
Blog | 5-minute Read
Azure AD B2B vs B2C: What are the key differences between Microsoft’s external access products?

Marcus Idle
Head of External Identity
Published: 16 May 2022
Deciding which external access solution meets your needs can be a challenge, so let’s explore what Microsoft’s Azure AD B2B and B2C products offer, where they crossover, and where they differ.
The management of external identities has changed a great deal in recent years, with Microsoft‘s approach being no exception.
If you‘re reading this blog, you‘ve likely come across the two products Microsoft uses to facilitate external access, Azure AD B2B and Azure AD B2C.
On the surface, it would seem self-explanatory that B2B is used to provide access to partners and suppliers whilst B2C caters to customer-facing interactions.
Like much of life, however, things are never so clear cut. Azure AD B2B and B2C may have begun life intended for these purposes, but there‘s an increasing amount of crossover in their application.
This can make things difficult for when it comes to selecting the right technology choice for your scenario. In this blog, I shall attempt to clarify the differences between the two and highlight how they can best serve your external access needs.

The Ultimate Guide to External Identity Success
A 7-step plan to achieve seamless user access, the highest levels of security, and unrivalled user experiences.
Azure AD B2B and B2C explained
So, how does Azure AD B2B work?
B2B (or ‘Azure AD B2B collaboration’) addresses the problem of sharing your applications with external users and is a feature of Azure AD rather than a standalone service.
These users could be suppliers, customers, partners, or any kind of external user with whom you wish to collaborate.
In the past, you may have just created a user account on your corporate Active Directory (i.e. a ‘local account’) to invite an external user to use a web application. Or, if you have ADFS infrastructure, you may have established a trust relationship between your ADFS server and your partner’s.
The local account solution is an easy fix – but it comes with a housekeeping problem. When the external user leaves, you may not be notified immediately (or at all) of their departure – which means they could retain access even when they should not have it.
The ADFS solution is a neater one – but is complex and requires all of your partners to have a similar solution and to set up trusts between each organisation.
In response, Microsoft created Azure Active Directory B2B, where you simply invite a user by email to start the ball rolling:
- The user receives an email with a link to accept the invitation.
- The authentication happens in the right place (at the user’s organisation).
- The trust relationship is established in the background – without any new hardware or configuration.
- Credentials stay in the guest directory.
- Access control is managed in the host directory.
You can onboard users in four main ways – simply pick the model that best suits your relationship with the external users:
- Individual email invitation.
- Access packages (individuals apply for and are granted access via an approval process).
