Privileged access no longer sits in silos. Microsoft’s ecosystem now connects identity, elevation, credentials, and monitoring into one joined-up model. Here we show how this simplifies operations and gives security teams far greater control.
The line between Privileged Identity Management (PIM) and Privileged Access Management (PAM) has always been hazy. And while legacy tools like MIM offered some capabilities, the common perception has long been that Microsoft’s identity management really only really covered the PIM side.
But it simply isn’t true anymore.
In reality, Microsoft Entra and Azure already deliver the privileged access controls most organisations are buying elsewhere, and they do it across cloud and on-prem without adding yet another platform to manage.
And, if you’re running Entra Suite or the ID Governance SKU, then you already have the foundations in place. You don’t need a separate third-party tool to get what Microsoft now provides natively. The extra spend is modest, the operating model barely shifts, and you end up with a cleaner, more controlled environment.
You just need to know how to unlock it.
What if PIM and PAM became Privileged User Management (PUM)?
PIM focuses on identities and what they can do: who holds privileged roles, how those roles are governed, and when access is reviewed. It applies to human and machine accounts alike.
PAM, on the other hand, focuses on what those identities actually do – controlling elevation, managing credentials, authenticating users, and monitoring activity.
But in modern hybrid environments, that split makes less sense. Cloud workloads, in-app admin roles, and cross-platform teams mean organisations are really managing the privileged user, not separate identities or systems.
So, maybe a more accurate (if not official -yet!) term, might be Privileged User Management (PUM). This perhaps reflects how organisations increasingly operate, treating the privileged user as the core unit for control, governance, and automation, spanning:
- Lifecycle of the privileged identity
- Assigned roles and environments
- Just-in-time elevation paths
- Credential management across cloud and on-premises systems
- Continuous evaluation and risk monitoring
- Guided user experience for privileged tasks
Microsoft’s Entra ecosystem already supports this model. PIM and PAM capabilities converge through access packages, Logic Apps, Hybrid Worker, AVD, Private Access, and Conditional Access. PUM reflects the real work of admins and provides a future-ready framework for governance and automation.
The difference between PIM, PAM (and now PUM)
PIM governs privileged identities.
PAM governs privileged access and actions.
BUT: Modern environments require managing the privileged user across both of these (PUM).
Managing privileged identities in Microsoft Entra
Entra PIM offers just-in-time (JIT) access to Azure and Entra roles. It works well, but two questions arise:
- How are privileged identities created and disabled?
- How do JIT and lifecycle controls extend to on-premises systems?
Privileged accounts should use dedicated secondary identities. Even with automated HR-to-AD/Entra flows for standard users, manual steps for privileged accounts create gaps. Dormant accounts and overlooked leavers are persistent risks.
Entra, combined with ID Governance, provides a solution. Logic Apps can extend Access Package assignments or Lifecycle Workflow triggers to generate SCIM payloads, driving API-based provisioning in Active Directory. This handles accounts even if they are on-premises and unsynced to Entra.
