Discover how threat actor TA4557’s sophisticated phishing campaign is targeting recruiters through fake job applications. Uncover their advanced techniques and how security teams and staff can identify these malicious threats.
Since October 2023, TA4557, a known cyber threat actor, has been deploying a new phishing tactic targeting recruiters.
By disguising malicious emails as job applications, the group aims to lure unsuspecting professionals into malware infections.
It’s an approach that highlights how cyber criminals are always looking to exploit potential vulnerabilities in professional workflows.
Who is TA4557?
Active since 2018, TA4557 has been closely monitored across the cybersecurity community. This financially motivated actor is infamous for its advanced techniques and proprietary tools.
They’ve previously been observed distributing the well-publicised More_Eggs backdoor, a piece of malware capable of creating profiles of infected systems and delivering harmful payloads.
TA4557 is also linked to advanced threat groups such as Evilnum and Cobalt Group, sharing overlapping methods and tools. Their campaigns are targeted, persistent, and marked by clever evasion tactics, making them a formidable adversary in the cyber threat landscape.
How the attack works
TA4557’s attacks are carefully crafted to deceive and evade.
Here’s how they unfold:
1. Initial contact: TA4557 sends recruiters emails posing as job candidates. These emails look authentic and are designed to get a response from the recruiter.
2. Delivery of a malicious link: Any recruiter who replies to the initial email then receives a link to a website claiming to host the candidate’s CV.
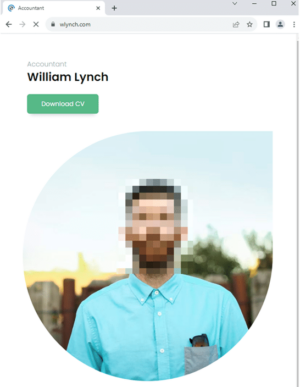
Source: Proofpoint
3. Malware deployment: The page contains a button or link prompting the recruiter to download the CV. Clicking downloads a .zip archive containing a malicious shortcut file (.LNK). Running the file triggers a “Living Off the Land” attack, leveraging legitimate Windows processes, such as ie4uinit.exe, to download and execute a scriptlet.
4. Persistence mechanisms: The scriptlet installs a DLL file in the %APPDATA%\Microsoft folder and uses Windows Management Instrumentation (WMI) to create a registry process that ensures the DLL’s execution.
5. Evasion tactics: The malware is designed to retrieve the RC4 encryption key needed to activate the More_Eggs backdoor, showcasing TA4557’s advanced operational stealth.
A textbook case of social engineering in action
The group’s success has been heavily influenced by their application of advanced social engineering tactics.
By engaging victims in legitimate conversations via non-malicious communication they establish trust and legitimacy. The perfect foil from which to deliver the malicious payloads and content.
It’s a tactic that can cause problems for many modern detection tools that focus on detecting immediate threats. This calculated approach makes their attacks particularly challenging to identify and stop.
Indicators of compromise
Proofpoint have provided indicators of compromise to be used in endpoint protection services.
- annetterawlings\.com
- Type: Domain
- 9d9b38dffe43b038ce41f0c48def56e92dba3a693e3b572dbd13d5fbc9abc1e4
- Type: SHA256
- 6ea619f5c33c6852d6ed11c52b52589b16ed222046d7f847ea09812c4d51916d
- Type: SHA256
- 010b72def59f45662150e08bb80227fe8df07681dcf1a8d6de8b068ee11e0076
- Type: SHA256
How to protect yourself and your organisation
Detecting attacks like these can be hard, especially in the early ‘benign’ stages.
And as the threat actors specifically target recruiters, the communications can often avoid being pinged as suspicious.
Of course, having a Security Operations Centre (SOC) with the most up to date and sophisticated detection technology can help spot behaviour patterns or anomalies beyond simple content scanning.
Moreover, this is a risk that again highlights the critical importance of creating a security-first and risk-aware culture across organisations.
Which is why Kocho strongly advocates ongoing training and assessments that continually drum in the importance of remaining vigilant. Upskilling everyone’s ability to spot potential phishing or other social engineering tactics.
Talk to our team to find out about how we can help with phishing and security awareness programmes for your organisation. And download our free guide to modern phishing trends below.
Key takeaways
TA4557 targets recruiters with fake job applications.
Attacks use malicious CV links to deploy malware.
Social engineering builds trust before delivering payloads.
Malware evades detection using legitimate Windows processes.
Early-stage attacks appear harmless, bypassing tools.
Training and advanced SOC tech are key defences.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great protection starts here
Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
You’ll get:
- Notifications of critical vulnerabilities
- Recommendations to reduce your risk level
- Expert advice to defend against new threats
























Got a question? Need more information?
Our expert team is here to help.








