Cloud identity transformation just got a major boost. Learn how Microsoft Entra’s newly released Source of Authority (SOA) conversion feature helps enterprise teams untangle hybrid identity. Helping you move towards a scalable, cloud-native future, without ripping out what still works.
Your identity journey probably started like most, with Active Directory (AD) running the show on-prem, with users and groups neatly tucked into your domain controllers.
Simpler times? Maybe.
But then came the shift to the cloud, and suddenly identity was being managed in two places. The result? A world of compromise.
You could create users and groups in Entra ID, but the moment they needed to interact with AD, things got messy. Group Provision to AD helped, but creating new groups on-prem still left you tangled in years of sprawl.
That’s all about to change.
With the introduction of Microsoft’s isCloudManaged attribute, supported by updates to Entra Connect and Cloud Sync, you can convert existing AD groups and users to be managed directly in Entra ID. No breakages. No rebuilds.
It’s a major step forward. One that clears the path to cloud-native identity, without ripping out what’s already working.
Charting the journey to cloud-native identity
Every journey needs a map.
Microsoft defines five distinct identity models, from fully on-prem to fully cloud-native.
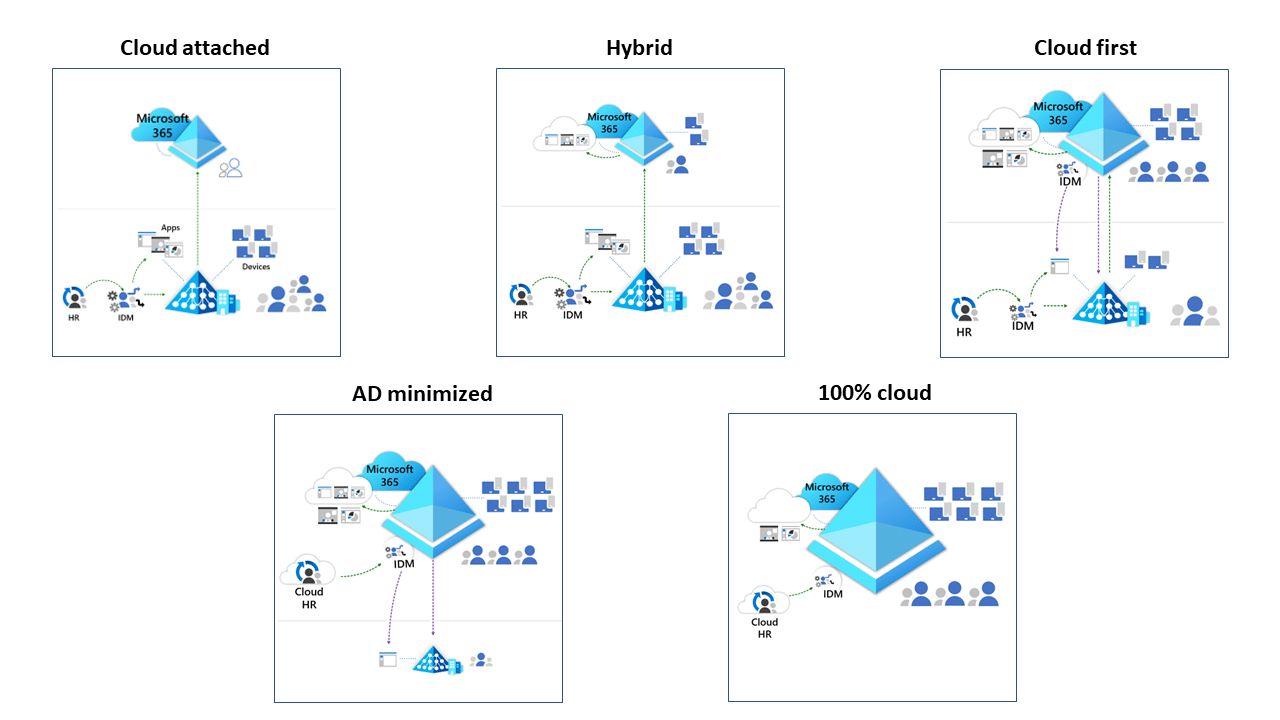
We know that most organisations haven’t reached the destination yet. They’ll be somewhere in the middle, navigating the hybrid-to-cloud-first phase.
