From security operations to the boardroom, clear reporting underpins confident leadership on cyber risk. Learn how to achieve visibility that turns data into insight and evidence into action.
Cyber security now sits alongside finance and compliance as a measure of corporate governance. It’s how organisations demonstrate resilience, accountability, and control.
That makes reporting central to effective governance. It’s the link between security operations, strategic decisions, and demonstrable resilience.
Because without clear, evidence-based insight, even the strongest defences can’t show progress, justify investment, or guide confident action.
Yet many organisations still struggle to turn data into clarity. A daily flood of alerts, logs, and metrics often obscures more than it reveals.
When analysts and boards can’t see the wood from the trees, smart decisions stall.
And accountability suffers.

The goal is to turn data into information, and information into insight.
Context is king: Turning data into meaningful analysis
Security operations centres (SOCs) face a relentless flow of data. Every day, thousands of alerts stream in from Security Information and Event Management (SIEM) systems, threat feeds, and endpoint tools.
The noise makes it difficult to separate signal from distraction.
Raw metrics show activity, not meaning.
A report claiming 500 blocked phishing attempts sounds reassuring until you ask what it really means. How severe were those attacks? How have they changed over time? What was the impact on operations?
Clarity comes from context. When teams can answer those questions, they stop reacting to numbers and start responding to risk.


Free Guide
Turn risk stress into cyber confidence
The SME Guide to Modern Security Operations is a playbook to strengthen cybersecurity without headcount, hassle, or hidden costs.
Inside: SME security stats, ROI proof points, cost comparisons, critical benchmarks, and a roadmap to resilience and cyber confidence.
Different stories for different audiences
Of course, effective reporting requires understanding your audience.
Technical teams need operational detail: real-time alerts, comprehensive logs, threat indicators. These reports enable swift response and demonstrate security posture at ground level.
But executives need something entirely different. Talk to a CFO about zero-day exploits and you’ll get a polite nod. Frame the same threat in terms of customer data exposure or regulatory penalties, and suddenly you have their full attention.
Metrics alone will not earn board confidence.
Leaders need assurance that controls are effective, risks are reducing, and investments are delivering measurable returns.

