Significant changes have been taking place over the last two decades as an increasing number of organisations turn to the cloud, with many businesses now running on a hybrid cloud state.
This cloud footprint grew organically, initially gaining traction within organisations with Software as a Service (SaaS) solutions, with adoption subsequently growing around the likes of Infrastructure as a Service (IaaS) and Platform as a Service (PaaS).
The COVID-19 pandemic has accelerated the pace of change in recent times. The rapid adoption of video conferencing tools like and Microsoft Teams is testament to this, with the rate of which they were adopted transforming work practices.
The use of this technology also shifted the conversation around the adoption of the cloud services that underpin such tools. The benefits of these became a hot topic, with discussion focused around the ability to scale cloud services quickly and easily.
This push towards the cloud can most clearly be seen in Office 365, with Microsoft shifting the market towards taking the approach of consuming Office 365 as a service. Microsoft is also one of the most widely adopted cloud platforms, with the majority of companies somewhere along their journey to a complete Office 365 installation. Projects are now being delivered globally that are underpinned by various cloud services.
As organisations start to switch over to a cloud-first approach, understanding the foundations of these services, and how to keep them secure is crucial to create solid building blocks. Conversation around the adoption of cloud services should focus on the control of encryption keys and data.
The challenge of data sovereignty
As the move to the cloud progresses, an increasing number of organisations are seeking help with data sovereignty.
Some organisations, such as those within the legal sector, are seeking to gain understanding due to pressure placed on them by clients who may have privacy concerns or are mandating key management.
Organisations also have their own concerns in trusting the handling of sensitive data to cloud providers. In the event of a subpoena, this goes directly to the cloud service provider rather than the organisation, meaning that the organisation has no direct control over whether to give up access to the data.
Data sovereignty is a very real issue that is troubling organisations currently. The Capital One breach was instigated by a rogue admin who gained access to server data, subsequently leaking over 100 million customer records.
Who is responsible for data has become a conversation topic over the last few years.
When it comes to moving data off-premise and into the cloud, who is responsible for it?
When data sits on-premise, an organisation is responsible for the hardware and software to access this. However, as soon as data is moved across to the cloud, the question of responsibility becomes blurred. Ultimately, it is the cloud service provider’s responsibility to ensure that the organisation can access their data. However, the protection and security of this data still lie with the organisation.
For organisations, having the opportunity to be the key custodian whilst also owning the sovereignty of their data allows them to have complete control over who access this data and how.

