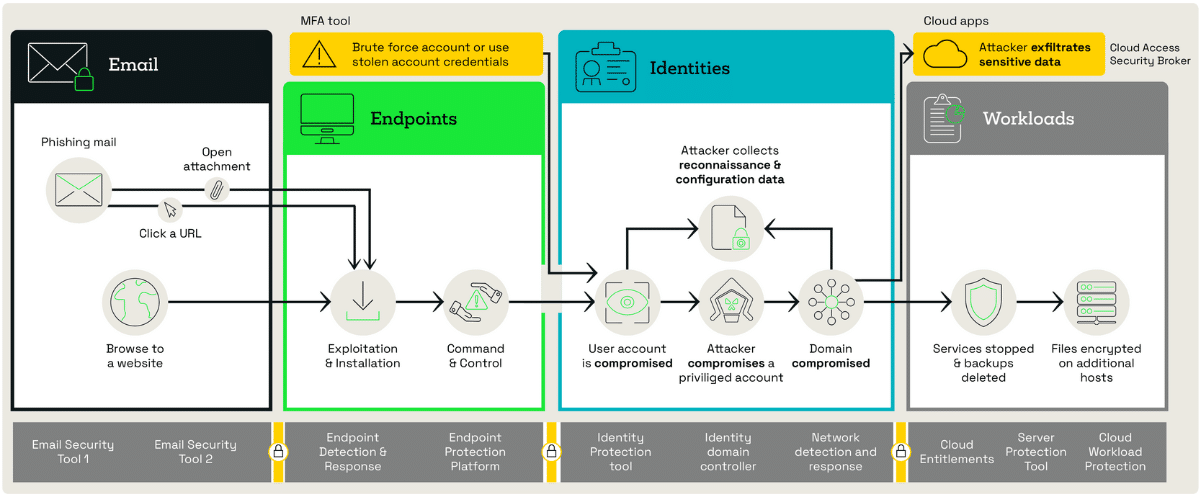
Chaining vulnerabilities together to bypass traditional defences
Attackers combine multiple minor vulnerabilities to create a pathway to their target.
Threat actors outmanoeuvre SOCs with dynamic adaptation
Attackers constantly map their environment, pivoting strategies and finding new paths as defenders block them, leveraging their holistic view against siloed defences.
Against SOCs still operating in silos, this graph-based approach is inherently more agile, offering attackers a significant edge.
By focusing on relationships rather than isolated nodes, attackers can exploit gaps that siloed tools and workflows fail to address.
For example:
- A poorly segmented network can act as a highway for attackers moving laterally.
- Overlapping permissions across different systems can create hidden pathways for privilege escalation.
- Disconnected monitoring tools can miss patterns of behaviour that span multiple domains.
5 reasons to adopt graph-based security in your SOC
Graph-based security can change the dynamics in the cat and mouse battle between cyber attackers and defenders.
By reflecting the interconnected approach used by attackers, organisations can strengthen their defences in key ways:
- Proactive defence
Graph-based security enables defenders to map potential attack paths and spot vulnerabilities early. By visualising connections between users, systems, and data, security teams can cut off attackers before they gain traction, shifting from reactive responses to proactive risk management. - Enhanced threat hunting
Unlike traditional tools that detect isolated threats, graph-based solutions (e.g., Microsoft Security Copilot) identify patterns across the network. By linking anomalies such as unusual logins and data access, SOC teams can uncover coordinated attacks faster and with greater precision. - Cost and tool consolidation
Organisations often manage numerous, disconnected security tools. Graph-based platforms unify these functions, reducing tool sprawl, cutting costs, and simplifying operations—freeing resources for strategic initiatives instead of maintenance. - Simplified management
A centralised, graph-based view of the security landscape provides insights that siloed systems lack. With automated analysis and prioritisation, teams can focus on high-impact tasks, improving risk management and incident response. - Greater resilience to advanced attacks
Sophisticated threats like ransomware and supply chain attacks exploit interconnected weaknesses. Graph-based security exposes hidden risks and blocks lateral movement, increasing resilience to multi-step attack strategies.
Microsoft’s Secure Futures Initiative: the blueprint for graph-based security
Microsoft’s Secure Future Initiative serves as a roadmap for embedding security across every layer of an organisation’s operations.
With principles like “secure by design” and “secure by default,” Microsoft is advocating for holistic, interconnected strategies that stand up to advanced threats.
This effectively lays the foundation for a series of innovative technologies that make the shift to graph-based security practical and achievable for organisations of all sizes.
The path forward: A strategic fight against cyber threats
To outpace modern attackers, organisations must move beyond siloed security approaches and embrace interconnected, proactive strategies.
Microsoft’s innovations, such as Security Copilot and the extended capabilities of tools such as Defender XDR and Sentinel, provide the tools needed to transform cybersecurity. These solutions enable organisations to detect threats earlier, respond faster, and reduce complexity, all while cutting costs and strengthening resilience.
However, technology alone isn’t enough. Partnering with an experienced security provider or external SOC team can be the key to unlocking these benefits. The right partner will guide implementation, optimise operations, and provide specialised expertise, ensuring that the full value of these tools is realised.
Did you know?
Kocho are a leading global Microsoft security partner with Verified Managed Extended Detection and Response (MXDR) solution status.
Talk to us today and find out how our experienced SOC team can help your organisation adopt modern graph-based security that protects against modern threats and drives greater cost-efficiency across your IT estate.
Key takeaways
Cyber attackers exploit interconnected systems while siloed SOCs struggle to keep up.
Legacy systems and tool sprawl hinder SOCs from adopting integrated, graph-based defences.
Graph-based security empowers SOCs to identify attack paths and prevent lateral movement.
Microsoft innovations, like Security Copilot, simplify complex threat detection and response.
Embracing proactive, interconnected strategies strengthens resilience against advanced threats.
Partnering with experts ensures seamless implementation of modern cybersecurity solutions.
The costs of siloed security far outweigh the investment in unified, proactive defence models.


Free Guide
The Ultimate Guide to Microsoft Security
The most comprehensive guide to Microsoft Security. Over 50 pages. Microsoft licensing and pricing simplified.
Discover technologies that:
- Detect and disrupt advanced attacks at machine-speed
- Tap into the world’s largest threat intelligence network
- Protect identities, devices, and data with ease

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.