That means users are still provisioned into AD, with groups spanning both on-prem and cloud environments, with Entra Connect or Cloud Sync doing the heavy lifting.
Some are already writing groups from Entra ID back into AD, but even then, AD often retains a huge footprint. Group sprawl persists. User authority still starts in the data centre.
This is where things start to change.


latest edition
Everything you need to know about Microsoft Entra
A clear, practical view of how Microsoft Entra works as a unified platform.
Expert guidance on modern identity design, security, governance, and Entra licensing.
Discover how you can:
- Run Entra as one coherent identity platform
- Apply end-to-end security and governance
- Modernise IAM safely, from MIM to AI-driven identity
Managing the source of authority (SOA)
Now, the SOA is key to all of this.
It determines whether a user or group is managed on-prem or in the cloud. Until now, Entra Connect could provision and match objects from AD into Entra ID. But once they landed in the cloud, they were effectively locked in. Changing the SOA to Entra ID meant deleting and recreating the object, which in turn meant losing key identifiers.
Not anymore.
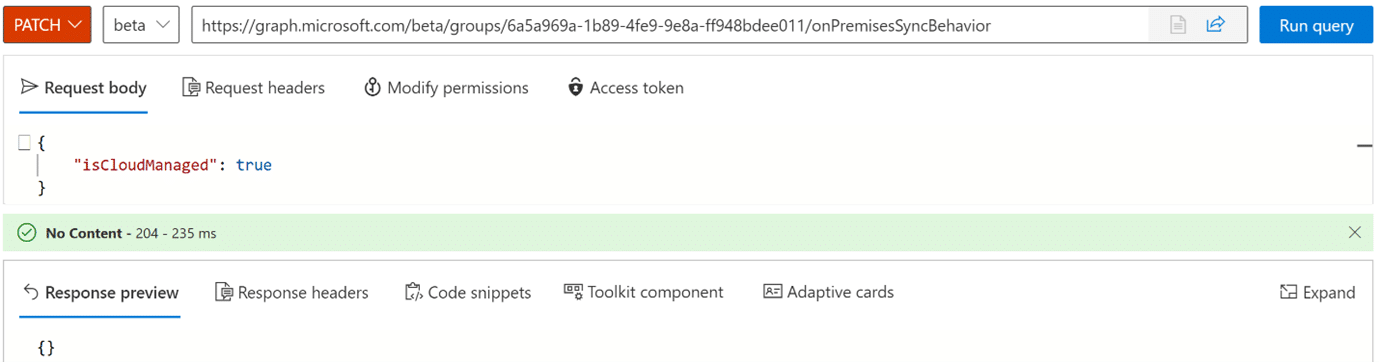
The breakthrough comes with the new isCloudManaged attribute. When you’re running the latest version of Entra Connect (minimum usable version 2.5.76.0) or Entra Cloud Sync (minimum usable version 1.1.1370.0), these tools recognise this attribute and know to stop syncing that object from on-premises.
Note: Only universal group types are currently supported. You’ll need to adjust the scope of other groups before making the switch.
Once dependencies are cleared, the process is simple. A single PATCH call via Graph API updates the object’s state quickly and without disruption.
This is a big win for those looking to untether their estates from legacy, getting you to a cloud-first model without rebuilding from scratch. No broken links. No identity loss. Just clean handover, ready for what comes next.
But be mindful. If your estate still relies on AD-integrated services, not everything will be ready to move in one go.
Group attribute
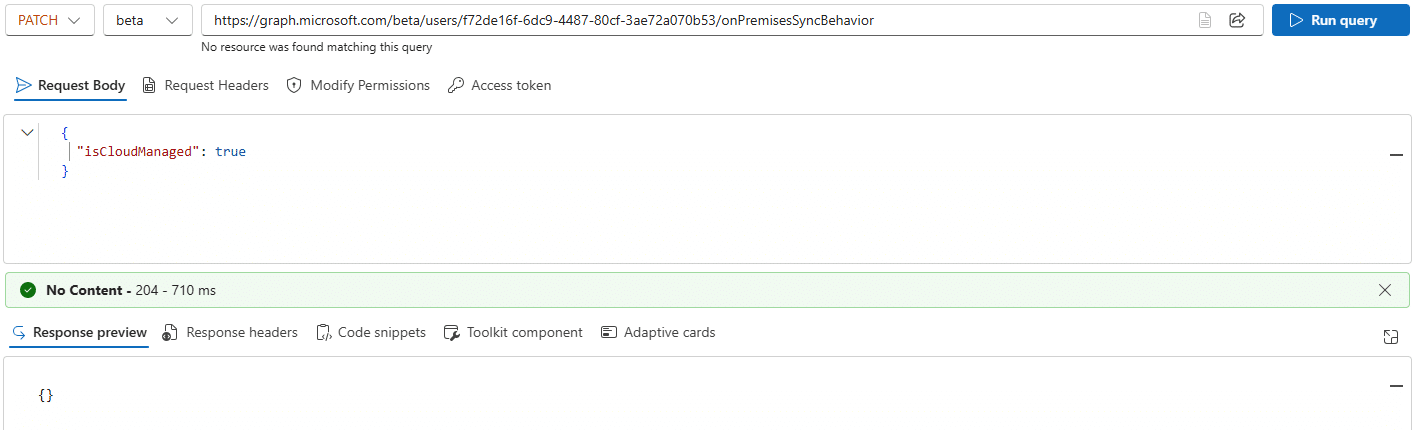
User attribute
The ‘what if’ scenarios for managing groups in the cloud
So, how do we start untangling years of static memberships, nested groups, and legacy sprawl without triggering chaos. This section we’ll dig into some common scenarios and explore what’s now possible, what’s still constrained, and how organisations can begin shifting group authority without disruption.
What if your on-prem groups are managed by MIM or GroupID?
For many organisations, group membership in AD isn’t handled manually. It’s automated using tools like MIM or GroupID, driven by attributes like department, location, or job role.
If you’re looking to bring those groups under cloud management in Entra ID and maintain dynamic behaviour, there are a few critical steps.
Once a group becomes cloud-managed, it defaults to static.
To preserve automation:
- Convert the group to dynamic, which removes any synced membership.
- Rebuild the membership logic using Entra’s rule syntax.
- Automate the transition using Graph API to apply changes at scale.
But there’s nuance here. If the group is already being used for authorisation in Entra ID or connected services, any misstep could impact access. The logic must be sound, the timing right, and the transition carefully managed.
It’s not overly complex, but it does call for expertise. Done right, this is your opportunity to simplify operations and maybe even retire on-prem logic for good.
Managing mail-enabled security groups and distribution lists in Entra ID
If all your mailboxes are already in Exchange Online, you can change the group’s source of authority and manage it via Exchange Online or Exchange PowerShell.
Just be aware:
- These groups cannot be written back to on-prem AD.
- Entra ID, including Entitlement Management, does not support managing mail-enabled security groups or distribution lists.
So, while you can manage them in the cloud, it still needs to be done through Exchange tools.
Navigating nested groups without breaking things
SOA only applies to the specific group object you set it on. It doesn’t cascade through nested groups. If a group contains other groups, those nested groups will stay managed on-prem unless you update each one individually.
This is by design, so you’ll need to:
- Apply SOA to each group you want to convert
- Start at the lowest level of the hierarchy and work upward
That way, you keep control and avoid unexpected behaviour as you transition.
Matching Entra ID groups to on-prem AD groups
Previously, Group Provision to AD would always create a new group. Microsoft Entra Cloud Sync can now match existing AD groups when provisioning from Entra ID.