More than half of UK cyber-risk professionals (52%) say their organisation struggles to translate technical security data into business risk.
Yet many organisations still fall short.
Decision-makers are expected to take responsibility for risks they cannot see, with little meaningful oversight of how digital systems are managed. It’s a disconnect that leaves both sides exposed and one that only clear, contextual reporting can resolve.
Data is only as valuable as the insight it delivers
Reports and dashboards are easy to produce. What sets effective reporting apart is how clearly it communicates risk, progress, and accountability.
With data flowing from every direction, clarity depends on context. The right reporting cuts through noise, turning metrics into insight that drives faster response, smarter decisions, and measurable value.
Quality reporting tells a story:
- What’s happening
- Why it matters
- What to do next
The best examples share common traits:
When reporting achieves this, it stops looking backward and starts driving strategy.
Clarity replaces complexity.
The question shifts from “how many alerts?” to “how much safer are we?”
Turning transparency into trust
Clear reporting does more than inform; it builds trust. It shows, with evidence, how security is measured, managed, and improved over time.
Evidence-based insight demonstrates due diligence and resilience in practice, not just in policy. It strengthens confidence among boards, regulators, clients, and investors alike.
Achieving that level of clarity can be difficult, especially for teams already stretched for time and resources. A reason why more and more organisations turn to external expertise for independent analysis and continuous improvement.
But the principle stays the same: clarity turns complexity into confidence. Transparent, contextual reporting not only strengthens security posture but also reinforces reputation and trust.
Key takeaways
Effective cyber security reporting turns raw data into actionable insights by contextualising critical and non-critical threats.
Tailored reports address the unique needs of stakeholders, from IT staff to executives.
Partnering with skilled MSSPs enhances threat response and decision-making through expert data management.
Executive reports focus on business impacts and risks, emphasising key indicators and strategic insights.
Top MSSPs continually update their analytics and reports based on evolving threats to maintain relevance.
Transparent reporting boosts investor confidence and reputation by demonstrating a commitment to security.
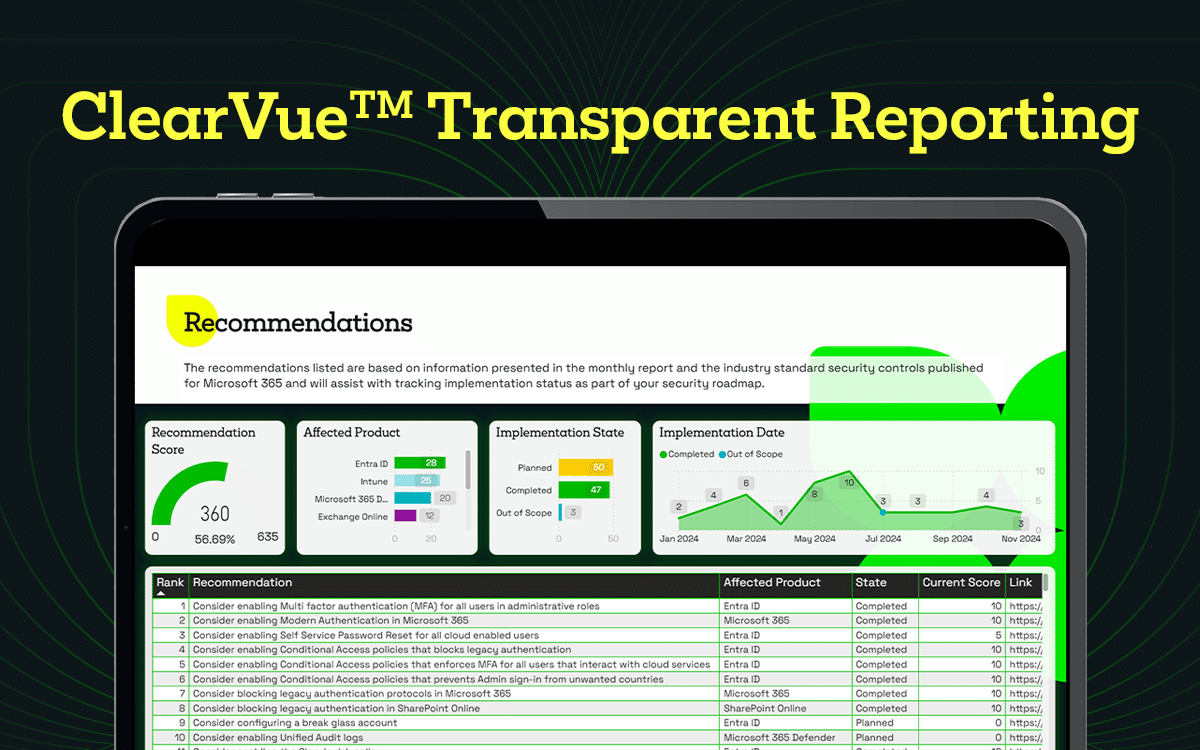
The ClearVue™ effect
At Kocho, we put analytics, reporting, and advice at the heart of our managed security operations.
With ClearVue, we provide our clients real-time visibility across incidents, risks, and performance. Transforming raw data into evidence leaders can act on.
With intuitive dashboards and board-ready reports, ClearVue provides the transparency and assurance today’s organisations need to prove protection, demonstrate progress, and strengthen trust.
Watch the short demo below to see how ClearVue delivers clarity that drives confident decisions.
For more detail, to arrange a full demo, or to talk to us about our managed security operations, please get in touch here.


Free Guide
Turn risk stress into cyber confidence
The SME Guide to Modern Security Operations is a playbook to strengthen cybersecurity without headcount, hassle, or hidden costs.
Inside: SME security stats, ROI proof points, cost comparisons, critical benchmarks, and a roadmap to resilience and cyber confidence.
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier