Discover the threats our security operations team have been monitoring this month, and their advice to keep you safe.
This month:
- Babuk ransomware slips past SentinelOne protections
- Russian hacktivists strike UK council websites
- DragonForce attacks hit UK retailers hard
- VoLTE vulnerability puts O2 customers on the map
- Stealthy Chrome extensions steal credentials and control
Novel EDR bypass exposes SentinelOne-protected systems to Babuk ransomware
A new attack strategy, termed Bring Your Own Installer, is being used to bypass protections in SentinelOne’s Endpoint Detection and Response (EDR) solution.
The technique takes advantage of misconfigured installations, manipulating the upgrade and downgrade process to disable anti-tamper safeguards.
The attack began when threat actors exploited a known CVE in a publicly accessible server, gaining local admin access. From there, they deployed Babuk ransomware by crafting multiple legitimate SentinelOne installer versions and manipulating product version changes.
These actions left behind numerous event logs and forensic indicators of tampering.
What’s the risk?
- Bypasses core endpoint protections, allowing malware to run unchecked
- Enables full deployment of ransomware such as Babuk
- Forensic traces may be missed in environments without deep monitoring
- Misconfiguration leaves organisations unknowingly exposed
Recommended mitigation
Action point
Review your SentinelOne configuration. If not already active, enable Online Upgrade Authorisation – now a default for new installs – to ensure protection against this exploit.
Pro-Russian DDoS attacks target UK councils
On 8 May, the pro-Russian hacker group NoName057(16) launched a campaign of distributed denial-of-service (DDoS) attacks on UK government-affiliated websites.
Their targets included multiple local councils and the Association for Police and Crime Commissioners.
Portsmouth, Salford, Bury, and Trafford councils reported brief disruptions, while others reported no impact. The group cited political motivations, blaming the UK’s role in the Ukraine conflict.
What’s the risk?
- Disruption of public-facing digital services
- Reduced public trust in government IT resilience
- Exposure of inadequately defended infrastructure
- Increased likelihood of future, more sophisticated attacks
Recommended mitigation
Action point
Audit your organisation’s DDoS readiness. Ensure protections are in place and test your response plan to reduce recovery time.
Ransomware chaos at major UK retailers
A wave of coordinated ransomware attacks in late April and early May disrupted operations at major high street retailers including M&S, Co-op, and Harrods.
The attackers gained access through identity compromise and social engineering, exfiltrating sensitive files (such as NTDS.dit files containing domain user password hashes), and deploying DragonForce ransomware across IT estates.
The result was a significant breakdown in operational continuity: internal systems were taken offline, online order platforms became unavailable, and stock availability in physical stores was heavily affected. Customers and staff alike experienced visible service disruption, while organisations were forced into full-scale incident response mode.
What’s the risk?
- Total loss of access to core systems and services
- Large-scale data compromise
- Operational paralysis across customer-facing channels
- Financial loss from ransom demands and business disruption
Recommended mitigation
Action point
Run a full Active Directory hygiene check. Reassess your backup, recovery, and incident response strategies to reflect the growing threat of human-led ransomware campaigns.
Watch 3-minute Security Posture Assessment Demo
See for yourself how a Security Posture Assessment helps you:
- Improve visibility of security threats
- Prioritise threats based on risk and effort
- Track improvements and measure ROI
- Stop wasting money with smarter investments
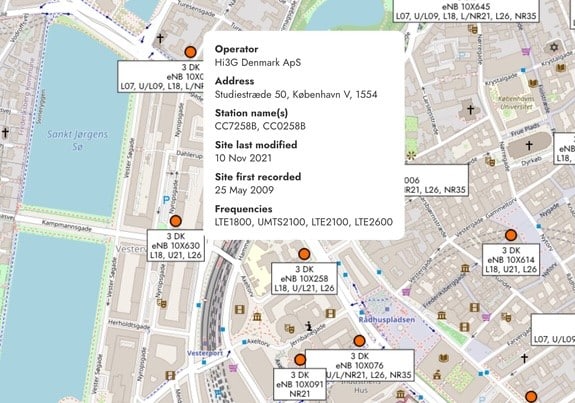
O2 VoLTE flaw exposes user locations
A vulnerability in O2’s Voice over LTE (VoLTE) implementation exposed sensitive metadata to any caller.
This included the recipient’s IMSI, IMEI, cell tower ID, and location area code, making it possible to determine their real-time location either domestically or abroad.
Security researcher Daniel Williams demonstrated this by successfully tracking a user in Copenhagen. The issue affected only O2’s network and has since been resolved.
What’s the risk?
- Real-time user location tracking by malicious actors
- Potential targeting of high-risk individuals or organisations
- Increased privacy concerns for roaming users
- Exploitation of mobile infrastructure flaws for surveillance
Recommended mitigation
Action point
Request a configuration audit from your mobile or VoIP provider. If you operate custom SIP infrastructure, review exposure of metadata in SIP headers immediately.
100+ fake Chrome extensions uncovered
More than 100 malicious Chrome extensions were discovered in May posing as helpful tools, such as VPNs and AI assistants, but were in fact part of a large-scale phishing and credential theft campaign.
Available via the Chrome Web Store, these extensions harvested sensitive data, injected ads, and in some cases enabled remote access.
The incident exposed how easily threat actors can weaponise trusted platforms to reach unsuspecting users.
What’s the risk?
- Credential theft and account compromise
- Unauthorised system access via browser hijacking
- Sensitive data exfiltration (e.g. banking or corporate access)
- Long-term malware persistence on endpoints
Recommended mitigation
Action point
Implement a company-wide browser extension policy. Block unverified extensions and limit installation rights to reduce exposure.


From our blog
Session cookie theft: The hidden risk to cloud identity security
The recent session cookie hijacking method, aka Cookie-Bite, offers yet another reminder that malicious actors are always on the hunt for ways to bypass even robust security controls like multifactor authentication (MFA).
For enterprises heavily invested in Microsoft 365 and Entra ID, it’s a wake-up call to take a fresh look at session security, endpoint hygiene, and browser-based risks in identity-first environments.
Resources & References
New Attack Method Bypasses SentinelOne’s Endpoint Detection & Response (EDR) Tool
Bring Your Own Installer: Bypassing SentinelOne Through Agent Version Change Interruption
‘Bring Your Own Installer’ Attack Targets SentinelOne EDR
Pro-Russian hackers claim to have targeted several UK websites | Cybercrime | The Guardian
Portsmouth City Council among UK authorities hit by cyber attack – BBC News
Pro-Russian hacking group targets council websites with DDoS attack – Tech Digest
Chaos spreads at Co-op and M&S following DragonForce attacks | Computer Weekly
Tech Insight : How Marks & Spencer Was Brought To A Standstill | Really Good Computer Support
Cyber news – 02 calls expose location
IS Preview 02 UK fixes Volte flaw
Hacker news – Fake Chrome extensions found
Thanks to this month’s contributors from the Kocho SOC team: Jack Fisher, Joshua Powell, and Nicci Smart.
Stay safe. Stay informed.

Let's talk!
Real partnership. Microsoft expertise. Complete transparency.
Book a free Discovery Call and learn more about our AI-powered security operations service, XDR Rapid Protect.
Get more information on:
- AI-powered rapid protection, from day one
- Dedicated Microsoft experts, by your side
- Powerful, intuitive reporting tools
- Collaboration and transparency as standard

Don't Miss
Great security & compliance resources






















Got a question? Need more information?
Our expert team is here to help.






