This month’s highlights range from mitigation advice for new Microsoft vulnerabilities to account takeover risks and nation state extortion tactics from North Korea. Read on for the latest updates and tips to keep your systems safe.
In the news:
Unusual UserAgents drive surge in account takeovers
Critical Windows flaw enables code execution
North Korean IT workers extorting global organisations
Outlook vulnerability enables malicious email attacks
Surge in unusual UserAgents linked to account takeovers
The Kocho Security Operations Centre (SOC) has detected a rise in account takeovers involving unusual UserAgents during successful malicious logins.
We’ve identified attackers leveraging UserAgents such as Axios, a popular JavaScript HTTP client, to automate sign-in attacks like credential stuffing or brute force attempts.
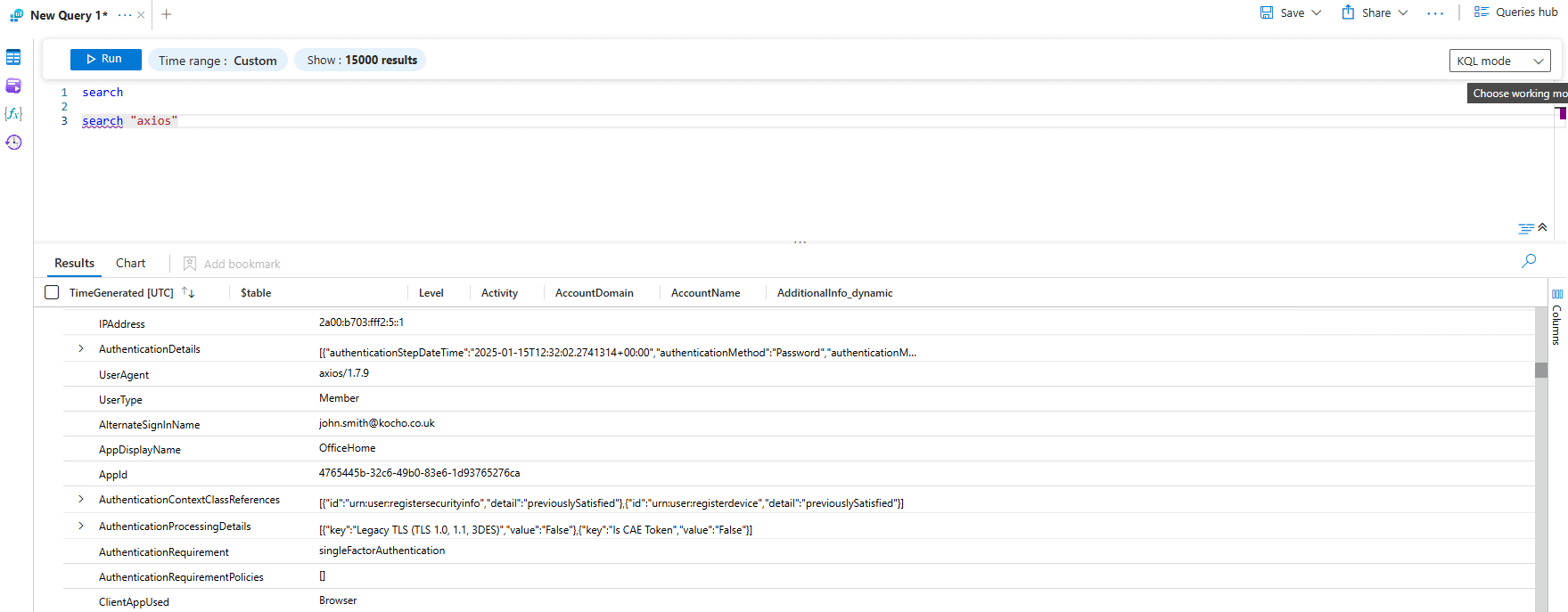
Our analysts also note that these attacks are often paired with access to services like OfficeHome, advising that detection capabilities can be increased by pairing both within a KQL query.
Additional suspicious UserAgents like “curl” and “Python” have also been observed during malicious activity. Expanding detection queries to include these UserAgents can offer broader coverage and improved incident response.
Recommendations
Critical Windows vulnerability requires immediate attention
Microsoft has disclosed a high-severity vulnerability (CVSS 7.8) impacting Windows Server 2025, Windows 10, and Windows 11, which could allow attackers to execute arbitrary code with elevated privileges.
A proof-of-concept exploit has been released, targeting a flaw in Windows Registry memory management.
Microsoft has released security updates, including KB5036980 Preview and KB5037771, to address the flaw.
We strongly urge all clients to apply these patches immediately and review their access controls, audit protocols, and user training to enhance defences.
Recommendations
Refer to Microsoft’s advisory (CVE-2024-43641) for detailed guidance.

Keep pace with the latest security threats
Sign up to receive the latest threat intelligence articles and reports from our SecOps team.
FBI warns of North Korean IT workers extorting employers
The FBI has issued a warning about North Korean IT workers posing as remote freelancers to infiltrate businesses, steal proprietary data, and extort employers.
Refusal to pay often results in the public release of sensitive information.
A statement on the FBI websites says:

After being discovered on company networks, North Korean IT workers have extorted victims by holding stolen proprietary data and code hostage until the companies meet ransom demands. In some instances, North Korean IT workers have publicly released victim companies’ proprietary code.
These workers, using forged identities, target organisations in the US, Europe, and East Asia. Their earnings, which fund the North Korean government, are increasing as tactics evolve to exploit remote work.
Security researchers have reported a rise in insider attacks and data exfiltration from platforms like GitHub. Recent indictments revealed that five individuals generated over $866,000 for North Korea through these schemes.
Recommendations:
Microsoft Outlook vulnerability
A critical vulnerability (CVSS 9.8) in Microsoft Outlook was disclosed on January 14, enabling attackers to remotely execute code on a victim’s device without user interaction.
The flaw exploits Windows Object Linking and Embedding (OLE) functionality, allowing malicious emails to trigger the vulnerability simply by being opened or previewed in Outlook.
Recommendations
Microsoft has released a patch to address the issue, but until it’s applied, the following mitigations are recommended:
Ensure systems are updated immediately to reduce exposure to this low-effort, high-impact attack vector.
For more detail about the vulnerability and links to patches, visit the Microsoft security information page here.
From our blog: Why SOCs need to move out of their silos
Cyber criminals are waging a new kind of war, but too many SOCs are still fighting yesterday’s battles.
Modern attackers thrive by exploiting the interconnected nature of systems, using graph-based strategies to outsmart defenders.
Yet, many SOCs are stuck in outdated, siloed approaches that leave critical gaps ripe for exploitation.
To stay ahead, they need to adopt their adversaries’ playbook. Shifting from fragmented defences, to unified, proactive strategies.
So, what’s holding them back?

Let's talk!
Real partnership. Microsoft expertise. Complete transparency.
Book a free Discovery Call and learn more about our AI-powered security operations service, XDR Rapid Protect.
Get more information on:
- AI-powered rapid protection, from day one
- Dedicated Microsoft experts, by your side
- Powerful, intuitive reporting tools
- Collaboration and transparency as standard

Don't Miss
Great security & compliance resources

Microsoft Security Roadshow
Demos and expert insight to help you get the most from Microsoft's identity, security and cloud solutions.

Purview Demo: Securing data in the age of AI

Cybersecurity a year in review: What happened in 2025, and what it means for your 2026 security strategy

How to achieve cost-effective threat visibility with Microsoft Sentinel data lake






















Got a question? Need more information?
Our expert team is here to help.




