We recently talked about the threat Business Email Compromise (BEC) poses to organisations. In this article, we explore the trend of bad actors weaponising legitimate apps like eM client, and the steps we can take to mitigate.
Working in threat detection, we’re always mindful of how perfectly legitimate tools can often be subverted for malicious purposes.
For instance, there have been some notable occurrences of eM Client, a popular email and calendar, being weaponised by threat actors to achieve persistence in a compromised environment.
Let’s start with the basics.
What is eM Client?
eM Client is a comprehensive desktop client for email and calendar management available for Windows and macOS.
Initially launched by a small group of students in Prague in 2007, eM Client grew steadily over the course of the next decade. Still widely used in 2024, the client supports major email platforms like Exchange, Gmail, and Outlook, while integrating with Zoom and Microsoft Teams for online meetings.
How threat actors have exploited eM Client features for BEC attacks
Over the years the client has garnered popularity thanks to its ease-of-use and a series of value-adding features inherent on the platform.
Unfortunately, however, it’s these features that have seen it curry favour among those with malicious intent.
Features exploited by threat actors include:
- Mass Mailing: eM Client’s mass mail feature includes the ability to BCC recipients, effectively hiding the campaign. In the wrong hands, this can be misused for spam campaigns, particularly effective during the free 30-day trial period.
- Invisibility of actions: Users can configure eM Client not to mark emails as read or to store sent emails in the Sent folder. This allows unscrupulous activity to stay under the radar. Making it much harder for compromised users to notice suspicious actions.
- Email exfiltration: eM Client has a built-in email download function that allows the user to download all emails from any accessible inbox, including shared mailboxes. It’s a feature that can be exploited as a potent tool for data exfiltration by threat actors.
Achieving persistence
