
Blog | 15-minute Read
What is a security operations centre (SOC)?

Anna Webb
Head of Global Security Operations
Published: 23 October 2020
The words ‘security operations centre’ or SOC have quickly become synonymous with cyber security. But what does a SOC do and what are the benefits of having one?
As the person responsible for cyber security in your organisation, you may find yourself wondering what exactly a SOC is – and if you haven’t got one, should you?
You may already have a security information and event management tool (SIEM) with security staff monitoring for threats and security incidents, but does that alone constitute a SOC?
If you’re already in the market for a security operations centre, whether developed inhouse or managed via a third party supplier, what should you be looking for in a ‘good’ SOC? And what considerations need to be made?
This blog will look to answer these questions and provide an understanding of the ever-evolving world of the SOC – why you might need one, what that might look like, and how to begin making it a reality.
The SOC explained: What you need to know
Most people imagine a SOC as a collection of hooded figures in a dark room with large monitors on the wall and a map of the world showing hotspots of cybercrime in progress.

In reality, a SOC is much more than that. A fully implemented SOC is a centralised capability that consists of three main elements – people, process, and technology.
Through the combination of these elements, the SOC is responsible for monitoring and analysing a company’s security posture using a dedicated SIEM or SOAR tool. Threat monitoring, incident response, and mitigation activities are at the heart of SOC capability.
Let’s take a look at those three main areas in more detail.
People
Whether you choose to have an inhouse SOC or opt for an outsourced option through a managed service, it is possible to have a great technical solution but limited capability.
You could be using Microsoft Sentinel, which has many great features for spotting potential security issues in your infrastructure. But if you don’t have people with the experience, skills, training or time to use that technology properly, then you won’t get the best out of your solution.
Here are some typical staff roles that exist within a SOC:
SOC Manager
As head of the SOC, the managerial and leadership responsibilities typically fall to the SOC Manager. They are responsible for recruitment, budgeting and setting the priorities of the SOC.
SOC Analyst
An organisation will have a team of analysts who operate at different levels within the SOC.
- Tier 1: Entry-level analyst with little or no commercial cyber security experience. Usually, a university graduate or an individual who has a keen interest in cyber security, self-taught but has been working in another IT-related role.
- Tier 2: More experienced than a tier 1 with regards to industry experience, usually with three to five years’ experience in SOC or security-based roles.
- Tier 3: The most experienced SOC analysts who typically have many years of experience in the cybersecurity profession. They usually act as mentors to tiers 1 and 2 and are sometimes used by a company in a consultative capacity to support clients with complex incident investigations, threat hunting, and SIEM optimisation.
The analysts use a wide range of monitoring services to track and capture alerts which are ranked by severity.
When an issue is spotted, they react accordingly following the organisation’s incident response plan.
All SOC analysts are responsible for reviewing incidents and determining the root cause. Initial incident monitoring is normally carried out at tier 1 and then escalated to tier 2 and 3 analysts depending on response times and agreed SLAs.
Tier 2 and tier 3 analysts have more of a focus on:
- Threat hunting
- Guided remediation and response
- Emerging threats and vulnerabilities
Tier 3 analysts can also provide information and guidance on best practice to internal and external clients.


Free Guide
In-house vs. outsourced security: Which is right for you?
62% of organisations say their security teams are understaffed.
Download your 35-page comparison guide to discover:
- The real cost of building an in-house SOC
- Key questions you must ask before investing
- Hidden risks that could catch your business out
Service Delivery Manager
A role more commonly found in a managed service SOC, the Service Delivery Manager is the conduit between the SOC technical staff and their clients.
They are responsible for operational, management and performance reporting for clients. They also serve as the escalation point for any issues that the client may have with the SOC.
Some SOCs may also have an Incident Responder and Compliance Auditor, but these are roles usually seen in more mature SOCs with many staff and clients. Ordinarily, these roles are incorporated into one of the three mentioned above.
Process
Having a team of experienced, highly qualified, and vigilant analysts is a good foundation for any SOC, but their expertise and skill needs to be underpinned by a set of clearly defined and robust processes.
Without these in place, you will find that your SOC lacks direction and fails to produce consistent outcomes.