Here’s how it works:
- Cloud Sync looks for an existing AD group originally provisioned from Entra ID and has SOA applied.
- It uses the SID value to identify a match.
- If a matching group is found within the writeback scope, the cloud group is linked to the original AD group.
- If no match is found, a new on-premises group is created.
This approach helps maintain continuity between cloud and on-prem identities without creating duplicates.
Bringing users into the SOA journey
As of 3rd October 2025, Microsoft Entra now also supports user SOA conversion, giving you the ability to change a user’s source of authority without writing back.
Enabled scenarios include:
- AD minimisation – switch a user’s SOA when they no longer need AD-tied access (e.g. LDAP, file shares).
- Cloud-first apps – when connected applications already use SAML/OIDC claims from Entra.
There are a few caveats to be aware of:
- You’ll need the latest versions of Entra Connect Sync (>2.5.76.0) or Cloud Sync (>1.1.1370), which recognise the new isCloudManaged user flag.
- Password Hash Sync must be enabled.
- There is no AD provisioning functionality yet.
- Automatically provisioning from other sources such as HR must be carefully scoped for affected users.
This brings user management into the same modernisation path as groups, helping you reduce reliance on AD, simplify your hybrid estate, and move closer to cloud-native identity.
Do you actually need that on-premises object?
Not every on-premises application needs an AD user or group.
It depends whether they use AD for authentication or they’re web apps integrated with Entra ID SAML 2.0 or OIDC. These apps can directly recognise groups and claims in Entra ID, so you don’t need an on-premises representation at all.
This is also a great opportunity to start cleaning up your on-premises groups.
Making group clean-up part of your cloud shift
Over time, AD environments fill up with groups that no one owns, uses, or remembers. Many are still synced to Entra ID, bringing complexity, risk, and unnecessary overhead.
Microsoft has published guidance to help clean this up. It focuses on security and distribution groups in single-forest, single-domain environments, and excludes groups that contain non-user objects like computers or contacts.
Here’s how to approach it:
Removing groups you no longer need helps reduce risk, eases admin effort, and simplifies what gets synced into Entra ID. It also puts you in a better position to move toward a modern, cloud-first identity environment.
How to start managing groups and access in Entra ID moving forward
Now is a great time to start formulating how your groups and access will be structured in Entra ID. It’s worth setting some standards in a written policy.
1. Start with purpose: Classify group types by use case
It’s worth remembering that Access Package Auto-Assignment Policies can be used alongside standard policies in the same package meaning that, unlike dynamic groups, exceptions can be managed for the same resource set.
Wherever a dynamic security group or assignable security group is used, it can be written back to AD using Group Provision to AD.
Use cases
-
Recommended type:
Dynamic Group
Reason:
Automatically maintained, low admin overhead
-
Recommended type:
Dynamic Distribution Group
Reason:
Automatically maintained, low admin overhead
-
Recommended type:
Microsoft 365 Group
Reason:
Enables full M365 collaboration suite including mail distribution
-
Recommended type:
Assigned Security Group
Reason:
Manual control, ideal for sensitive roles or exceptions.
-
Recommended type:
Distribution Group
Reason:
Manual control, ideal for sensitive roles or exceptions.
2. Decision tree: When to use what
You next need to unpick what solution works for the different tasks at hand.
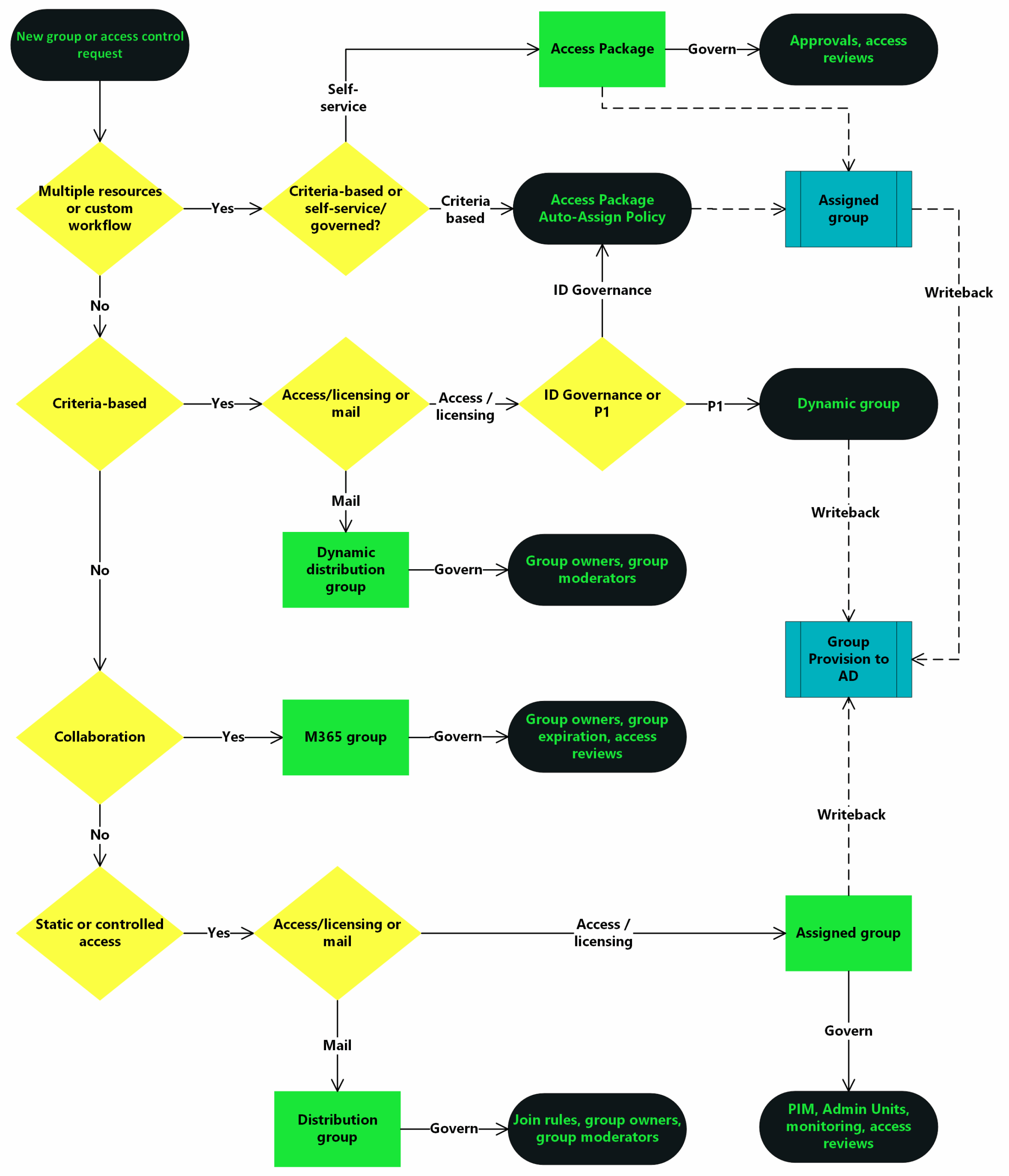
3. Naming conventions: Prevent sprawl and duplication
Use a structured naming convention that encodes purpose, scope, and ownership.
Format:
[Prefix]-[Region/Scope]-[Department/Function]-[Purpose] -[Suffix]
Examples:
- SG-EU-HR-Payroll → Security Group for HR Payroll in EU
- DG-Global-IT-Admins → Dynamic Group for IT Admins globally
- M365-US-Marketing-Campaigns → Microsoft 365 Group for US Marketing Campaigns
- AP-UK-Finance-Contractors → Access Package for UK Finance Contractors
Prefix Legend:
- SG = Security Group (Assigned)
- DG = Dynamic Group
- M365 = Microsoft 365 Group
- AP = Security Group used in Access Package
4. Governance principles
Before rolling out your group policies, it’s vital to establish the right governance guardrails. These principles will help you maintain order, prevent sprawl, and keep access aligned with business need.