Achieving persistence in a cloud environment is a novel form of avoiding detection and maintaining a foothold within a target’s estate. Threat actors have been observed in the wild installing eM Client as a means of bypassing multifactor authentication (MFA) requirements in Azure environments.
This has been achieved by threat actors by first compromising a user account, adding eM Client as an Enterprise Application, and then configuring it with the following delegated permissions:
- AccessAsUser.All – This configures eM Client to have the same access to mailboxes as the signed in (and now compromised) user account, via Exchange Web Services.
- Offline_access – This permission allows an application to maintain access to data it’s already been given access to. In effect, the application will continue to receive new session tokens for as long as it’s set to receive them, without user input. Which means that even after access to the compromised user account has been removed, the threat actor would continue to receive, read, and send emails on behalf of the user – achieving persistence.
Mitigation steps
Let’s look at the different approaches you can take to mitigate against this kind of compromise, dependent on if you’re an E5 licence holder or not.
For E5 licence holders
In this scenario, we recommend Unsanctioning the application in Microsoft Defender XDR. You can do this by configuring the following:
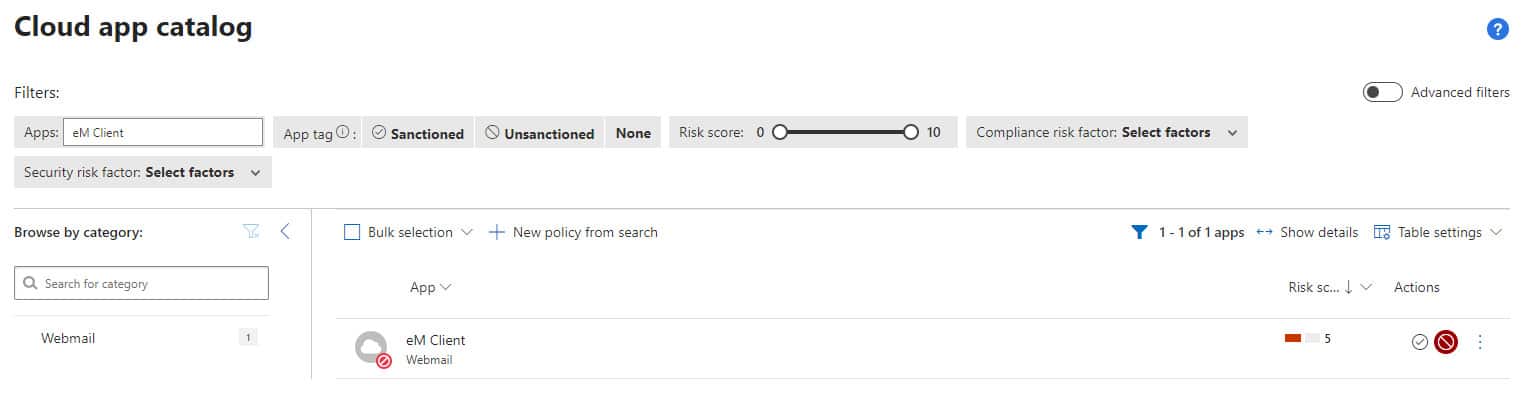
- Log in to your organisation’s Defender portal at security.microsoft.com
- In the Cloud apps blade select the Cloud app catalog section
- In the filters, enter the name of the application: eM Client
- In actions, select “Unsanctioned”
Then:
- Navigate to the “Settings” blade
- Select Cloud apps
- Under Cloud Discovery select Microsoft Defender for Endpoint
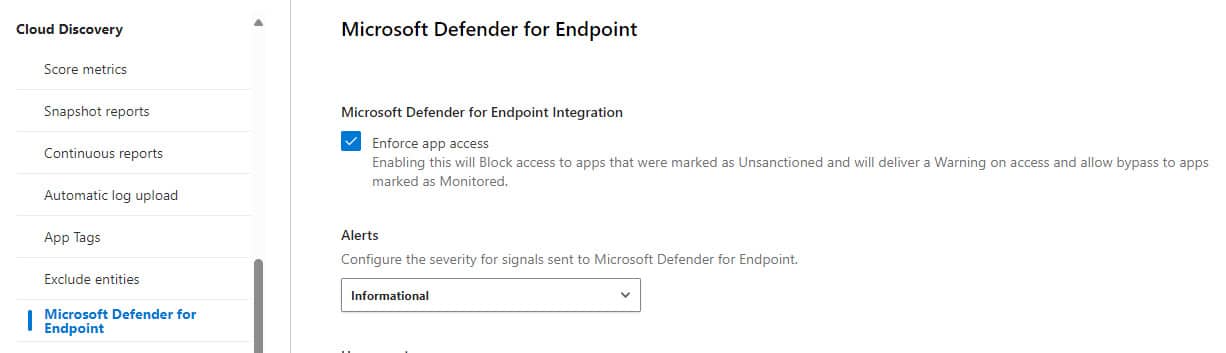
NOTE: Ensure that “Enforce app access” is enabled in the settings, as its description says. Enabling this feature will block access to applications that have been marked as an unsanctioned. Meaning, if a user attempts to access the application they will be issued a warning.
For clients without E5 licences
In this case we recommend the following approach.
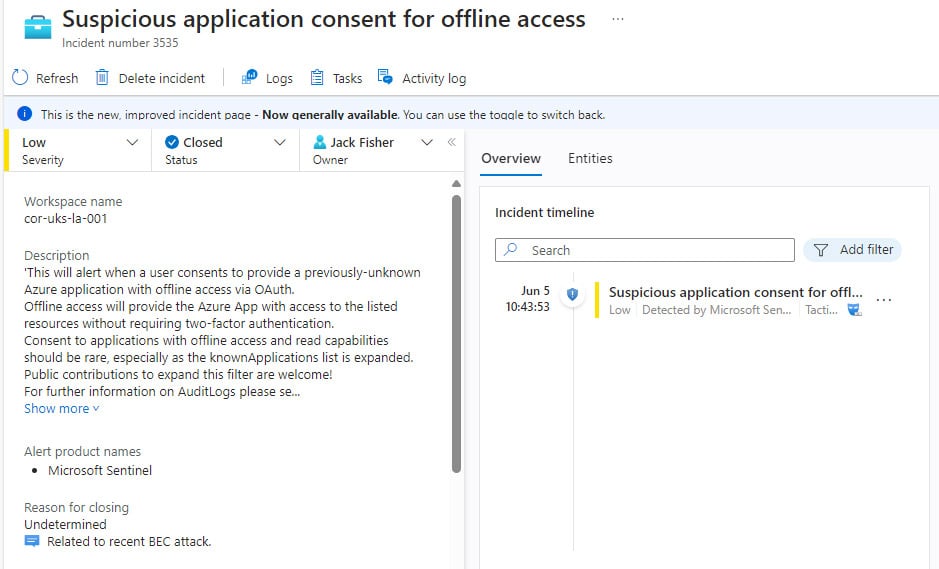
Ensure the Suspicious application consent for offline access analytic is enabled within the estate.