- Self-service User Flows (Individuals apply for access via an automated verification process).
- Bulk invite via CSV upload.
There are many advantages of using B2B to invite guests into your organisation:
- You can place guests into the same groups as your employees to manage access to resources.
- You can invite users and bundle up access using access packages (via an Azure AD feature called ‘entitlement management’).
- You can control and review access with Azure AD’s conditional access and access reviews.
- You can easily create ‘terms of use’ that your guests must accept before they gain access.
What is Azure AD B2C?
Azure AD B2C provides a security and authentication solution for your outward-facing applications and is independent of your corporate Azure AD.
The actual authentication process works in a very similar way to B2B. But B2C is not designed to allow access to your employee groups and other resources, as it is primarily intended for end customers.
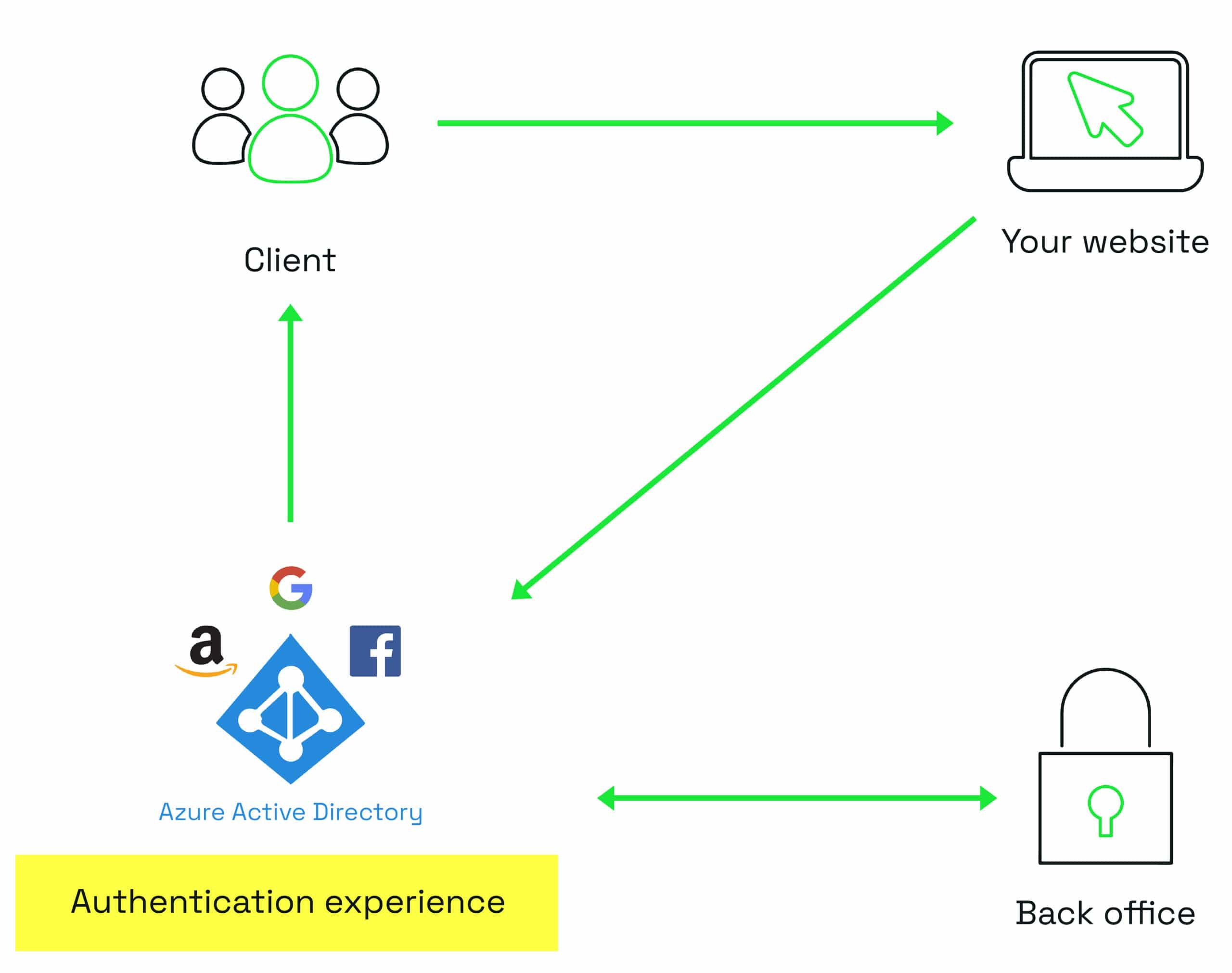
B2C provides complex user flows (known as custom policies). This feature allows you to have multi-step sign-in experiences, which can be useful for providing or verifying attributes.
For example, with one of our insurance company clients, existing customers with no online relationship with the company needed to be able to sign up to the website and see their documents.
To make this happen, B2C needed to verify the customer’s identity using an API call during sign up.
After accepting the terms and conditions, the customer submits their account number and a one-off ‘activation code’. Providing these two items allows the policy to check their identity.
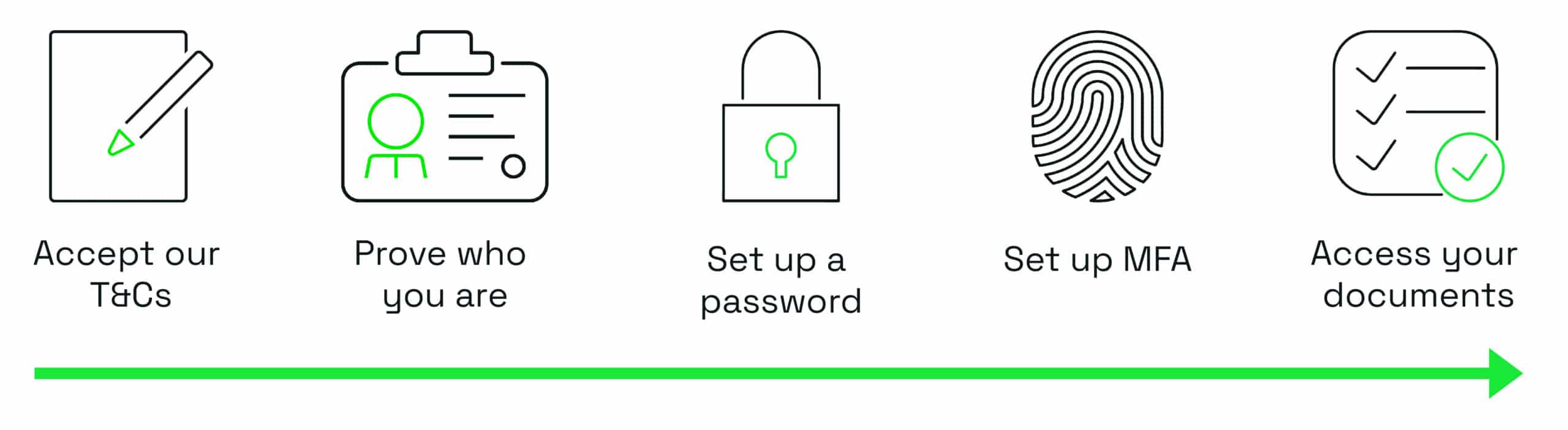
The policy sends the data to a web service (API) external to B2C and receives a response which tells it whether the user is indeed a customer.
At this point, the customer can now continue to set up their credentials, complete the sign-up process, and access their documents.
Azure AD B2B and B2C compared
Below I’ve put together a comparison of the two products against some typically required features:
Azure AD B2B |
Feature |
Azure AD B2C |
|---|---|---|
To enable collaboration using Microsoft 365 apps and authorise users from partners and suppliers regardless of the identity provider. |
Primary use |
To support customer (consumer or business) transactions through customised applications. |
Employees and partners with work or school accounts. Can also use any email address for partners. |
Identity types supported |
Customers with local app accounts (email and username) and any supported social identity through direct federation. |
In the same directory as your employees. Can be added to the same groups and apps. |
Where are identities managed? |
In the B2C directory, separate from your, or any partner, directories. |
Yes, to all Azure AD connected applications. |
Single sign-on (SSO) support? |
Yes, to customer-owned apps within the Azure AD B2C tenant. SSO to Microsoft 365 apps is not currently supported. |
Managed by the host/inviting organisation. Azure AD also provides access reviews as part of its Identity Governance offering. |