This does not mean that processes should exist just for the sake of it. What it does mean is that, at a minimum, you should have processes that cover areas such as:
- Incident management
- Incident response and forensics
- Data breach
- Emerging threats
- Threat awareness
- Disaster recovery and business continuity
You will also need to think about processes that are more people focused and deal with analyst development, such as:
- Training
- Personnel assurance/security vetting
- Skills matrix
- Career framework and progression
- Operational effectiveness testing
There are also the human resource processes to bear in mind, such as:
- Operating hours
- Analyst breaks
- Shift working
- On-call
- Annual leave cover
- Bank holiday cover
These processes don’t need to be lengthy, but they do need to capture the necessary detail to ensure that everyone in the SOC is working together and understands the requirements of the role.
Technology
Now let’s look at the technology that underpins the SOC.
There are several products on the market that an organisation can implement.
Traditional SOC technology has required physical on-premises servers or appliances for the collection and analysis of data from a business’ networked devices.
However, cloud-based security tools are now the preference as more businesses move their data to the Cloud.

Costs can vary between SIEM products, depending on how they’re run. Prices are usually based either on the number of log events processed per second or the size of the logs ingested and stored.
Most third parties offer a tiered pricing model (depending on the size of your organisation). This is based on what logs you want to ingest and review, what alerting or notifications you want to get out of the tool, and how much of that data you want to store and for how long.
There are also additional machine learning and artificial intelligence offerings available that develop and provide automation which can affect cost also.
There are lots of technical elements to consider, but fundamentally what is a SIEM or SOAR?
What is a SIEM?
The term SIEM was coined by two people from Gartner, Mark Nicolett and Amrit Williams, in 2005. SIEM stands for security information and event management.
It is where software products (or technology) and services combine security information management (SIM) and security event management (SEM) to provide real-time analysis of alerts generated by applications and network hardware.
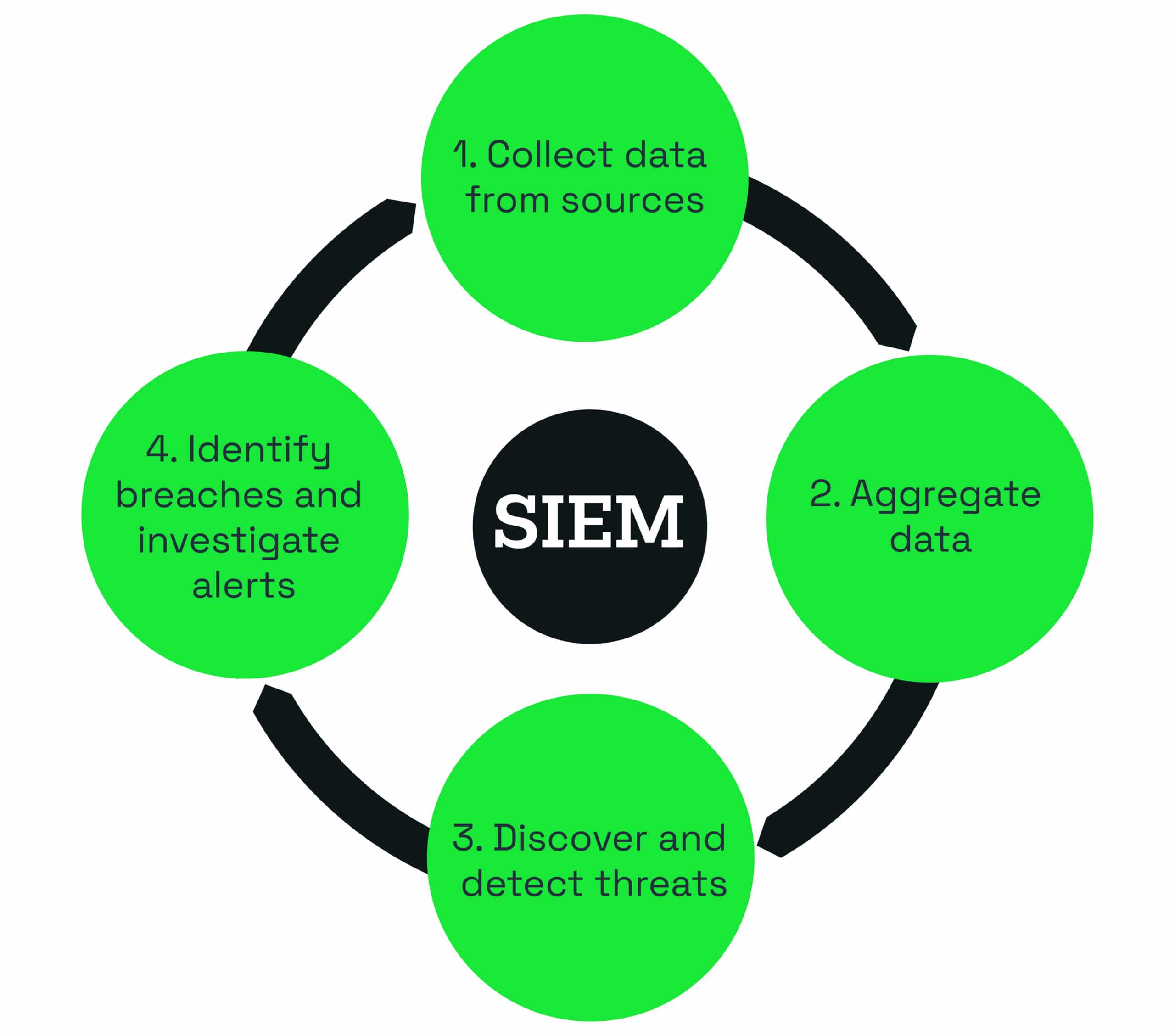
SIEM can be sold as software, as an appliance, or as a managed service. The products are also usually used to log security data and generate reports for compliance purposes.
