Discover the threats that our cybersecurity specialists have been monitoring this month, and their advice to keep you safe.
In the news this month:
- Hijacked Chrome extensions put millions of accounts at risk
- Fake CAPTCHAs deploying dangerous malware
- Healthcare data breach in US exposes 1 million patient records
- North Korean hackers use PDFs to hijack devices
- Malware-infected game targets Steam users
Chrome extension attack: 2.6 million users put at risk
A cyberattack has put over 2.6 million users at risk after at least 35 Google Chrome extensions were compromised.
Attackers used phishing emails targeting extension publishers, tricking them into injecting malicious code. This allowed threat actors to steal user access tokens and cookies, risking sensitive account data.
Cyberhaven found that attackers embedded malicious code to communicate with a remote server at cyberhavenext[.]pro, enabling further data theft.

Browser extensions are the soft underbelly of web security. They often have extensive permissions, accessing cookies, access tokens, and identity data.
Fraudulent emails posed as Google Chrome Web Store Support, falsely warning developers of imminent extension removal due to policy violations.
Over 35 compromised extensions have been identified, mainly targeting VPN and AI assistant extensions due to their broad privileges.
Recommendations
The increasing threat from Lumma Stealer malware
Kocho SecOps has detected active instances of the notorious Lumma Stealer malware, which is designed to steal sensitive information and is increasingly distributed through Malware-as-a-Service (MaaS).
Unlike traditional phishing campaigns, Lumma Stealer now spreads via fake CAPTCHA verification pop-ups. Our team has identified multiple content delivery networks (CDNs) hosting these deceptive pop-ups, tricking users into executing malicious PowerShell commands themselves.
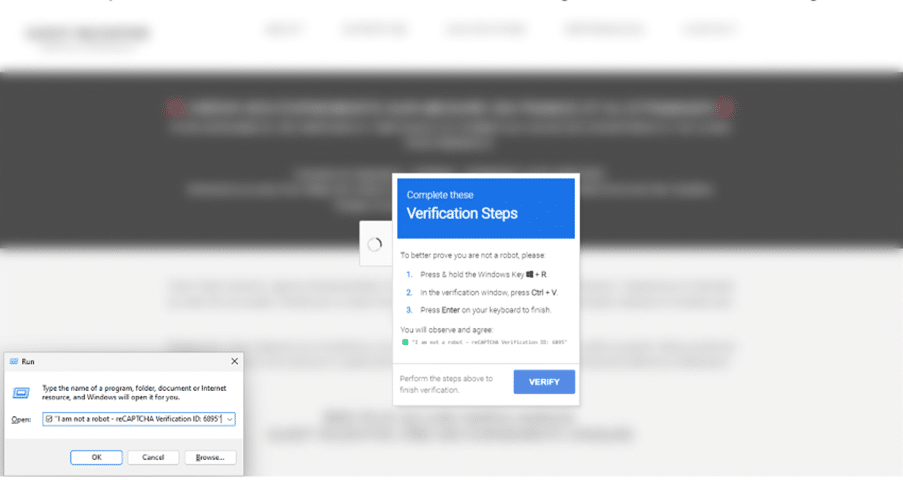
- Once the initial PowerShell command is run, additional malware loaders are activated.
- File-less malware is executed on victim machines, making detection harder.
- Google Chrome credential files are accessed, and registry keys are manipulated.
- The attack appears highly automated after initial user interaction.
Recommendations

Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
Healthcare sector breach: One million patients exposed
A Connecticut-based federally qualified health center (CHC) has disclosed a data breach potentially affecting over a million individuals, including patients and COVID-19 test/vaccine recipients. The exposed data includes:
- Social Security Numbers (SSNs)
- Medical diagnoses, test results, and treatment details
- Insurance information
To mitigate the damage, CHC has:
North Korean hackers exploit PowerShell to hijack devices
The North Korean hacker group Kimsuky is using a new PowerShell-based attack to hijack devices via spear-phishing emails.
Victims are tricked into opening what appears to be a legitimate PDF, but instead, they execute a malicious PowerShell script with admin privileges. This installs a remote desktop tool, allowing attackers to gain control and steal data.
Microsoft has observed this method in limited attacks since January 2025.
Recommended actions:
It’s yet another example of why phishing remains a critical tactic in the cyber attackers playbook, reinforcing the need for organisations and their workforce to remain ever vigilant and continually aware.
Gaming security breach: Steam users targeted with malware-infested game
A recent malware attack on Steam highlights the importance of cybersecurity in gaming. PirateFi, a free-to-play beta game, was found to contain Trojan.Win.32.Lazzy.gen, a malware capable of stealing browser cookies and online credentials.
The game was quickly removed, but around 900 users had already downloaded it.
It’s a vital reminder that a Zero Trust mindset is not just for the workplace, it’s for all digital interactions. And as the lines between work and home blur, any breach can have the power to cause chaos anywhere.
Recommendations for anyone affected:


From our blog
Zombie phishing: The hidden horror lurking in your inbox
Zombie phishing is an email hijacking scam that can cause your organisation nightmares.
Also known as conversation hijacking, it’s a particularly sneaky type of phishing that infiltrates its way into legitimate conversations and uses your own email threads against you.
And it’s a horror story that’s growing in popularity.
Find out why attacks have risen by 70% in the past year and what you can do to stay protected.
Resources & References
Thanks to this month’s contributors from the Kocho SOC team: Joshua Powell, Jack Fisher, Nicci Smart, and Ethan Harris
Stay safe. Stay informed.

Let's talk!
Real partnership. Microsoft expertise. Complete transparency.
Book a free Discovery Call and learn more about our AI-powered security operations service, XDR Rapid Protect.
Get more information on:
- AI-powered rapid protection, from day one
- Dedicated Microsoft experts, by your side
- Powerful, intuitive reporting tools
- Collaboration and transparency as standard

Don't Miss
Great security & compliance resources






















Got a question? Need more information?
Our expert team is here to help.