5. Management Recommendations
To keep your environment clean, secure, and scalable, you need the right management habits in place.
We suggest:
- Use access reviews and expiration policies for Access Packages
- Document rule logic for Dynamic Groups and review it on a quarterly basis
- Assign owners and moderators to Dynamic Distribution Groups to ensure accountability
- Require owners for Microsoft 365 Groups and enable expiration policies to avoid sprawl
- Set up access reviews for Assigned Security Groups and reduce manual changes by using Admin Units or privileged roles
- Assign clear ownership to Distribution Groups and configure join rules where self-service access is appropriate
Caveats and gotchas
Before you dive in, there are a few limitations and quirks worth knowing. Ignore them and things can quickly unravel.
- Minimum supported version of Entra Connect Sync Client is 2.5.76.0
- Minimum supported version of Entra Cloud Sync client is 1.1.1370.0
- Cloud Sync can’t provision users to AD
- M365 Groups can’t be written back to AD
- Global groups are unsupported , only Universal groups work
- Mail-enabled groups and DLs can’t be written back
- SOA doesn’t cascade through nested groups
- Cloud-managed groups don’t support extension attributes 1–15
- Exchange Hybrid must be disabled before switching user SOA
- Federated domains aren’t supported , switch to PHS or PTA
The next steps to modernised identity
Modernising identity doesn’t mean starting from scratch. With Microsoft Entra’s latest update, it’s now possible to shift group and user management into the cloud without breaking dependencies or losing fidelity.
Legacy tools like MIM and GroupID will still need careful planning to phase out, but it’s achievable. The first step is clean-up. Streamlining your group structure now will save you serious pain later.
The real win is what Entra brings in return. Automation, governance, and lifecycle controls that go well beyond what AD was ever built to handle. But to take full advantage, you need clear rules. Ownership, naming, access policies, and lifecycle strategy all need to be in place before scaling up.
This guide isn’t the finish line. It’s your playbook for moving forward. Start small, think big, and build an identity model that fits the way your business actually works.
Entra and cloud identity: Common questions
-
Not yet. Only universal security groups are supported for SOA conversion at present. Global and domain-local groups need to be converted before switching.
-
Latest versions of Entra Connect or Cloud Sync, Graph API access, and PowerShell (for bulk operations).
-
No, you simply apply the isCloudManaged attribute and Entra Connect will stop syncing that object.
-
Not fully. You can manage them in Exchange Online, but they can’t be synced back to AD or managed via Entra’s native UI.
-
Use Microsoft’s recommended scream test methodology, check ownership and usage, and remove groups only once you’ve validated they’re unused or redundant.
-
Moving to cloud-native identity isn’t without its complexities. A Microsoft-focused identity partner can help make the journey smoother, particularly when it comes to navigating tricky provisioning scenarios or avoiding disruption to existing services. With the right support, organisations can move faster, avoid common pitfalls, and stay focused on long-term outcomes.
Great identity starts with great partnerships
The Kocho team has been delivering secure identity management solutions for our clients for more than 20 years. Which is why we know that every organisation is on its own path to modernisation, with no two environments ever alike.
If you’d like to explore what’s possible within your organisation and see how you can take the next steps away from legacy solutions, then please get in touch with our team.
And if you need to understand more about what Microsoft Entra can really offer, then please download our exclusive, expert-authored guide via the link below.


latest edition
Everything you need to know about Microsoft Entra
A clear, practical view of how Microsoft Entra works as a unified platform.
Expert guidance on modern identity design, security, governance, and Entra licensing.
Discover how you can:
- Run Entra as one coherent identity platform
- Apply end-to-end security and governance
- Modernise IAM safely, from MIM to AI-driven identity
Next steps
Like this? Don’t forget to share.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.