Think about when you shop online and use your credit or debit card. Those companies you are spending your money with will need to have Payment Card Industry (PCI) compliance.
The standard is there to ensure there are controls around cardholder data to reduce the risk of credit card fraud and a SIEM helps them prove and meet compliance requirements.
What is a SOAR?
Security orchestration, automation and response, or SOAR, is very similar to SIEM.
It refers to the technologies that enable organisations to collect data inputs which are then monitored by the security operations team.
For example, alerts from the SIEM system and other security technologies would be subject to analysis and triage through a combination of human and machine power to define, prioritise, and drive response activities.
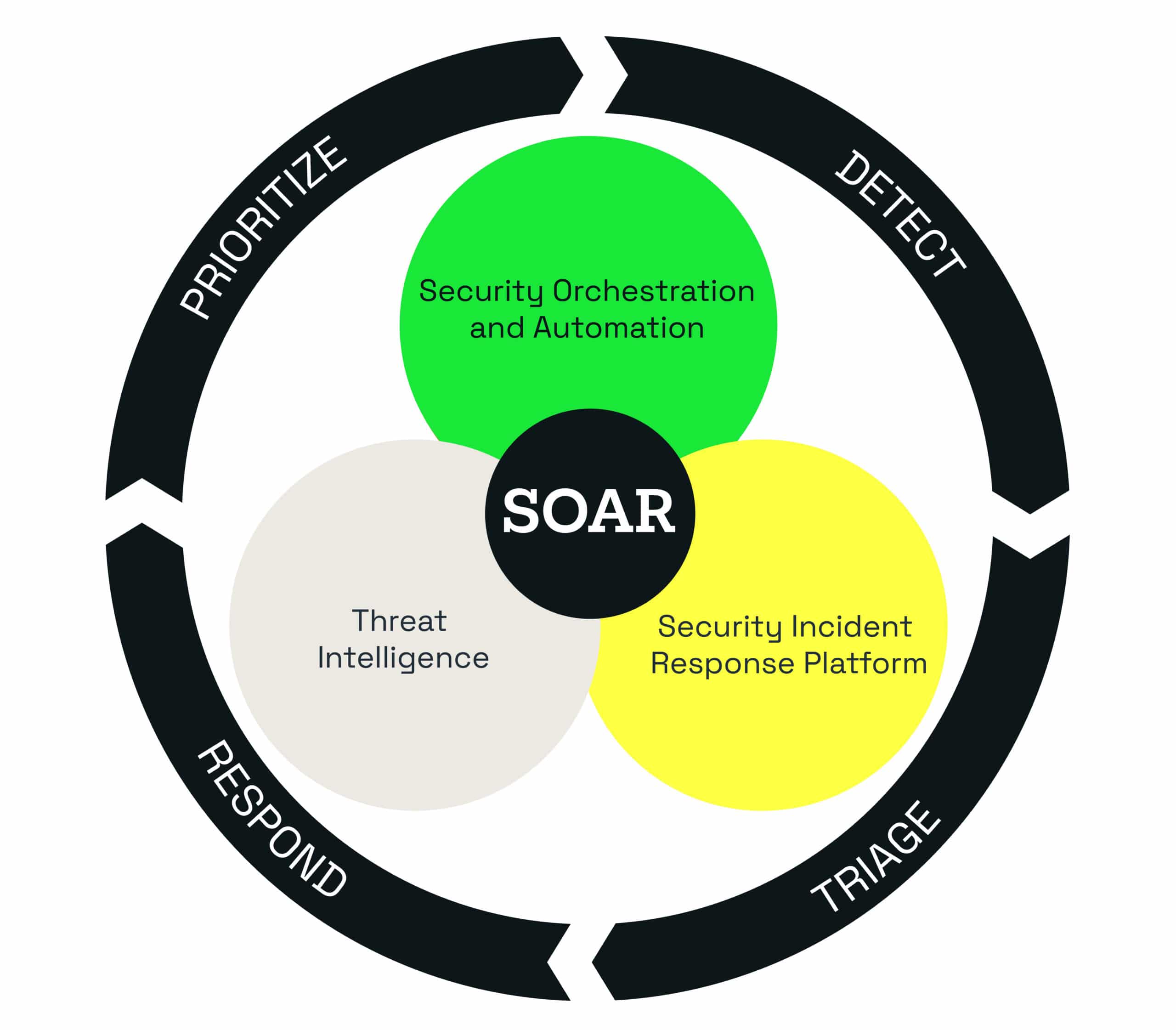
SOAR tools allow an organisation to define those analysis and response procedures in a digital workflow format to quickly respond, contain and remediate incidents with little to no human intervention.
You may be thinking that SIEM and SOAR sound the same, but while SIEM tools have been around for years, SOAR is the new kid on the block.
When looking at SIEM vs. SOAR, they are similar in that they both collect security data from a variety of sources.
Where they differ though, is in the locations and quantity of information being sourced. While SIEM will ingest various log and event data from traditional infrastructure component sources, a SOAR takes in all those things and much more.
How does a SOC work?
Before the age of cloud computing, organisations would rely on firewalls installed at the edge of their network and download malware scanning solutions to combat the threat to network security.
Today is a different story. The threat landscape has changed, and hackers have evolved. Their attacks are increasingly more sophisticated and profitable, spreading exponentially across the Internet.
The way that security is managed has evolved too with the advent of the SOC. It’s an example of software as a service (SaaS) that operates as a subscription service in the Cloud.
Through a SOC, networks and endpoints can be continuously monitored for vulnerabilities and threats. If an incident is discovered, the SOC can respond to remediate that incident and investigate the root cause.
Let’s quickly look at the different SOC models that are available.
