In July 2024, cyber security firm CrowdStrike suffered an outage that impacted upon organisations around the world. In this tech update, we’ll examine how opportunists tried to take advantage of the situation through phishing attacks.
Plenty has already been said about the global CrowdStrike outage in July 2024. The immediate impact on organisations around the world or the aftermath and eye-watering cost implications that are still being calculated.
However, one aspect of the outage that needs to be highlighted is the way that cyber criminals tried to take advantage of the situation for their own gain. And how this is a clear example of the opportunism that organisation’s need to always be on guard against.
The outage: A recap
CrowdStrike, a top cyber security firm known for its Falcon platform, provides endpoint protection through antivirus, EDR, and threat intelligence.
Now it’s important to note that the recent outage, which affected users of the CrowdStrike Falcon Sensor, was a system failure, not an external breach or cyber attack.
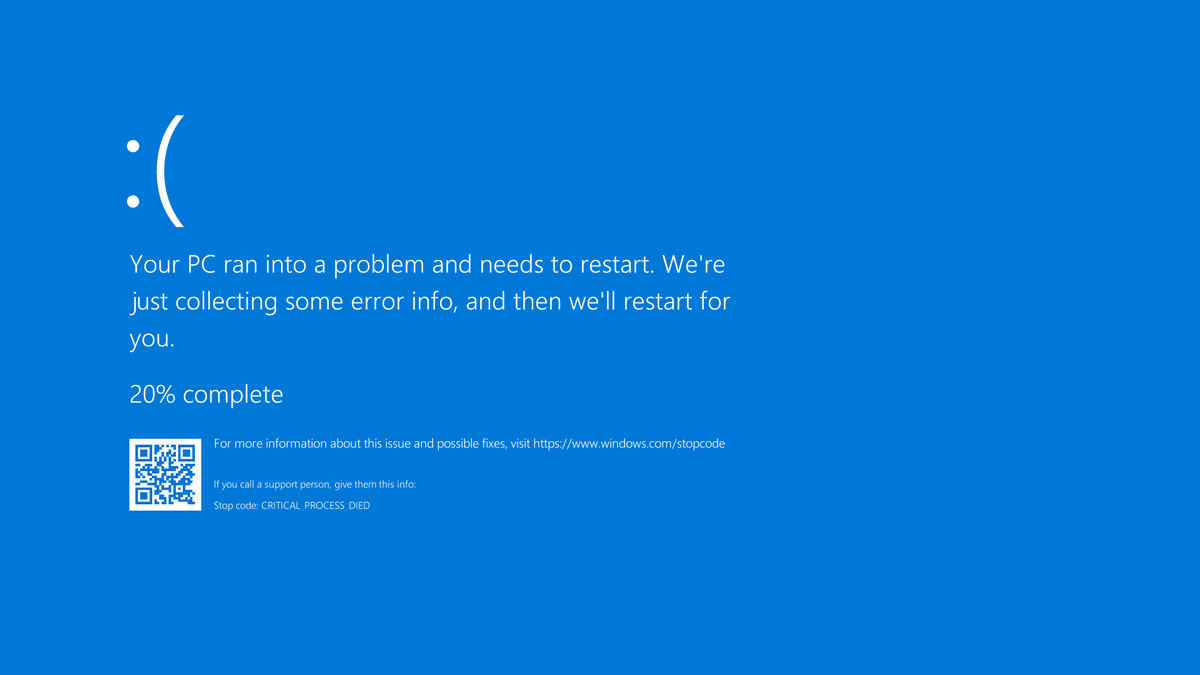
The Falcon Sensor update caused Windows to experience a BSOD (blue screen of death), rendering machines inoperable. Mac and Linux systems were unaffected.