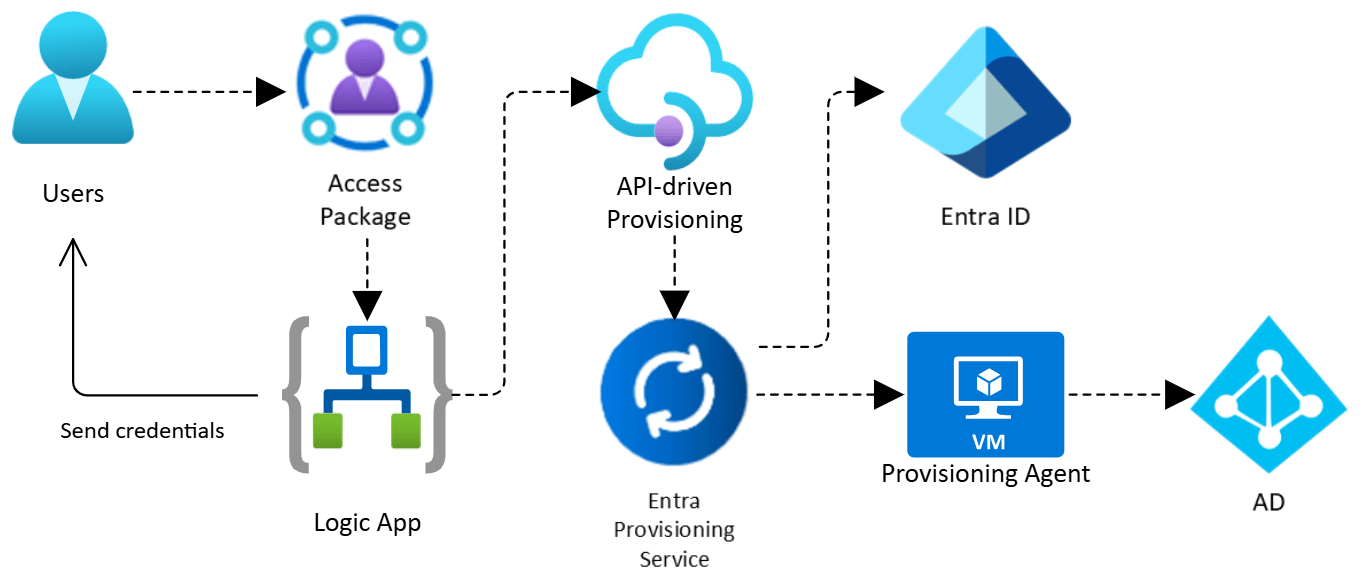
For cloud-only accounts, Temporary Access Pass (TAP) lets users register a passkey without ever needing a password.
For on-premises accounts, Hybrid Worker supports lifecycle tasks through Runbooks in Azure Automation. It creates accounts, adds users to groups, or removes access when no longer required.
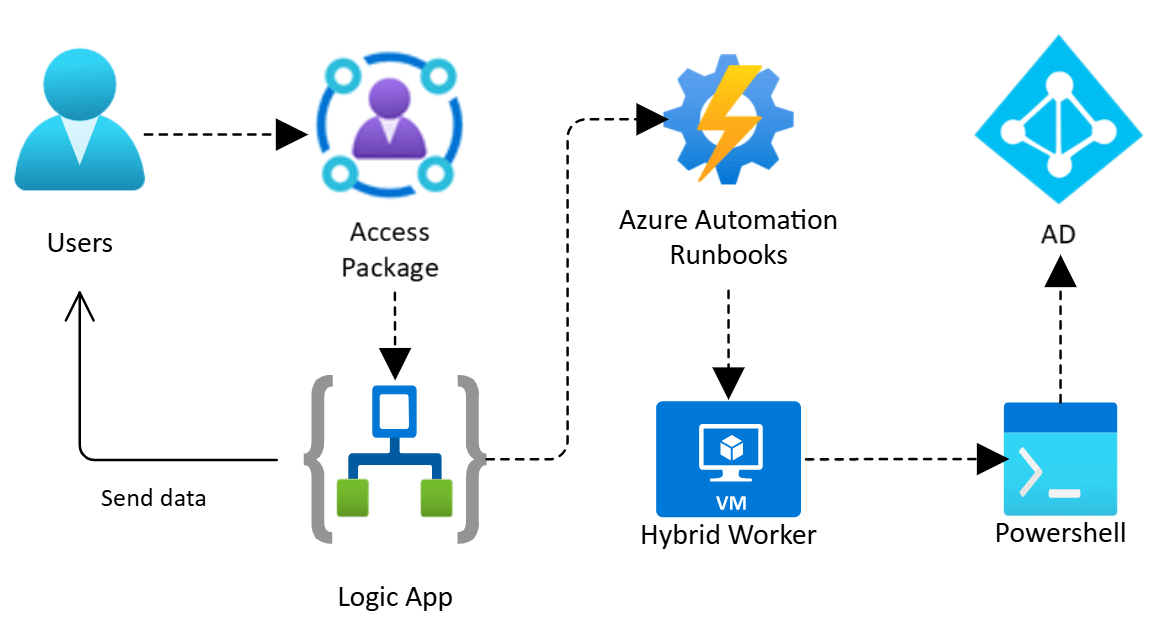
Managing privileged access across cloud and on-premises
With identities managed, the next focus is access. Credential rotation, session controls, and network segmentation all need a coordinated approach.