Regardless of model, all SOCs have several core functions that need to be fulfilled operationally.
These functions are what provide the main security value for any organisation.
Log collection
All SOCs need data and the main source of that data are logs from a variety of sources. These data sources are usually Windows or Linux servers, firewalls, endpoints, databases, etc.
Ideally, data should be collected real-time. This means having direct feeds into the SIEM tool from any systems within the enterprise.
As analysts cannot review data on that scale, part of the SIEM is a log ingestion engine, which uses artificial intelligence algorithms to scan the logs and pick up anomalies.
These logs also need to be retained and available for investigation into older security incidents for regulatory and compliance purposes.
Monitoring
This is usually done using scanning tools or the scanning element of the SIEM.
The scans are run across the company’s network to look for potential threats, breaches, and suspicious activity.
This information can then be used for tuning and optimisation to better ignore false positives and improve the speed and accuracy of incident identification.
The better your SIEM can surface accurate and urgent alerts, the less your analysts will suffer from alert fatigue and the more effective your response power will be.
Incident response
If an incident does occur, then the SOC needs to respond and ensure that the threat is stopped and neutralised.
They will also need to ensure that any compromised systems are secured appropriately and cleaned before being returned to service.
If the incident involves a hacker then they need to follow the chain of evidence and secure property (such as logs) if any investigation or criminal case is to be brought.
Root cause analysis
Where an incident has occurred, the SOC will need to fully investigate the root cause of the problem and diagnose why it happened in the first place.
This analysis should then feed into a continuous improvement process to prevent any future occurrences of the same incident.
Vulnerability management
The SOC is also responsible for vulnerability management.
This means identifying areas of the network or infrastructure that might potentially be vulnerable to an attack and taking steps to prevent it from happening.
This could be anything from the patching of servers and application of policies on firewalls, to vulnerable port closures or software updates.
