Important updates have been announced to UK (and US) cyber security regulations over the last few months. We explore what they are, what it means for your business, and how to prepare and safeguard your digital supply chain.
Cyber attacks continued to increase in volume and sophistication through 2022, and 2023 shows no sign of changes.
As a result, the governments of the UK and the US have tightened their cyber security regulations. Improving the cyber resilience of both the public and the private sectors.
These regulatory changes may have far-reaching consequences for your organisation’s ability to trade and stay competitive.
They should also ensure you take a robust approach to the security credentials of your chosen managed service provider.
By staying ahead of these changes, you can take the necessary steps to improve your security, compliance, and ensure resilience in your digital supply chain.

Security risks in the digital supply chain
Is your Managed Service Provider your security weak link?
The UK Government’s National Cyber Strategy 2022
Published on 15 December 2022, the National Cyber Strategy 2022 is a serious initiative from the UK government. Over £22 billion is going to be committed to its research and development.
It’s designed to strengthen resilience at national and organisational level to prepare for, respond to, and recover from cyber attacks.
Critical national infrastructure will be the first to be fully secured, with the private sector to follow close behind.
All of these changes are to be implemented by 2025.
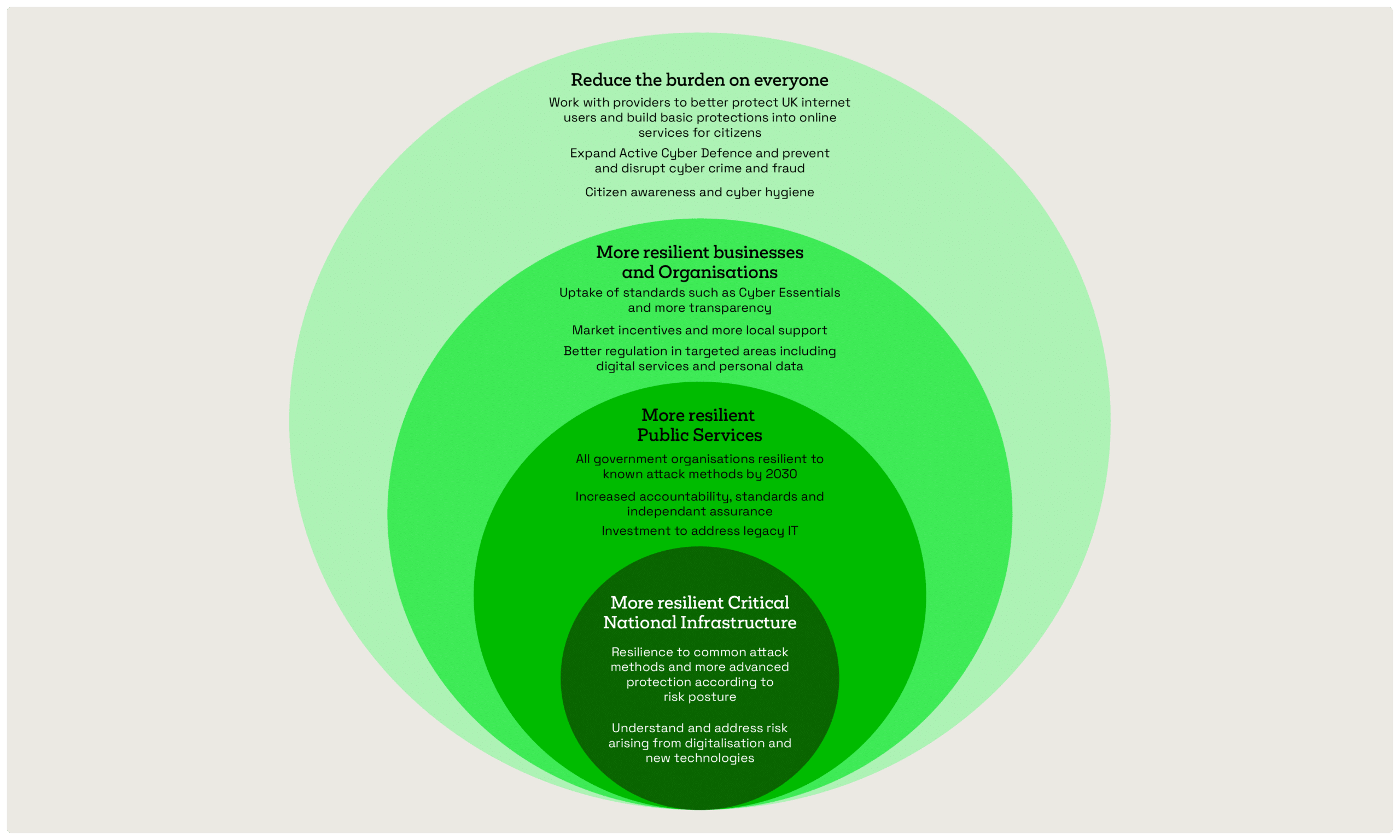
Notable changes coming soon include:
- The UK Government will adopt the National Cyber Security Centre’s (NCSC) Cyber Assessment Framework (CAF) across all departments and setup a new cross-department SOC known as the Government Cyber Coordination Centre (GCCC).
- The UK Government will review the critical national infrastructure sector to increase adoption of the CAF and review vulnerabilities in the sector’s supply chains.
- Market incentives will be developed to support and drive behavioural change amongst UK businesses to proactively manage their cyber risk.
- Targeted legislation to ensure cyber risk is managed effectively by those with the greatest responsibility to do so (i.e. large organisations or managed service providers)
Recent changes to Cyber Essentials
In January 2022, the NCSC introduced the biggest update to Cyber Essentials since its launch in 2014.
The changes require UK businesses to demonstrate far more robust cyber resilience in order to achieve the accreditation.
Initially, it allowed organisations a 12-month grace period to implement many of these changes.
That grace period is rapidly coming to an end. So you need to be ready.
Changes (at a glance)
- All cloud-based services are now required to be ‘in scope’ of Cyber Essentials.
- All admin users of cloud services must apply multi-factor authentication (MFA), tougher MFA and password rules needed for standard users.
- More stringent rules on device declaration and bring your own device (BYOD) policies.
- Tougher security rules around virtual, server-based computing (or thin clients), homeworkers, and firewalls.
Further updates and changes to Cyber Essentials are due in April 2023. These will build on the updates in 2022, offering clarifications, adjustments, and further guidance.
Some of the notable recent changes include:
- New guidance on zero trust architecture for achieving cyber essentials, and a note on the importance of asset management.
- Tighter controls around third-party devices.
NIS regulations extended to include managed service providers
The Department for Digital, Culture, Media and Sport (DCMS) announced in November 2022 that outsourced IT providers and managed service providers (MSPs) would be brought into the scope of the Network and Information Systems (NIS) Regulations.
Specific changes have not been formally announced, but the regulations are likely to include more stringent requirements for mandatory reporting on cyber incidents. Potentially, there will be tougher financial penalties for non-compliance.
The goal of this legislation is to strengthen the UK’s resilience against online cyber attacks. These third-party companies will now be accountable for protecting the sensitive data they manage on behalf of their clients.