Sign up for great content and exclusive invites
Join the Kocho mailing list for latest news, best practice, and educational resources.
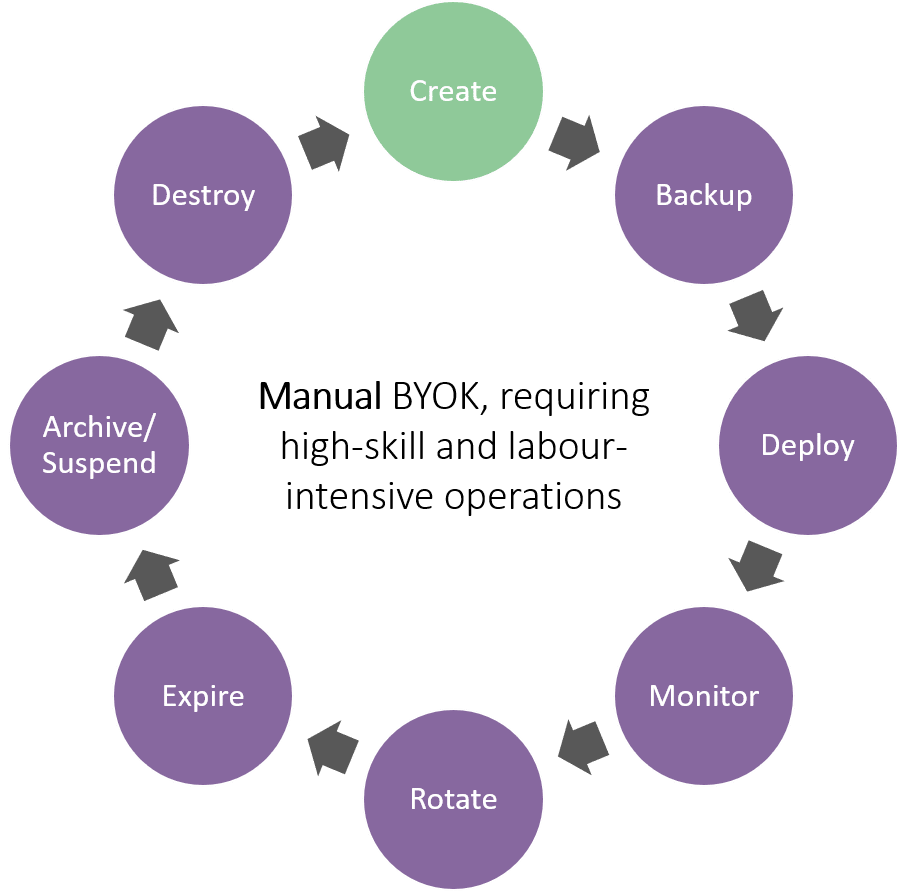
Securing Data in the Cloud
When moving data to the cloud, there are several options surrounding data security:
- Data stored in the cloud in clear, no keys, no encryption: Only recommended for personal, meaningless data which requires no protection.
- Data stored in a single cloud, CSP provides encryption, keys and access controls: Allows cloud service provider to provide the encryption of the data. Organisations have no control over encryption keys – they are just using the cloud facility.
- CSP provides keys and users each use the different access controls for each CSP: Multi-cloud providers ensure that organisations are not locked into a single cloud service provider. However, the use of multiple cloud service providers means that each service requires different ways to manage data and access it, whilst organisations must still give control of the encryption keys to the cloud service provider.
- Data stored in single cloud, HSM derived key (BYOK), use access controls provided by CSP: A Bring Your Own Key (BYOK) model means that the organisation owns the key, whether that is a hardware security module or a key source. This key may sit on-premise or in the cloud, but importantly, the organisation owns and derives the key, as well as pushing the key into the cloud. This gives organisations ownership of the key material and how that key is being used to encrypt and protect data. This works well for a simplistic single cloud provider approach, however, organisations in this situation must learn how to use this and the back-end services of that cloud service provider.
- Data stored in multiple clouds, HSM derived keys (BYOK), users each use the different access controls for each CSP: With most companies looking at multiple cloud use, they can take the approach outlined in #4. This presents a demand for organisations to learn how to control and access each individual cloud service provider, which can become an extremely large task.
- Data stored in the multiple clouds, CCKM provides keys (optionally from HSM) key discovery and management and multi CSP access controls via CCKM single UI: This gives organisations absolute control over their encryption keys, while making multi-cloud use easier, with a Cloud Key Life Cycle Management acting as key broker.
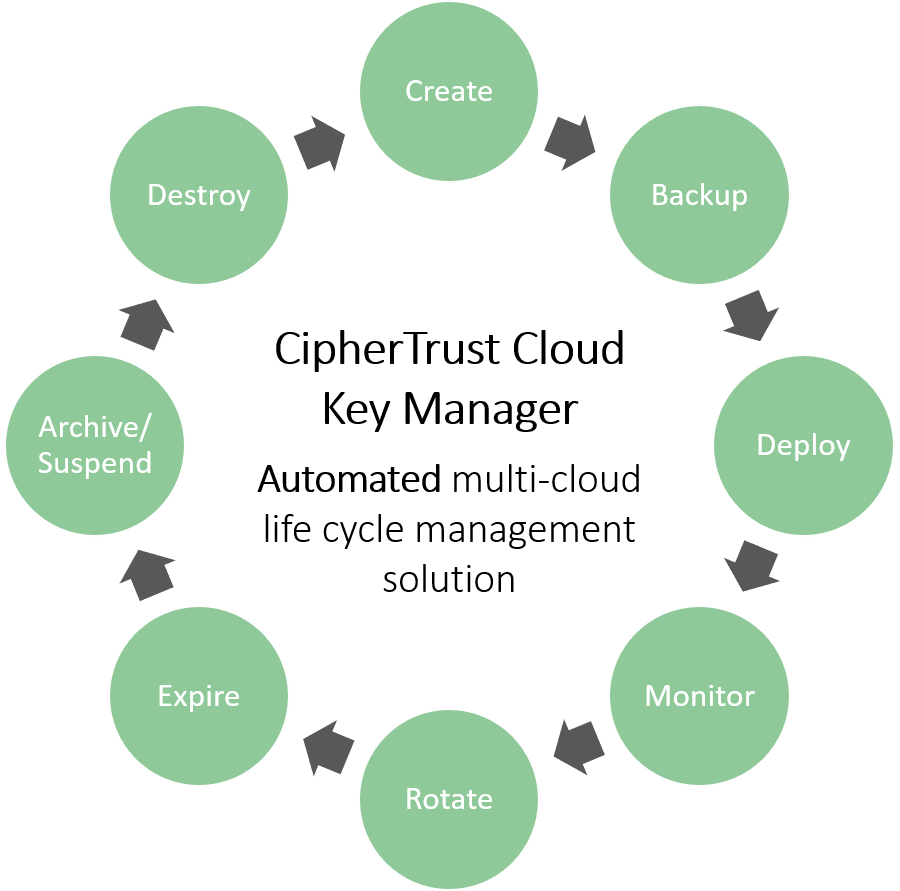
Introducing the CipherTrust Cloud Key Manager platform
Enabling organisations to migrate information to the cloud, whilst being assured that they have complete control over this data and its management is essential. CipherTrust Cloud Key Manager from Thales reduces the labour intensive side of key management and eliminates the need to have a highly-skilled corporate employee to manage this.
The CipherTrust Cloud Key Manager platform allows the centralisation of key management, enabling organisations to protect their data, wherever it resides. This eliminates the necessity of individually managing and understanding each cloud service provider.
The benefits of using the CipherTrust Cloud Key Manager include:
CipherTrust Cloud Key Manager supports a growing list of IaaS, PaaS and SaaS providers. SaaS solutions include Microsoft Office365, Salesforce.com and Salesforce Sandbox. Supported IaaS/PaaS solutions include Microsoft Azure, Microsoft Azure China National Cloud, Microsoft Azure Stack, IBM Cloud, Google Cloud Platform, and Amazon Web Services.
Using CipherTrust Cloud Key Manager provides the ability for organisations to be the key custodian, offer the lifetime key management of any keys that they are actually placing in the cloud.
Like this? Don’t forget to share.

Sign up for great content and exclusive invites
Subscribe to the Kocho mailing list if you want to receive:
- The latest Microsoft tech insights
- Demos and exclusive event invites

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier
























Got a question? Need more information?
Our expert team is here to help.