Why do I need a SOC?
A SOC is typically needed because most organisations handle data, and that data needs to be protected.
Data is at its most vulnerable while it is traversing an organisation’s network either internally or on the Internet. Company websites are a particular draw for hackers, as behind them sit vast databases of client data – name, address, date of birth, national insurance number – all things that can be used or sold for profit.
This can be anything from an unsuspecting member of staff clicking on a malicious link in an email, to a disgruntled employee purposely causing damage or compromise to an internal system.
In both cases, having a SOC will help identify those threats quicker and remediate any vulnerabilities before they become a major issue.
Improved threat management
Companies have traditionally deployed various security technologies to help detect and prevent threats, as well as to strengthen and protect their assets.
These security technologies need to be centralised, standardised, correlated and monitored in real-time.
There is also a need to have resources available to analyse and respond to suspicious activities and incidents.
Where a SOC provides benefit is by bringing all those elements together in a ‘single pane of glass’ view so that the review and remediation process is coordinated to reduce risk.
Maintenance of regulatory compliance
Regulatory compliance has become essential for many businesses, especially with more transactions taking place over the Internet.
A SOC helps you meet regulatory compliance requirements that call for security monitoring, vulnerability management or an incident response function.
Centralisation and consolidation of security functions
Bringing the elements responsible for security together as a SOC enables the consolidation of security functions within a business.
This can save money and enable cost-sharing. It can also help maximise expertise, skills and resource availability.
Challenges of running a SOC
Like any venture in business, there are challenges to running a SOC.
Budget and costs
Establishing a SOC can be a difficult challenge.
There are costs involved in the initial outlay and resourcing for the tool. Do you use existing staff with some security knowledge and provide training? Do you hire in a new member of staff who then needs to learn the business but can build the capability?
Do you develop it inhouse or outsource it entirely? Or, to account for limited resources, do you adopt a co-managed approach with an outsourced partner identifying and prioritising incidents and focus your internal resources on remediation?
There are several things to be considered, but whether you start small and build up or choose to outsource each approach has its own set of benefits and challenges.
Lack of processes
If you are building a SOC you need consistency in the work being done.
From monitoring to incident remediation, there should be processes in place to determine what that work looks like.
All too often the processes are forgotten about in the rush to implement the end solution, and it can cause difficulties further down the line when the processes become a requirement for legislation and compliance purposes.
Too focused on the technology
This is somewhat tied to budget and costs.
It is a scenario where all the focus is placed on buying the right tool, only to exhaust the funding for resourcing or training.
Staff are then left to self-learn and ultimately the tool is not used to its full potential.
Internal support for the SOC
If the business is not fully aware of why the SOC exists and what the benefit of it is then there will be a lack of support due to a lack of understanding of the function.
It’s important to communicate the implementation of the SOC and manage it like any other business project, ensuring all stakeholders buy into the concept and the need for a SOC from the outset and that they continue to support it beyond its inception.
Skills shortages
In March 2020, it was estimated by the UK government that approximately 653,000 businesses (48%) have a basic skills gap when it comes to cyber security.
The difficulty is compounded by the fact that more and more businesses need these skills to meet regulatory requirements and manage their cyber security.
Qualified and experienced analysts are in short supply but high demand.
Conclusion
I’m hoping by now that you have a much better idea of what exactly a SOC provides, how it operates and the challenges and benefits of implementing one.
What matters most is finding a balance of people, process and technology that works best for your size and requirements. Don’t run before you can walk, start small and give yourself room to grow and scale up accordingly.
A SOC doesn’t have to cost the Earth and might be more achievable than you think.
Key takeaways
A SOC should enable you to proactively respond to suspicious or malicious activity to identify, contain, remediate and recover from threats.
Whether inhouse or outsourced, it’s important to be clear about what you want to measure and report on.
A good balance of people, process and technology will provide a much better SOC experience – for you, your staff, and your organisation.
Choose your SIEM/SOAR tool wisely. Do your research, get a demo and proof of concept if you can.
There’s no one size fits all SOC – find the platform and approach that best meet your needs, be it inhouse, outsourced or a bit of both.


Free Guide
In-house vs. outsourced security operations: Which is right for you?
62% of organisations say their security teams are understaffed.
Download your 35-page comparison guide to discover:
- The real cost of building an in-house SOC
- Key questions you must ask before investing
- Hidden risks that could catch your business out

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.