Hybrid Worker can manage AD password resets at creation, on demand, or on schedule. Azure Key Vault ensures secure credential storage. Entra Application Proxy and Private Access provide controlled access to internal applications, legacy protocols, and SSH environments. Conditional Access policies enforce strong authentication.
Azure Virtual Desktop (AVD) can serve as a Privileged Access Workstation (PAW). Combined with Conditional Access and Private Access, this creates a controlled and monitored environment for sensitive tasks.
While Microsoft does not yet offer advanced session capture like keystroke or video monitoring, full auditability is possible using Azure Monitor Agent and Defender. Activities can be logged, exported to Log Analytics or SIEM, and continuously evaluated via Entra Continuous Access Evaluation (CAE). Suspicious activity triggers near-immediate session termination.


latest edition
Everything you need to know about Microsoft Entra
A clear, practical view of how Microsoft Entra works as a unified platform.
Expert guidance on modern identity design, security, governance, and Entra licensing.
Discover how you can:
- Run Entra as one coherent identity platform
- Apply end-to-end security and governance
- Modernise IAM safely, from MIM to AI-driven identity
Using bots, Teams agents and automation to streamline privileged access
Logic Apps can deliver Temporary Access Passes, passwords, or notifications through encrypted email. Teams integration offers a more modern experience. Privileged users can interact with a bot or agent to request elevation, reset passwords, or check account status. Natural-language queries can trigger automated workflows in seconds, reducing friction and increasing security.
Agents can also guide users through role elevation, password expiry, or other privileged tasks, embedding operational controls directly into user workflows.
Using Access Packages to manage privileged access journeys
We’ve touched on a range of Microsoft components that can stand alone, but they deliver far more value when used together in the same ecosystem.
Entitlement Management – the My Access portal – is fast becoming the central entry point, even for admins, with privileged roles now sitting alongside everyday access tasks. Keeping privileged user journeys here creates a cleaner, more consistent experience.
Elevation can be triggered by the primary account, secondary accounts stay passwordless, and the PIM portal can be kept for true edge cases such as Global Admin, protected with context based access.
By starting privileged journeys here, we can start to deliver a consistent experience:
- The My Access Portal becomes the central place for admin and user access.
- Privileged journeys can start here, with elevation triggered by the primary account.
- Secondary accounts stay passwordless, with PIM kept only for edge cases or Global Admin.
- Access Packages provide built-in Access Reviews and support features like Verified ID Face Check.
- B2B guests, including vendors or partners, can request privileged accounts the same way.
- Custom questions and selections can also be added where variables are at play.
An end-to-end privileged user scenario in Microsoft Entra
Consider Pedro, a new starter who needs a privileged account:
Step 1
Pedro requests a secondary account in My Access. Manager approval triggers a Logic App to provision the AD account, and Access Packages apply automatically.