Free Report
Phishing and Cyber Behaviour Trends
Who’s clicking on what? Why? And are your employees reporting threats?
Download Hoxhunt’s Phishing report and find out:
- Phishing threats that pose the highest risk
- Average time to identify and contain a breach
- Highly targeted and highly susceptible industries
Opportunistic phishing attacks
Whenever a significant outage occurs, cyber criminals see an opportunity to exploit the situation.
The CrowdStrike incident was no exception.
Opportunistic hackers quickly set up false CrowdStrike domains, masquerading as legitimate sources claiming to have a fix for the outage.
How these phishing attacks worked
- Fake domains: Hackers created convincing fake websites that appeared to be affiliated with CrowdStrike.
- Claims of a fix: These sites falsely claimed to offer a solution to the outage, enticing worried users looking for a quick fix.
- Monetary exploitation: Visitors to these sites were often asked to make a payment to access the fix.
- Malware installation: Instead of providing a solution, these sites would typically install malware on the victim’s system, further compromising their security.
Malicious domains
CrowdStrike released a list of identified impersonation domains.
Here’s a few examples of impersonated domains:
- crowdstrike0day[.]com
- crowdstrikebluescreen[.]com
- crowdstrike-bsod[.]com
- crowdstrikeupdate[.]com
- crowdstrikebsod[.]com
- crowdstrike0day[.]com
These domains can be added as indicators in security tools for monitoring and automatic blocking.
The intelligence can also be used for threat hunting and continuous monitoring.
Basic KQL to aid hunting and detecting
Threat Hunting (IoC based)
EmailUrlInfo| where TimeGenerated > ago(30d)
| where UrlDomain in (Malicious_Domains)
Continuous Monitoring
| where TimeGenerated > ago(1h)
| where EmailDirection == “Inbound”
| where LatestDeliveryAction == “Delivered”
| where SenderFromDomain has “crowdstrike”
and SenderFromDomain !endswith “crowdstrike.com”
| project TimeGenerated, SenderFromAddress, Subject, RecipientEmailAddress, DeliveryAction
The above KQL is a great start for IoC hunting and continuous monitoring.
The Microsoft XDR table named DeviceNetworkEvents and searching for malicious domains in the RemoteUrl column could also help to identify visits to malicious domains from endpoints.
Conclusion
While the CrowdStrike outage itself may have been a system failure, it created a collateral threat from opportunistic phishing attacks that preyed on the fears and anxieties of affected users.
An incident that perfectly highlights just how quickly these financially motivated predators react when they sense an opportunity.
And a stark reminder of how organisations need constant vigilance. Not just against direct cyber attacks, but also against those who seek to exploit vulnerabilities like those seen in the aftermath of this outage.
Which is exactly why we advocate proactive threat hunting and continuous monitoring to keep one step ahead of these opportunistic threats.
Key takeaways
The CrowdStrike outage was caused by a system failure, not a cyber attack. But it still led to significant security risks.
Cyber criminals quickly exploited the CrowdStrike outage by setting up fake domains and phishing sites.
Phishing attacks targeted users with fake solutions, leading to potential malware infections and financial loss.
Organisations need to continuously monitor and update security measures to detect and block malicious domains.
The incident highlights the importance of staying vigilant against opportunistic attacks during any crisis.
Want to know more?
If you’d like to understand more about how Kocho SecOps provides continual monitoring, proactive threat hunting, and rapid response to emerging incidents, reach out to our team for a detailed consultation.
And please join our mailing list for the latest cyber security news, technology updates, and regular tips to keep protected against advanced threats.

Let's talk!
30-day free trials and flexible contracts
Book a free Discovery Call and learn more about our AI-powered security operations service, XDR Rapid Protect.
Get more information on:
- 30-day free trials for new partnerships
- Flexible, 30-day contracts (no lock-in)
- Microsoft-funded proof of concepts
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great protection starts here
Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
You’ll get:
- Notifications of critical vulnerabilities
- Recommendations to reduce your risk level
- Expert advice to defend against new threats
























Got a question? Need more information?
Our expert team is here to help.