The legislation would require outsourcers and managed service providers to implement robust cyber security measures, and to report any cyber incidents to their clients and the relevant authorities.
It’s a move designed to boost the UK’s cyber resilience against online attacks. With MSPs holding the keys to the kingdom of so many UK based businesses, it seems like the logical next step in bolstering the security of the digital supply chain.
Joe Biden’s 2021 Executive Order on cyber security
While it might be a little older, and US specific, Executive Order (EO) #14028 is worth mentioning as it hints towards changing trends we’re starting to see in the UK.
The EO is aimed at helping the US Government and private sector work together to better protect themselves against cyber threats.
Measures in the EO include the Federal Government switching to a zero trust “never trust, always verify” mindset.
Furthermore, organisations working with Federal Government need to have improved processes in place, covering:
- Modified contract language and processes to adhere to new guidance from NIST and the Cybersecurity and Infrastructure Agency (CISA).
- Businesses will be required to manage and secure their own software supply chains better.
- Service providers to Federal Government must now share incidents and threat information.
- Organisations must have MFA and encryption processes in place as standard.
These cyber security regulatory changes might not all have a direct impact on you right now, but it’s a clear indicator of which way the winds are blowing. And what you need to plan for with regards to security and compliance.
What these changing cyber security regulations mean for your business
The changes make it more important than ever for your business to improve its cyber resilience and security posture.
It’s clear that regulatory changes starting with central government and critical infrastructure will impact on the bottom line of many businesses. Especially with regards to winning contracts and providing commercial services.
Organisations serving this sector that can’t demonstrate Cyber Essentials accreditation or essential security capabilities, such as MFA or data encryption, will be impacted first.
These challenges will soon also ripple through the digital supply chain and into other industries.
The changes to Cyber Essentials place a lot more importance on securing remote working practices and new cloud infrastructures.
The 2022 changes have proven to be a big step up in complexity for many organisations. Our advice would be to seek help if you need it, as getting these accreditations will be crucial for your business in the future.
The expansion of NIS regulations to include MSPs means you should undertake a review of your current supplier, if you have one.
Check their incident reporting processes, and make sure you scrutinise their security processes closely.
It will become increasingly important to use a managed service provider with strong cyber security credentials as regulations tighten around resilience of digital supply chains.
Key takeaways
You should prioritise Cyber Essentials accreditation if you don’t already have it, especially if you deal with government bodies of critical infrastructure as part of the supply chain.
Make the shift to a zero trust security mindset. Use modern, risk-based, multi-factor authentication practices to control access to data and systems.
Review and refine your remote working and mobile device management policies to ensure you have strong security procedures in place.
Review the security of your cloud infrastructure. The benefits of the cloud are revolutionary to many organisations, but the Cloud can also massively expand your attack surface.
Your security is only as strong as your weakest link. Scrutinise your MSP to ensure that it isn’t the weak link in your digital supply chain.

Security risks in the digital supply chain
Is your Managed Service Provider (MSP) the weak link in your security? Discover:
- Must-ask security questions
- Must-have security credentials

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier






















Got a question? Need more information?
Our expert team is here to help.