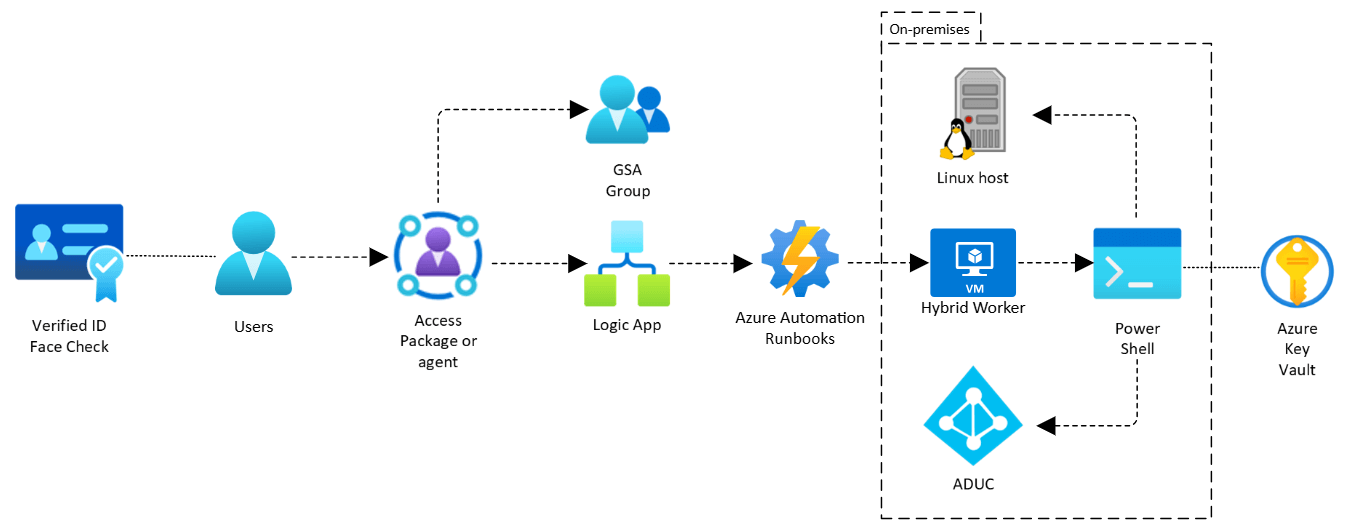
Step 2
He selects the “User Admin” package: giving two hours access in Account Operators, ladmin (or a bespoke user) added to the Linux sudo group, and SSH access to an Entra group via Private Access. His AD password is reset and delivered via Teams.
Step 3
Pedro signs in with a passkey using his cloud account, accesses his AVD PAW host to connect to Linux via Putty through a tunnel via Global Secure Access and can RDP to an on-premises server for connecting to Active Directory. CAE monitors continuously.
Step 4
After two hours, the package unassigns. The deprovision Logic App and Hybrid Worker remove his Private Access membership, Account Operators role, and Linux root access. The Teams agent notifies him.
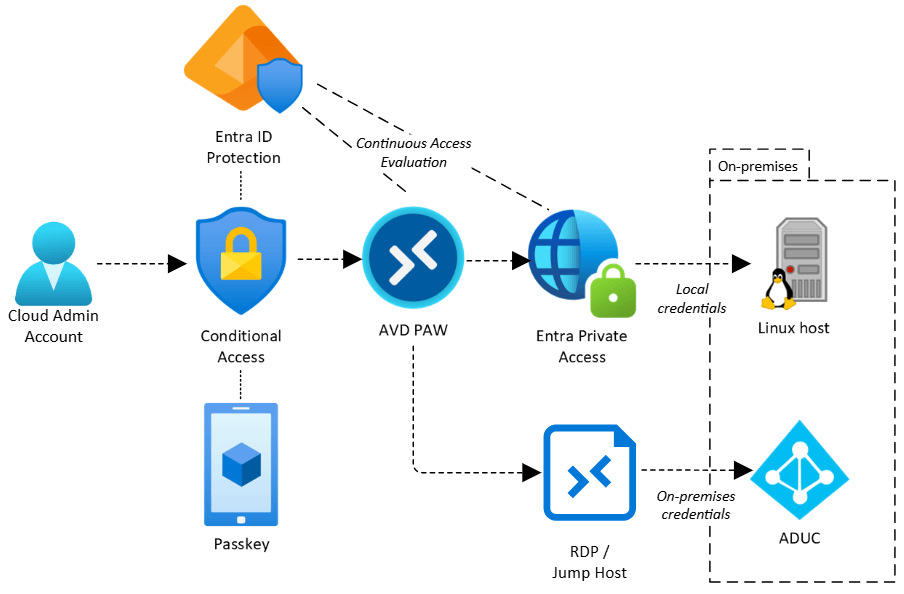
Step 5
Higher privilege requests, like Domain Admin, require Face Check verification in My Access.