Lifecycle management |
Customer self-serve – or can be managed by the application. |
Managed by the host/inviting organisation (this is where you can apply conditional access policies, etc.). |
Security and compliance policies |
Conditional Access can be implemented in B2C and actions taken are determined by risk level. |
The host organisation’s branding will be applied to set items such as logo and background. |
Customisation and branding |
B2C customisation is completely flexible – the host organisation has full control. |
Supported and easy to use Office 365 tools and applications. |
Integration with Office 365 |
Not at present – possible through a hybrid scenario with Azure AD B2B. |
Microsoft has now introduced an API integration. |
Complex journeys |
B2C’s flexibility allows for journeys to be created to fit any requirement. |
Supported through access packages. |
Sign up and approval |
This can be enabled through custom policies. |
At time of writing, B2C offers some features that B2B does not have:
- Out-of-the-box integration with a wide range of identity providers including MSA, Amazon, and more: B2B only offers out-of-the-box integration with Google accounts and Facebook accounts.
- Custom policies with multiple steps: B2B offers journey steps but in a more limited way – for example, you can call an external API but at the moment you only have two choices about when to call it.
Convergence
However, Microsoft is rapidly developing new capabilities for B2B.
Recent additions to Azure Active Directory include:
- Additional attributes
- Custom page layouts in user flows
- API connectors (ability to call an external API during a user flow)
So, what we’re seeing is a trend of convergence between the two products. The restriction of having to choose B2C if you want a customised look and feel no longer applies.
This means that these two products are increasingly venturing beyond the confines of their original B2B and B2C remits. It’s more about deciding on the functionality you require and selecting the product that suits you best, regardless of whether it’s a partner or customer access scenario.
I wouldn’t be at all surprised if Microsoft were to eventually do away with the B2B and B2C labels. As these two products become ever more entwined, they’ll act as a single external access management suite.
Key takeaways
Don’t let the B2B and B2C labels mislead you – focus on the functionality.
Both products benefit from industry-standard protocols and world-class security features.
Azure AD B2C has the most flexibility, but B2B is catching up.
Increasing crossover and hybrid deployments will likely open up more features in future.

The Ultimate Guide to External Identity Success
A 7-step plan to achieve seamless user access, the highest levels of security, and unrivalled user experiences.
Next steps

Great emails start here
Sign up for free resources and exclusive invites
Subscribe to the Kocho mailing list if you want:
- Demos of the latest Microsoft tech
- Invites to exclusive events and webinars
- Resources that make your job easier



























Got a question? Need more information?
Our expert team is here to help.