This rule will detect any offline access being granted to an application that has not been seen before, or if it has been marked as unsanctioned in Defender.
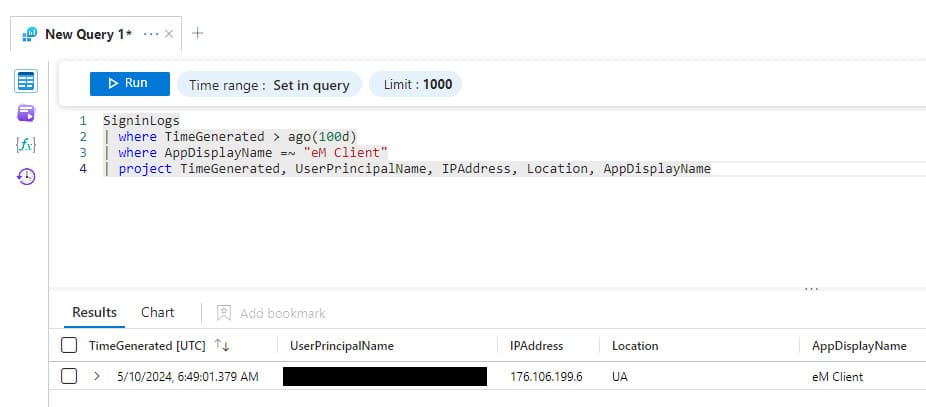
You can also search for authentications via this application with the following KQL:
Conclusion
While eM Client is a robust tool designed to enhance productivity and communication, its features can also be exploited by cybercriminals to carry out sophisticated attacks like BEC.
For this reason, we urge organisations to be vigilant and proactive in employing security measures to mitigate these risks. Something that can be effectively achieved via the advanced tools from within your E5 licence and Defender XDR. Or through a more manual process if you don’t hold an E5 licence.
Ultimately, the key to defending against weaponised legitimate applications is continual awareness across your estate, and ensuring your security settings are accurately configured.
Key takeaways
Feature exploitation: eM Client’s mass mailing, action invisibility, and email downloading features can be manipulated for malicious purposes.
Achieving persistence: Threat actors use eM Client to maintain control in compromised systems by exploiting specific delegated permissions.
Bypassing security: eM Client is installed as an enterprise application to circumvent multifactor authentication in cloud environments.
Mitigation for E5 licence holders: E5 users should use Microsoft Defender XDR to unsanction eM Client, blocking access and issuing user warnings.
Mitigation for non-E5 licence holders: Non-E5 users should enable analytics to detect and respond to suspicious application consents.
Proactive security measures: Organisations must maintain continual vigilance and properly configure security settings to defend against weaponised applications.
Want to know more?
If you’d like to understand more about how Kocho SecOps detects and responds to this behaviour, reach out to our team for a detailed consultation. Our expertise in managing and mitigating BEC attacks can help safeguard your organisation against ever-evolving, always improving cyber threats.
And please join our mailing list for the latest cyber security news, technology updates, and regular tips to keep protected against advanced threats.


Free Guide
The Ultimate Guide to Microsoft Security
The most comprehensive guide to Microsoft Security. Over 50 pages. Microsoft licensing and pricing simplified.
Discover technologies that:
- Detect and disrupt advanced attacks at machine-speed
- Tap into the world’s largest threat intelligence network
- Protect identities, devices, and data with ease
Next steps
Like this guide? Then don’t forget to share it with your followers.

Great protection starts here
Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
You’ll get:
- Notifications of critical vulnerabilities
- Recommendations to reduce your risk level
- Expert advice to defend against new threats
























Got a question? Need more information?
Our expert team is here to help.