Step 6
Six months go by (how time flies!), and his manager is required to complete an Access Review to approve Pedro’s continued access.
Step 7
A year later, Pedro decides to move onto a new job and leaves the business. Lifecycle Workflow removes all Access Packages and disables his privileged accounts.
What this scenario shows
Bringing it all together
Hopefully this has shown what’s possible when you manage privileged users with Microsoft.
Entra, PIM, Hybrid Worker, Logic Apps, Private Access, and AVD can collectively support identity lifecycle, just-in-time access, credential handling, and monitoring across cloud and on-premises.
The real value comes from treating the privileged user as the centre of control and designing workflows that fit how teams actually operate. Automations then become cleaner, security becomes easier to enforce, and the whole journey feels more manageable.
Session monitoring may not match every dedicated PAM tool, but strong auditing and control are achievable by combining Microsoft’s native security and monitoring features, plus the integration options you gain through Teams and agents.
It’s a modern approach that reduces admin effort, lowers risk, and lets organisations get more from the technology they already own.
FAQ: Microsoft PAM and Privileged User Management
-
Yes. Microsoft delivers PAM capabilities through Entra, PIM, Conditional Access, Access Packages, Logic Apps, Hybrid Worker, AVD, Private Access, and Azure Automation. Together, these support identity lifecycle, just-in-time elevation, credential handling, and privileged access to cloud and on-premises systems.
-
PIM manages privileged identities. PAM manages what those identities can access and do. Modern environments require both models to work together, which is why this approach increasingly focuses on managing the privileged user as a whole rather than treating identity and access as separate tracks.
-
PUM is a practical way to think about privileged access. It treats the privileged user as the centre of governance, covering how accounts are created, how elevation happens, how credentials are handled across hybrid estates, and how activity is monitored. Microsoft’s Entra ecosystem already supports this approach.
-
Yes. Hybrid Worker and Azure Automation can provision, update, and remove on-premises privileged accounts. Private Access and Entra groups handle SSH access and legacy protocol routing. AVD can act as a secure workstation for privileged tasks, with Conditional Access enforcing strong authentication.
-
Yes. Entra PIM provides JIT access for cloud roles, and Access Packages extend JIT flows to on-premises environments through Logic Apps and Hybrid Worker. Session risk is continuously monitored through Conditional Access and Continuous Access Evaluation.
-
Hybrid Worker can reset AD passwords automatically, at creation, on schedule, or on demand. Temporary Access Pass enables secure registration without passwords for cloud-only accounts. Azure Key Vault provides secure storage for sensitive credentials used in automated workflows.
-
Microsoft does not provide traditional session capture such as keystrokes or video. It does offer comprehensive auditing and telemetry through Azure Monitor Agent, Defender, and Log Analytics. Entra Continuous Access Evaluation can terminate sessions almost instantly when suspicious activity occurs.
-
Yes. Access Packages support B2B users. Vendors or support partners can request internal privileged accounts through the same My Access workflow, with the same governance controls and Access Reviews. This also includes guests using AVD and GSA with the new public preview for external identities.
-
Access Packages and Lifecycle Workflows can trigger Logic Apps to automate creation, disablement, and removal. API-driven provisioning supports on-premises AD accounts, and workflows ensure privileged accounts are removed as soon as a user changes roles or leaves the organisation.
-
For many organisations, yes. Microsoft already covers core PAM functions across lifecycle, elevation, credential management, access control, and monitoring. Some organisations still complement Microsoft with third-party tools for deep session recording, but the majority of requirements can now be met using Entra and Azure-native capabilities.
-
Agents allow privileged users to request elevation, reset passwords, and receive notifications through natural language through Teams. This removes friction, reduces errors, and embeds privileged access directly into everyday workflows.
-
- Unified governance across cloud and on-premises
- Automated lifecycle and elevation workflows
- Strong authentication and conditional access
- Lower operational overheads
- Integration with existing Microsoft investments
- A simpler, more guided user experience

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.









